Best Laptop High process Review
With precision crafted metal frame design, refined performance and Windows 10 built in, it’s the smart choice for your business. With precision crafted metal frame derefined performance and Windows 10 built in, it’s the smart choice for your business.With precision…














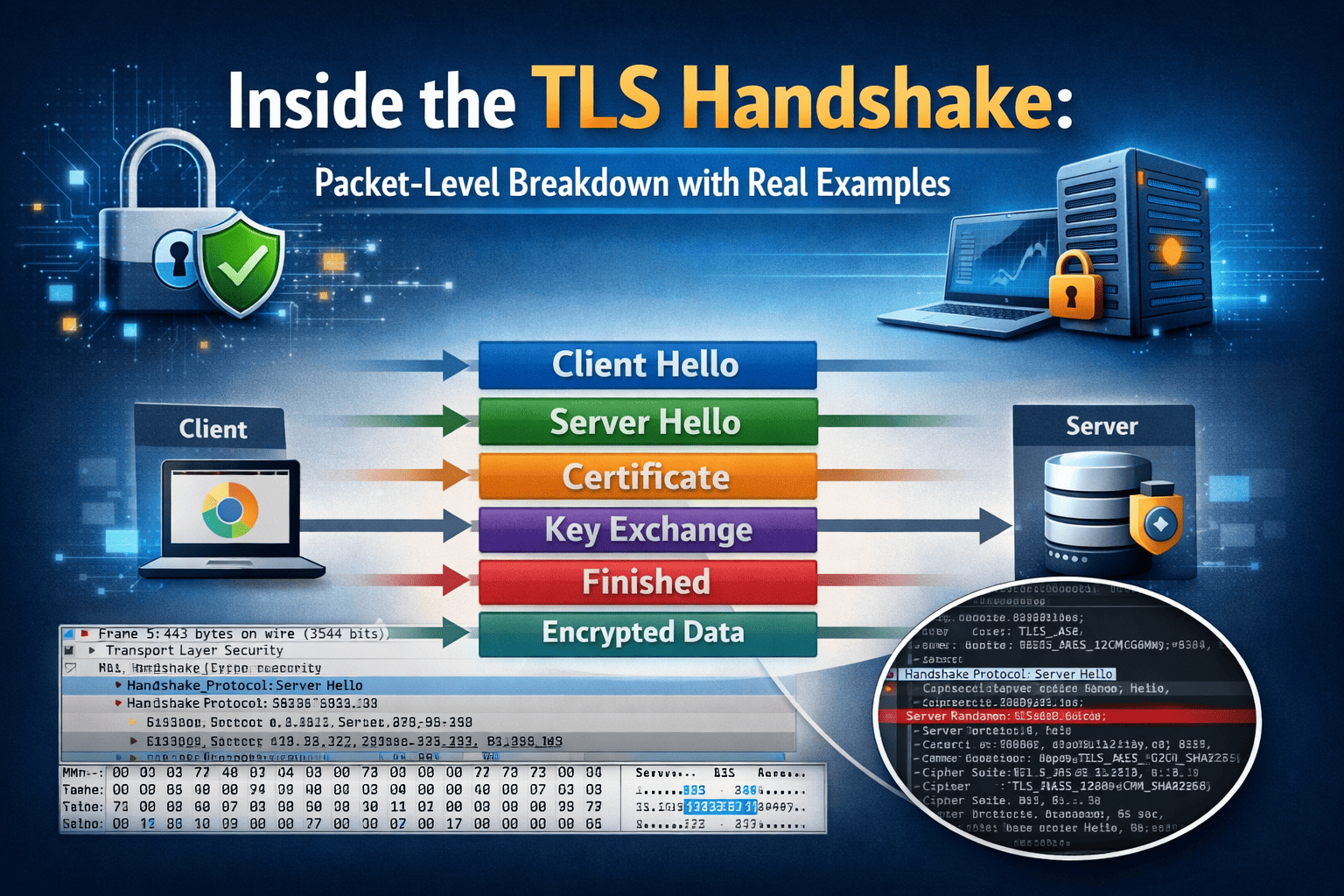
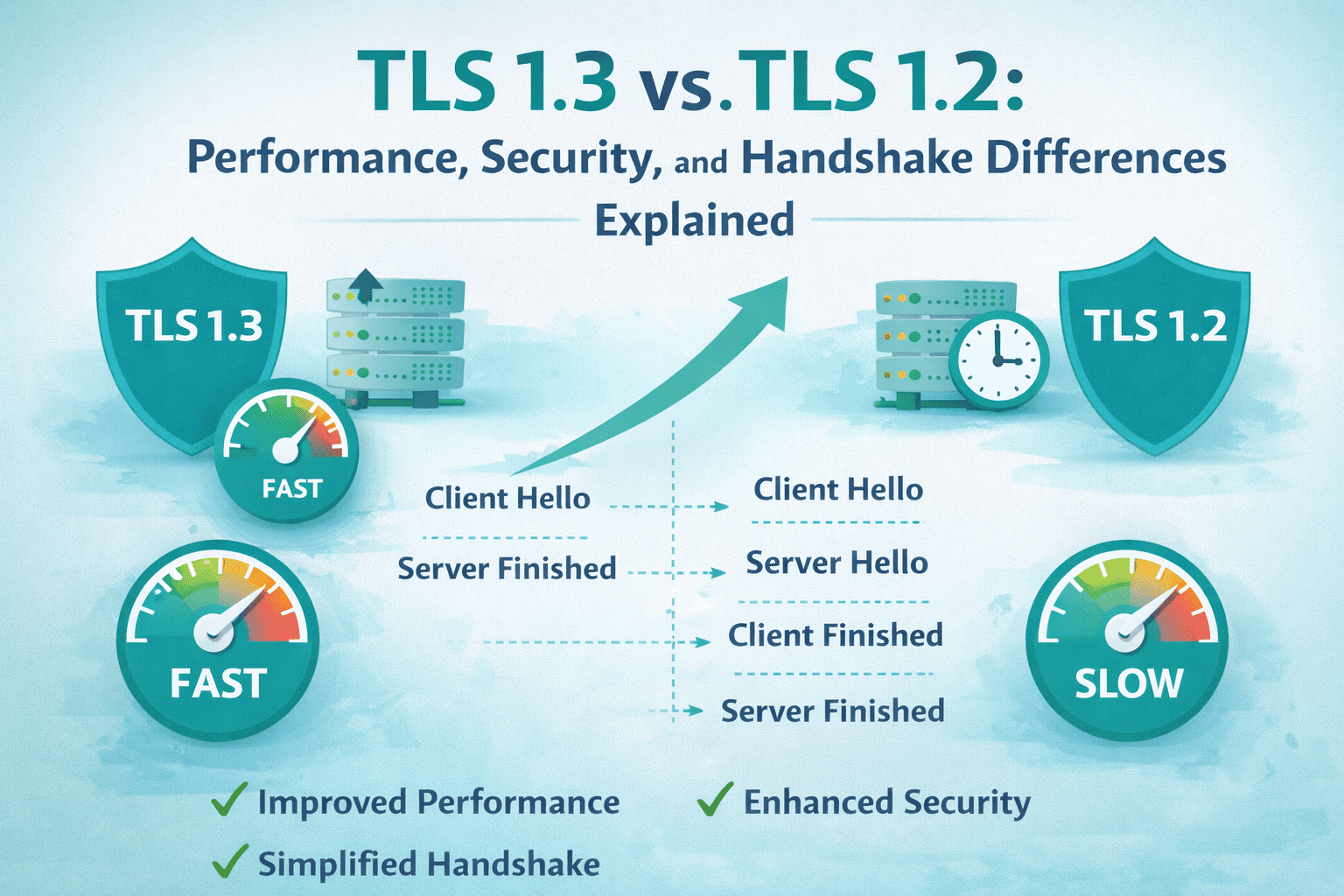

































![GlobalSign SSL Promo Codes, Discounts, Coupon Code & Deals [Updated 2026]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/GlobalSign-SSL-Promo-Codes-Discounts-rhsqbp2nrzjzfdc7a5m4iag114p7kmgjfp59ckgqv4.png)
![GeoTrust SSL Promo Codes, Discounts, Coupon Code & Deals [Updated 2026]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/GeoTrust-SSL-Promo-Codes-Discounts-rhsqbn6zebhes5exl4svdax3ucyh5892rfuae0jj7k.png)
![Comodo SSL Promo Codes, Discounts & Deals [Updated 2026]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/Comodo-SSL-Promo-Codes-Discounts-rhsqbp2nrzjzfdc7a5m4iag114p7kmgjfp59ckgqv4.png)
![GoDaddy SSL Promo Codes, Discounts & Deals [Updated 2026]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/GoDaddy-SSL-Promo-Codes-Discounts-Deals-rhsqbhjy9b9ouhn4i2d3yccca1q9v1moqnxdicrw8w.png)




























![GoDaddy Wildcard SSL Promo Codes, Discounts & Deals [Updated 2026]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/20250708_2315_SSL-Promo-Deals_simple_compose_01jznj6ehqe53sf59cemgc4f05-rhsqbm957hg4gjgaqme8st5n8z33xj5cfb6swqkxds.png)






























































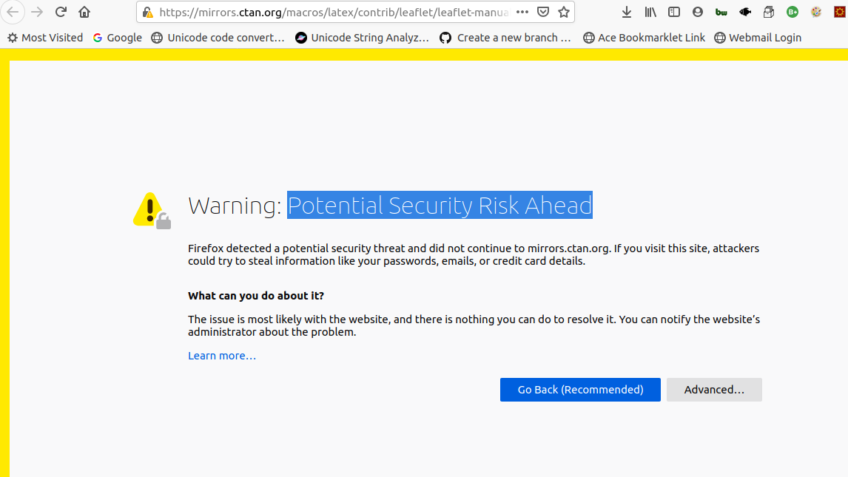





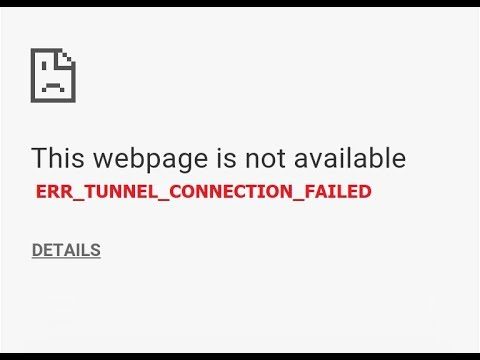
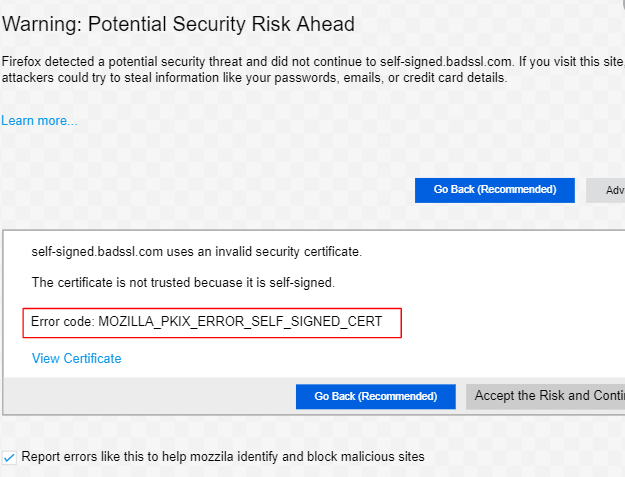
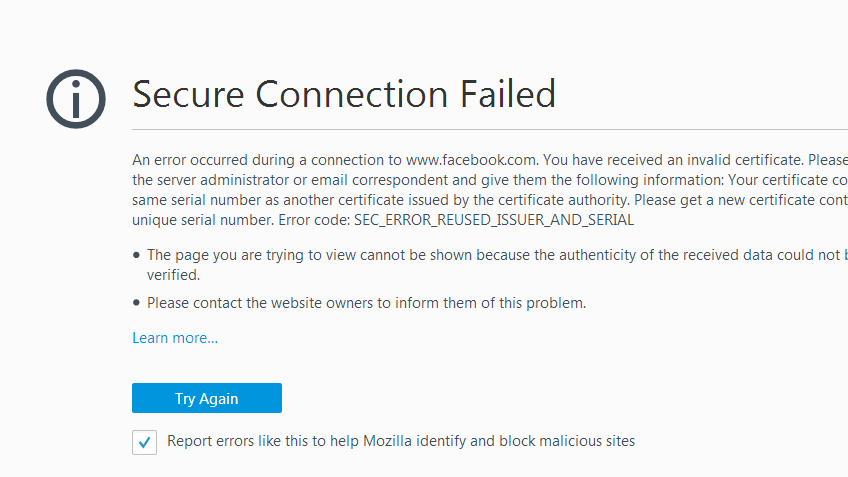

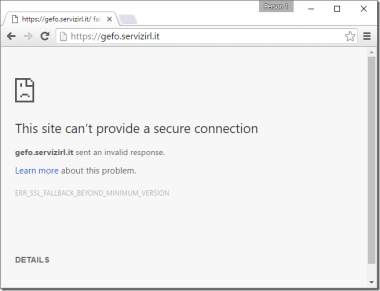
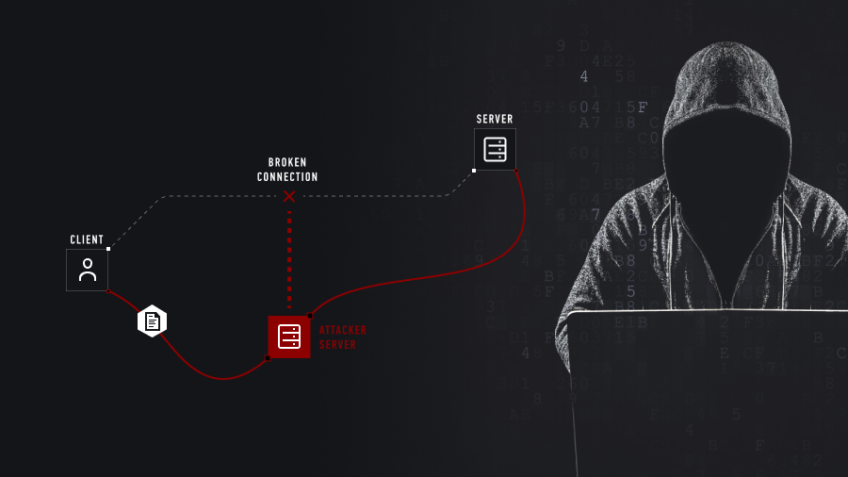




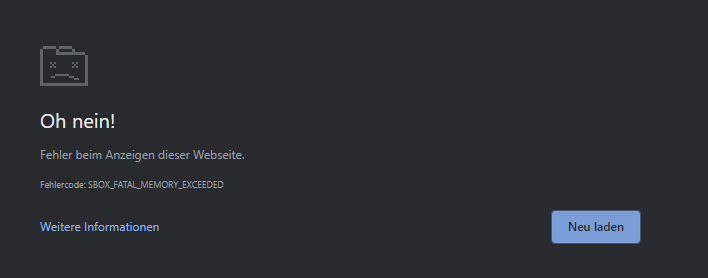
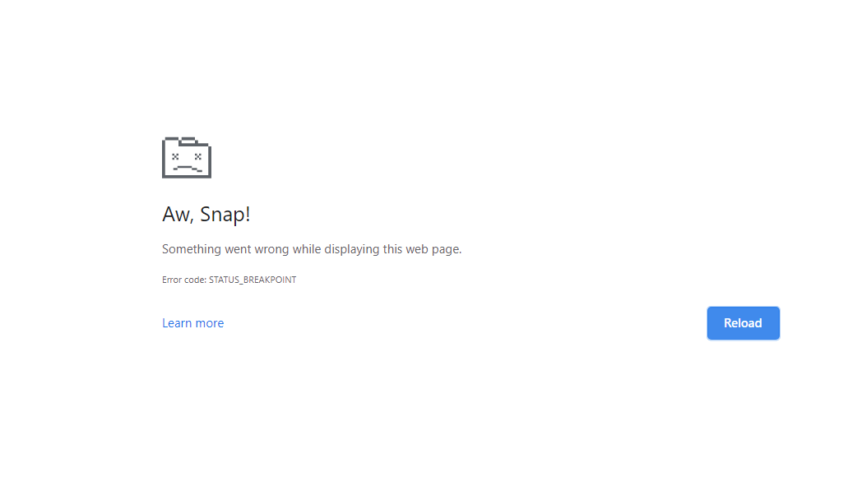




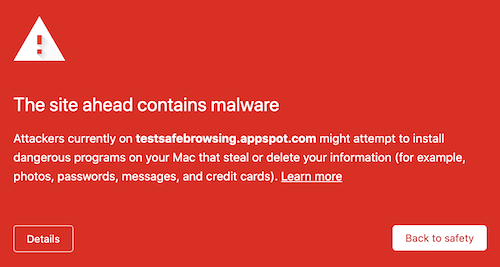


![How to Fix Google Chrome Won’t Open Load Problem [Tutorial]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/Fix-Google-Chrome-Wont-Open-Load-Problem-rhsqbbwx4b1ywtvbezxcjdrkpqi2kv0apw0gmp09a8.webp)