FAQs What does “Invalid URL” mean in Chrome? An “Invalid URL” error in Chrome usually means the address you entered is incorrect, the page has been deleted or moved, the URL is incomplete, or it contains illegal characters or[…]
Archive: Category: Website Security
How to Secure AI Agents: Best Practices for AI Security
Artificial intelligence is no longer limited to static models that generate answers on demand. The rise of AI agents — systems powered by large language models and other AI technologies that can act autonomously to perform tasks, make decisions, and[…]
Top 10 Healthcare Cybersecurity Trends in 2026
The healthcare industry has always been a critical pillar of society, but in recent years, it has undergone rapid digital transformation. From electronic health records (EHRs) to telemedicine, the integration of digital tools has made healthcare more efficient, accessible, and[…]
Mobile cyberattacks in 2026 have escalated to record levels. Smartphones have evolved into full digital identities — storing authentication tokens, financial credentials, biometric data, cloud access, and communication histories. This has transformed mobile devices from simple communication tools into one[…]
In today’s hyper-connected digital economy, cloud security refers to the strategies, technologies, and policies used to protect data, applications, and infrastructure hosted in cloud environments. This includes safeguarding against threats like unauthorized access, misconfiguration, data leaks, and ransomware within platforms[…]
Generative AI has moved from experimental to essential in just a few short years. In 2025, it’s no longer a futuristic concept—it’s powering everything from personalized marketing and automated code generation to synthetic media, customer service, and product design. As[…]
Active and Passive Network Attacks: Key Differences
The two types of attacks that can occur in network security are passive and active attacks. An attacker attempts to change the messages’ content during an active attack. An attacker duplicates the communications while observing them in a passive attack.[…]
Best Methods of Gaining a Stable and Secure WiFi Network
In the modern era, life seems to come to a standstill without a stable WiFi connection. As a result of extensive wifi usage all over the world, the number of hackers trying to gain access to your network has also[…]
Malware Scanning: How to Scan Your Devices for Viruses?
What is Malware? A ‘malware’ (contraction for ‘malicious software’) is a program that is specifically created for malicious intent. When these software programs enter your device, it causes disruption and destruction of your files. They may also gain unauthorized[…]
What does the term network firewall mean? Intranets in particular are protected by network firewalls, which are security tools intended to prevent or lessen illegal access to personal networks linked to the Web. Firewall policies specify the only traffic that[…]
Ways to Implement DMARC for Your Business
What is DMARC? DMARC is an abbreviation for “Domain-based Message Authentication, Reporting & Conformance”. It is essentially a security protocol that is required by business organizations before they can apply for a Verified Mark Certificate for their email. It contains[…]
The ERR TOO MANY REDIRECTS Error and How to Fix It?
HTTP 408: How to Fix the Timeout Error?
Last updated: Oct 12, 2025 Website errors can frustrate users and hurt your search rankings. One of the most common — yet often overlooked — issues is the HTTP 408 Request Timeout error. This error typically occurs when a client[…]
Tips to Avoid Common Shopify Mistakes
Shopify is an online merchandising platform, for people who have long to start their own business, this platform provides you the opportunity to begin merchandising your products to your customer through an online platform too. It has all the features[…]
How to Avoid Technical Errors on Wix?
Whenever we think about starting a website, our thoughts are generally clouded with issues of learning coding to create a website. But what we forget is that we are living in the 21st century and you do not need the[…]
Tips To Resolve and Avoid WooCommerce Errors
Wouldn’t it be amazing if you could turn your blog site into an online store too? Well, you could avail this opportunity by just using the WooCommerce plugin on your WordPress site. Its affinity in working with WordPress makes it[…]
“There is an error processing your Request” on Magento
Before learning how to debug this error, let us know a little about “What is Magento?”. Well, magneto is the eCommerce platform. It is responsible for helping you create an online store and sell your merchandise to the world. It[…]
Common Errors in WordPress (And Ways to Fix Them)
Errors are basic interruptions that you come across while browsing on internet sites. But there is a solution to every error occurring. Sometimes, there are small errors that can easily be resolved and sometimes there are complicated errors, which either[…]
“Error Establishing a Database Connection” in WordPress
In one way or another, you will come across this while browsing on WordPress. Well, today we gonna know how to fix this. Before undoing this error, we need to unveil quite a few possibilities causing this issue and in[…]
How Email Encryption Works in Outlook?
Security is our primary requirement while sharing confidential emails. These emails could vary from HITECH, HIPAA, and FERPA to GDPR. Data is stockpiled in these emails and their privacy and security can be maintained by encrypting the email so that[…]
Everything You Need To Know About – .Com Vs .Net
We all once in our lives stumble upon the thought of creating our own websites. Well, there are billions of things that we need to keep in mind while creating one. And it here where we all need to make[…]
Report About Hard Drive & Ways to Destroy It?
If you google How to Destroy a Hard drive, you will encounter a number of ways from setting it to fire or demagnetizing it to How to technically destroy it. But if I were to answer that, the best way[…]
WHAT IS OCSP STAPLING?
OCSP Definition OCSP Stapling is one of the methods to check the revocation of the SSL/ TLS Certificates provided by the CA(Certificate authorities) in order to provide your users a better experience of your website and also make your website[…]
Hashing Algorithm: Applications and Working
When our work is organized, it gets easier and also it takes us less time to complete it. Just like that when our data is organised in a certain manner it becomes easier for the system to work efficiently. That’s[…]
Guide to Analyze and Avoid Malicious URLs
Internet is a vast platform that provides us the opportunity to connect with people, exchange our data besides it also helps us in exchanging our encrypted credentials around billions of websites and also helps us to connect to billions of[…]
WordPress White Screen of Death and How Can You Fix it?
The white screen of death is a WordPress error that is very common among WordPress users and has been a persistent problem haunting WordPress users since the platform was created. You, too, might be facing this error, but do not[…]
Two Factor Authentication? 2FA Defined & Explained
Are you curious about two-factor authentication and multi-factor authentication definition? So, What is two-factor authentication and for what reason is it utilised? The Two-factor authentication definition sometimes alluded to as two-step authentication or double factor validation, is a security interaction[…]
Best Ways to Fix the Critical Error in WordPress
Is it true that you see the critical error on your WordPress site? WordPress may sometimes show you a message that ‘There has been a critical error on this website. Kindly browse your site administrator email inbox for directions’. It[…]
WHAT IS PENETRATION TESTING? A COMPLETE GUIDE EXPLAINED
Are you curious about Penetration testing? Then you have come to the right place to get the answers to your curiosity. Below is everything you need to know about penetration testing, as well as the penetration tools used for such[…]
What is Ryuk Ransomware? How Does Ryuk Ransomware Work?
Are you curious about the Ryuk Ransomware? Then you have come to the right place to get the answers to sate your curiosity. Below is everything you need to know about the yuk ransomware and its works. What is Ryuk[…]
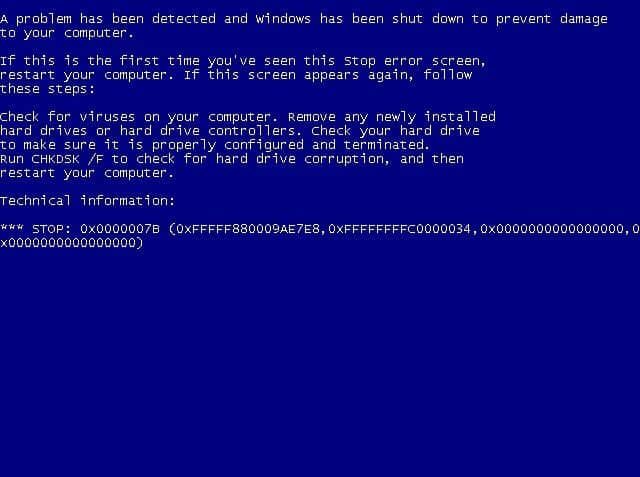
How to Fix Blue Screen of Death 0x0000007B?
It is exceptionally irritating to meet the stop blunder 0x0000007b when you boot your PC, and this mistake is regularly joined by Blue Screen of Death. Be that as it may, fortunately, this post presented by MiniTool Solution has assembled[…]
Difference Between Digital Signature and Digital Certificate
People get a little confused between a digital signature and a digital certificate because both of them provide security measures and sound similar. This might be the reason that people think both of them are similar. The computations that are[…]
What is a Brute Force Attack & How to Prevent It?
Brute force attacks do not rely on the website’s vulnerabilities but bad actors may use other tactics. It becomes easy for the hackers to guess the credentials because these attacks make the websites weak and hackers can extract the data.[…]
How to Protect Your Website from WordPress Brute Force Attacks? No website is safe and the bitter truth is that your website might be under a brute force attack. The most common WordPress attack is a brute force attack. When[…]
What is Internet Cookies? A Complete Guide
Last updated: Nov 2, 2025 Every time you visit a website, browse products, check your email, or log into a service, small files known as internet cookies are quietly working behind the scenes. These cookies help you stay logged in,[…]
How do lava lamps help with Internet encryption?
Last updated: Nov 2, 2025 When it comes to internet security, randomness plays a surprisingly critical role—one that’s often overlooked by non-specialists. To understand why lava lamps are being used to help encrypt traffic on the internet, it’s essential to[…]
How to protect your Social Security number: 10 SSN tips?
How to protect your Social Security number: 10 SSN tips? If you want to protect your website against identity theft, then start by protecting your website with a social security number. The high-value target for the IF theft is your[…]
What is an SSL Certificate Outage Error? A Complete Guide
In today’s digital world, websites rely heavily on SSL (Secure Sockets Layer) certificates to secure data transmitted between users and the website. SSL certificates are essential for ensuring secure communications, protecting user information, and building trust with visitors. However, an[…]
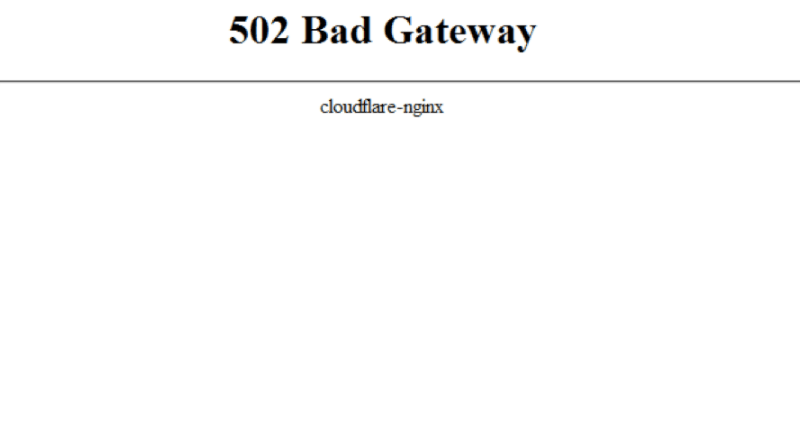
How to fix the 502 Bad Gateway error? There are several errors you will face if your server doesn’t respond well. Here’s a similar error of 502: Bad Gateway error that we are going to know about and find[…]
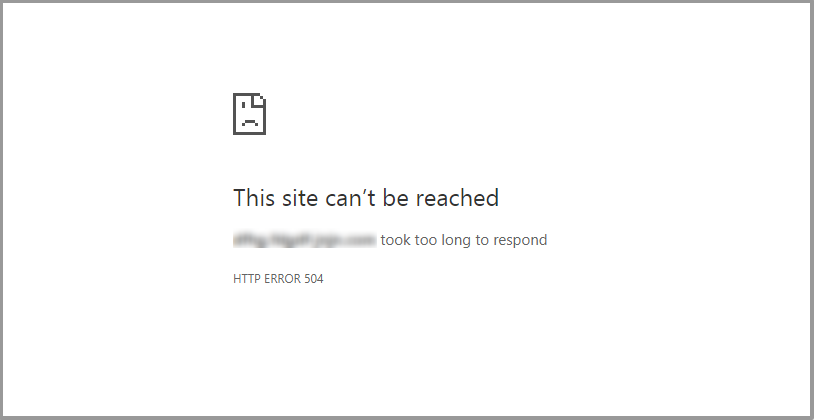
How to Fix the 504 Gateway Timeout Error?
A 504 Gateway Timeout error occurs when a server acting as a gateway, proxy, CDN, or load balancer does not receive a timely response from an upstream server it depends on. Your browser successfully reaches the gateway, but that gateway[…]
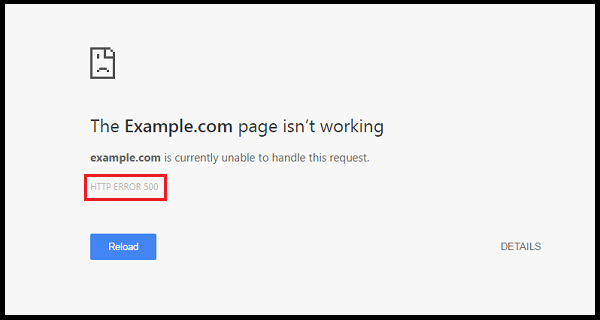
How to fix 500 internal server error?
How to fix the 500 Internal Server Error? There are numerous websites on the server which might not be working or might be outdated. The development of the websites frequently faces the issue of 500 Internal Server error and the[…]
Websites running on a server can attract several numbers of people to the website and create traffic. This makes the website earn money and brings the website to the top in the SEO. The more traffic in a website, the[…]
Being an internet user, you might have come across tones of error that would cause due to browsing data, an extension that you have added to the browser, download history, cookies from other sites that can be malicious or suspicious[…]
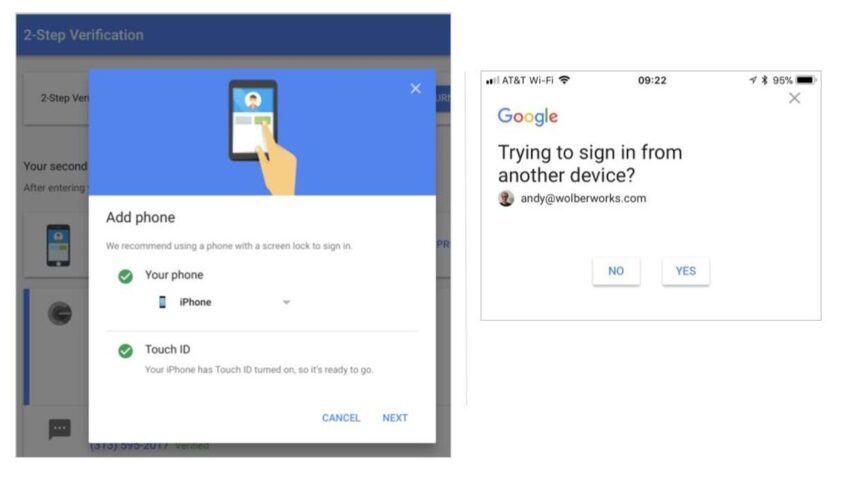
What are two-factor authentication (2FA) Being secured in every way must be our primary priority. That is why we are going to share some knowledge about how can you be secured with the help of two-step verification or dual-factor authentication.[…]
What Is SSL Inspection? Why Should You Use It?
What is SSL Inspection? As we all know that in today’s world privacy has become an important issue for everyone. These days’ people are more concerned about their personal data which they are sharing on the internet and this is[…]
If you’re encountering the SBOX_FATAL_MEMORY_EXCEEDED error while browsing on Chrome or Edge, you’re not alone. This issue can be quite frustrating as it prevents you from fully utilizing the browser. Fortunately, there are several ways to resolve this error and[…]
Fix Error ‘STATUS_BREAKPOINT’ on Chrome and Edge?
What is ‘STATUS_BREAKPOINT’ on Chrome and Edge? Errors and web browsers go hand in hand as there are can be an unusual attack of errors. The errors are very common and are faced by all the web browsers, not[…]
What is ARP Spoofing attack? Everything You Should Know
What is ARP Spoofing attack? The request response scheme of ARP protocols is arranged so that the first answer to an ARP request is accepted and stored. In the context of ARP spoofing, hackers try to pre-empt the actual target[…]
What is a Smurf Attack? A Comprehensive Guide For 2026
Last updated: Oct 31, 2025 Cybersecurity has evolved rapidly over the past few decades, and so have the ways attackers exploit weaknesses in networks. One of the earliest and most influential forms of distributed denial-of-service (DDoS) attacks is the Smurf[…]
What is a Macro Virus Attack? How to Avoid Them?
What is a macro virus attack? It destructs the software, not the system is the main aim of the macro virus attack. The most common software to prepare a macro virus attack is Microsoft Excel and word. The reason behind[…]
There have been taking place numerous types of cases with the help of emails. The emails some of the time contain messages from a friend, family, or work colleagues. The emails may seem right until you open the attachment and[…]
SQL Injection: Vulnerabilities & SQL Injection Prevention
What is SQL Injection In the early days of the internet, building websites was straightforward: no JavaScript, no CSS, and few images. But as the web gained popularity, the need for more advanced technology and dynamic websites grew. This led[…]
Web Application Firewall – How does WAF Work?
What is Web application firewall The protection to the web application from a variety of hackers, cookie poisoning, SQL injection among others. This leads to breach in apps and this makes it easy for the intruder to grab your data.[…]
What is Malware and How to Protect from Malware?
What is malware? The word malware is a kind of software that makes damage to the device, hacks the data, and creates havoc. Many malwares can cause damage to your devices such as viruses, trojans, spyware, ransomware, and many others.[…]
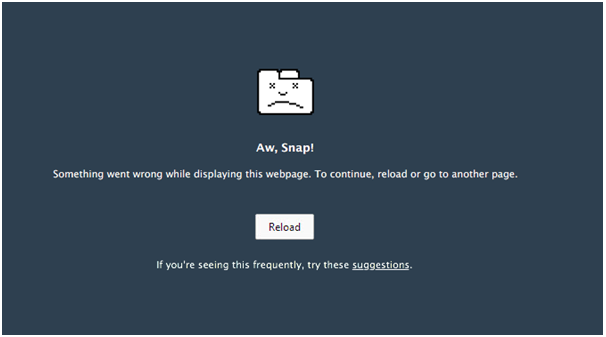
How to fix the ‘aw, Snap!’ page error on google chrome?
Last updated: Nov 1, 2025 The “Aw, Snap!” error in Google Chrome is one of the most common and frustrating issues users encounter while browsing. It occurs when Chrome is unable to load a webpage and instead displays a crash[…]
Last updated: Oct 26, 2025 The STATUS_BREAKPOINT error in Google Chrome or Microsoft Edge usually appears when the browser fails to process a web page due to a rendering crash, unexpected script execution, or a low-level interruption in the Chromium[…]
Last updated: Oct 26, 2025 Sometimes Google Chrome opens normally, but web pages refuse to load, remain stuck on a blank screen, or show network errors like ERR_CONNECTION_RESET, ERR_CONNECTION_CLOSED, ERR_CONNECTION_FAILED, or Proxy Error in Chrome. This issue doesn’t mean Chrome[…]
Last updated: Oct 26, 2025 The “No data received” error in Google Chrome (now commonly shown as ERR_EMPTY_RESPONSE) appears when Chrome successfully connects to a website but doesn’t receive any data back from the server. In other words, the connection[…]
How to fix ERR_CONNECTION_RESET error on google chrome?
How to Solve Internet Connection Problems?
The Internet has become a part of life these days as everyone is using the internet these days. It has fulfilled the communication gap between people because this one person from a corner of the world is connected to the[…]
What are Online Fake Reviews and How to Avoid them?
Everyone in today’s world is surfing the internet and also buy various products from shopping sites. But when we buy anything, we check that the product is good or not or the customers who have used that product. The feedback[…]
How to fix google chrome STATUS_INVALID_IMAGE_HASH error?
These days’ people tend to use internet websites more often and they face too many errors while switching from one website to another website. Some websites may not load properly or you might be having some network issue or the[…]
SEO and Cybersecurity – The Importance of Cyber Security to SEO
In a world where everyone is using the internet and sharing their personal data over the internet through various platforms and using net banking services, their data should be kept safe and secure. So for this purpose only Cyber Security[…]
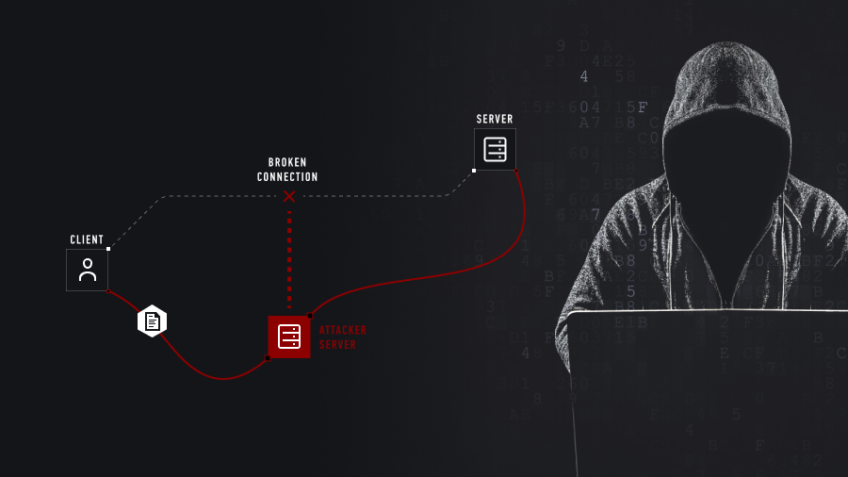
What is Domain Phishing? A Complete Guide
What is Domain Phishing? It is a method through which the hackers or the middle man gathers your personal information using Emails and Deceptive sites which exactly looks like the original site. The word Phishing sounds like Fishing but F[…]
Some Common Browser Errors while Loading a Web Page
You all have noticed some kind of errors while browsing a web page, and I am sure you all don’t like them all and want to get rid of those errors. So this will help you to figure out your[…]
What is SQL Injection? How to Prevent SQL Injection
Last updated: Nov 2, 2025 SQL Injection (SQLi) is arguably one of the most dangerous and widespread web application security vulnerabilities. Whether you’re a regular website visitor, a business owner, or a developer managing a database-driven site, you’ve likely interacted[…]
What is Cross Site Scripting (XSS)?
These days its far more important to protect the website online application that carry out number of functions. All the robust functionality is only because of JavaScript programming language. JavaScript grants permission to the website to do some pretty cool[…]
What is Web Application Firewall & How it Works?
What is Web Application Firewall? The protection to the web application from a variety of hackers, cookie poisoning, SQL injection among others. This leads to breach in apps and this makes it easy for the intruder to grab your data.[…]
What is File Integrity Monitoring and How it Works?
With the world changing rapidly the data and the system that controls the data are also changing. At the beginning of the Internet and WWW, the data used be stored on one’s personal a machine and it was accessed by[…]
What is Vishing? And How to Protect from it?
All of us at least ones got that phone call telling us we won the lottery of million dollars but when we try to get that so-called winning money they told us to give them our bank detail and that[…]
Difference between Authentication vs Authorization
Last updated: Nov 2, 2025 In the world of digital security, two terms often come up together—authentication and authorization. While they sound similar and are both essential for keeping systems and data safe, they serve very different purposes. Think of[…]
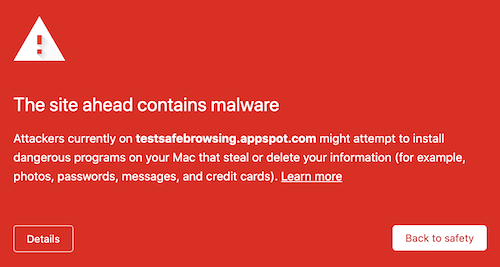
Google Chrome to Remove ‘Not-secure’ Warning
Google Chrome has long been warning users about potentially unsafe websites through the “Not Secure” label displayed in the address bar. This warning is displayed on websites that do not have an SSL/TLS certificate (Secure Socket Layer/Transport Layer Security), meaning[…]
Types of SSL Certificate
Not all websites require the same level of security, which is why there are different types of SSL/TLS certificates available today. An SSL (Secure Sockets Layer) certificate — more accurately referred to as a TLS (Transport Layer Security) certificate in[…]
Difference between HTTP and HTTPS
Last updated: Nov 2, 2025 HTTP, or Hypertext Transfer Protocol, is the foundation of data communication on the web. It was created in 1991 and is used every time you load a webpage, submit a form, or request an image[…]
Google Chrome clamps down on annoying autoplay content with latest version. Google has promoted the Chrome 66 browser to the stable channel for Mac, Linux, Android, Windows and iOS. Over the next number of weeks, the browser will be rolled[…]





































![How to Fix Google Chrome Won’t Open Load Problem [Tutorial]](https://comparecheapssl.com/wp-content/uploads/bfi_thumb/Fix-Google-Chrome-Wont-Open-Load-Problem-rhsqbbwx4b1ywtvbezxcjdrkpqi2kv0apw0gmp09a8.webp)