Antivirus, VPN & Firewall Troubleshooting
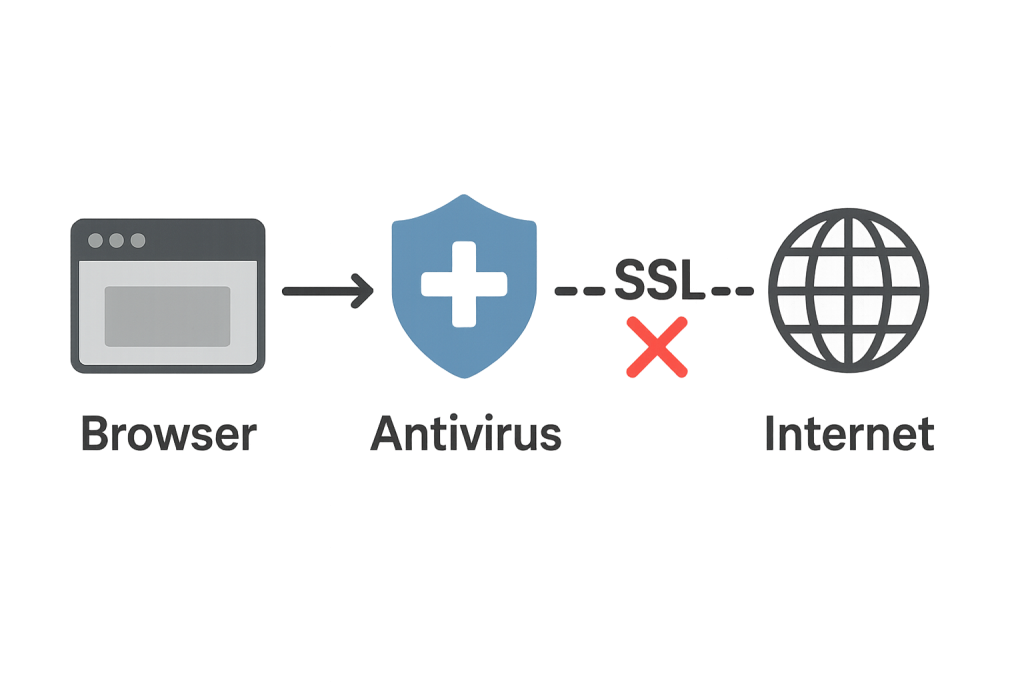
Sometimes, the ERR_SSL_PROTOCOL_ERROR isn’t caused by the browser or website — it’s your security software that’s interfering with the encrypted connection.
Modern antivirus programs, VPN clients, and firewalls often inspect HTTPS traffic, and in doing so, they may break the SSL handshake, causing this error to appear.
Here’s how to troubleshoot and resolve these issues:
How Antivirus Software Can Cause SSL Errors
Many antivirus tools include “HTTPS scanning” or “SSL filtering” features. While intended to protect you, they sometimes act as a middleman between your browser and the website — injecting their own certificates into the connection.
If this scanning process fails, your browser sees an invalid or untrusted certificate and blocks the connection with ERR_SSL_PROTOCOL_ERROR.
Disable HTTPS Scanning in Antivirus Software
If you’re using any of these tools, disable HTTPS scanning temporarily and retest:
| Antivirus Tool | How to Disable HTTPS Scanning |
|---|---|
| Bitdefender | Settings > Privacy > Web Protection > Turn off “Scan SSL” |
| Avast / AVG | Menu > Settings > Protection > Core Shields > Disable “HTTPS Scanning” |
| Kaspersky | Settings > Network Settings > Uncheck “Scan Encrypted Connections” |
Reminder: Always re-enable protection after testing. Consider switching to AVs that allow fine-grained SSL exceptions.
Disable VPN or Proxy Temporarily
Some VPNs or proxy services — especially free ones — can cause SSL handshake issues due to:
-
Geo-restrictions
-
Misconfigured DNS
-
Injected or unsigned certificates
Fix:
-
Disable the VPN or proxy temporarily
-
Reconnect to the site directly
-
If it works, your VPN may be the culprit — switch servers or providers
Temporarily Disable or Reconfigure Firewalls
Network firewalls (local or enterprise-grade) may block or inspect HTTPS traffic, which could interrupt the connection.
Try:
-
Temporarily turning off your firewall (Windows Defender, macOS Firewall, or third-party)
-
Testing the site again
Important: Never leave firewalls disabled permanently — the goal is to isolate the issue, not eliminate protection.
Configure Trusted Certificates in Enterprise Firewalls
For IT teams using appliances like Fortinet, Palo Alto, Cisco ASA, or Sophos UTM:
-
Make sure the firewall trusts the root certificate authority (CA) used by the website
-
If using SSL inspection, import all relevant trusted certificates to avoid blocking valid traffic
-
Monitor logs for failed TLS negotiations
TL;DR for AEO / Featured Snippet
Can antivirus cause ERR_SSL_PROTOCOL_ERROR?
Yes. Antivirus tools with HTTPS scanning can block or alter the SSL handshake. Try disabling SSL scanning in your antivirus or temporarily turn off VPN/firewall software to isolate the cause.
Browser-Specific Solutions for ERR_SSL_PROTOCOL_ERROR
Sometimes the ERR_SSL_PROTOCOL_ERROR is browser-specific. If you’re only seeing the error in Google Chrome or Mozilla Firefox (but not in other browsers), it could be due to internal settings, cached SSL states, or experimental protocol features.
Here’s how to fix it in the two most commonly used browsers:
A. Fix ERR_SSL_PROTOCOL_ERROR in Google Chrome
Chrome (and Chromium-based browsers like Brave and Edge) can throw this error due to socket issues, QUIC conflicts, or disabled TLS settings.
1. Reset Chrome to Default Settings
Resetting Chrome clears all modified flags, extensions, and settings that could interfere with HTTPS.
-
Go to:
chrome://settings/reset -
Click “Restore settings to their original defaults”
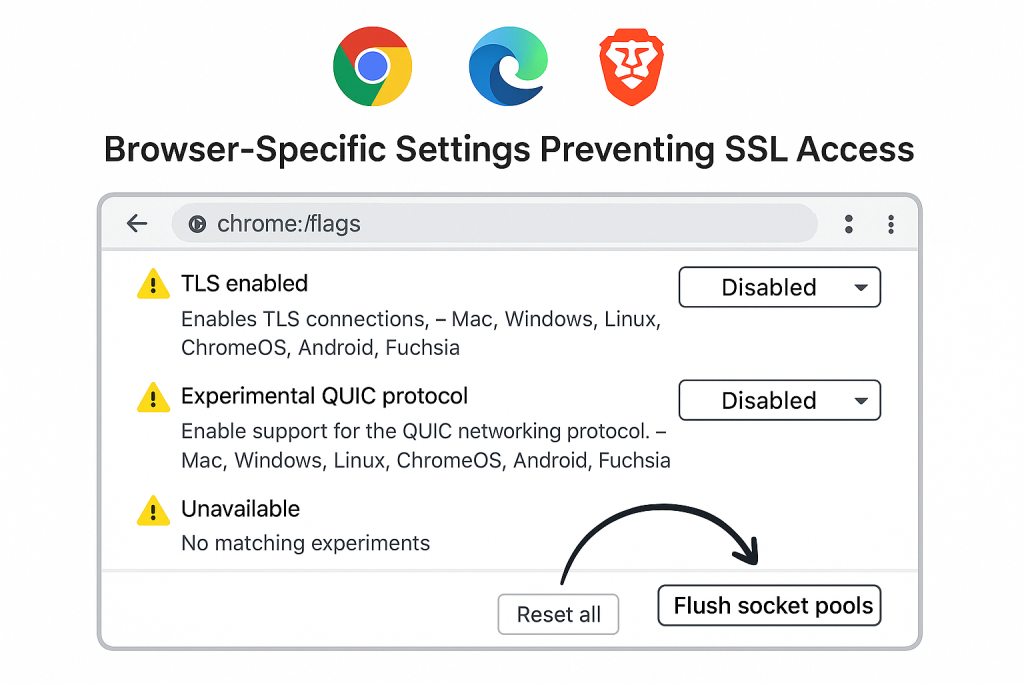
2. Enable All Supported TLS Versions
Modern Chrome versions support TLS 1.2 and TLS 1.3. If they’re disabled via experimental flags or policies, SSL errors may appear.
-
Visit:
chrome://flags -
Search for “TLS”
-
Make sure no TLS-related features are set to “Disabled”
Note: Admins can also enforce TLS policies via Group Policy or Registry settings.
3. Flush Socket Pools Using Net-Internals
Stale or corrupted SSL socket connections may trigger this error. Flushing the socket pool often helps.
-
Visit:
chrome://net-internals/#sockets -
Click “Flush socket pools”
Then restart Chrome and test again.
B. Fix ERR_SSL_PROTOCOL_ERROR in Mozilla Firefox
Firefox uses its own networking stack and certificate store. It may throw SSL_ERROR_PROTOCOL_VERSION_ALERT or SEC_ERROR_UNKNOWN_ISSUER, both of which relate to the same underlying SSL/TLS issue.
1. Clear Firefox’s SSL State
-
Go to:
Settings > Privacy & Security > Certificates -
Click “View Certificates” > “Servers”
-
Remove any suspicious or cached certificates
You can also delete cert8.db / cert9.db from the Firefox profile folder (advanced users).
2. Reset Firefox to Default
-
Go to:
about:support -
Click “Refresh Firefox”
This resets flags, extensions, and custom network settings that might interfere with TLS handshakes.
3. Check SSL/TLS Settings in about:config
If Firefox has been modified or hardened, it may have disabled required protocols.
-
Visit:
about:config -
Search for and verify these keys:
-
security.tls.version.min=3(TLS 1.2) -
security.tls.version.max=4(TLS 1.3) -
security.ssl.enable_ocsp_stapling=true
-
If any are misconfigured (e.g., too restrictive), right-click and reset to default.
Bonus Tip for All Browsers
Create a new user profile or use a fresh portable version of the browser to isolate settings-related issues.
TL;DR (for AEO/Featured Snippet Use)
Browser-specific ERR_SSL_PROTOCOL_ERROR fixes:
-
In Chrome: Reset settings, enable TLS, flush socket pools
-
In Firefox: Reset browser, check
about:config, clear SSL state
How to Prevent ERR_SSL_PROTOCOL_ERROR in the Future
Once you’ve fixed the error, the next step is making sure it doesn’t return. SSL/TLS errors are preventable with proactive maintenance, good certificate hygiene, and modern server configuration.
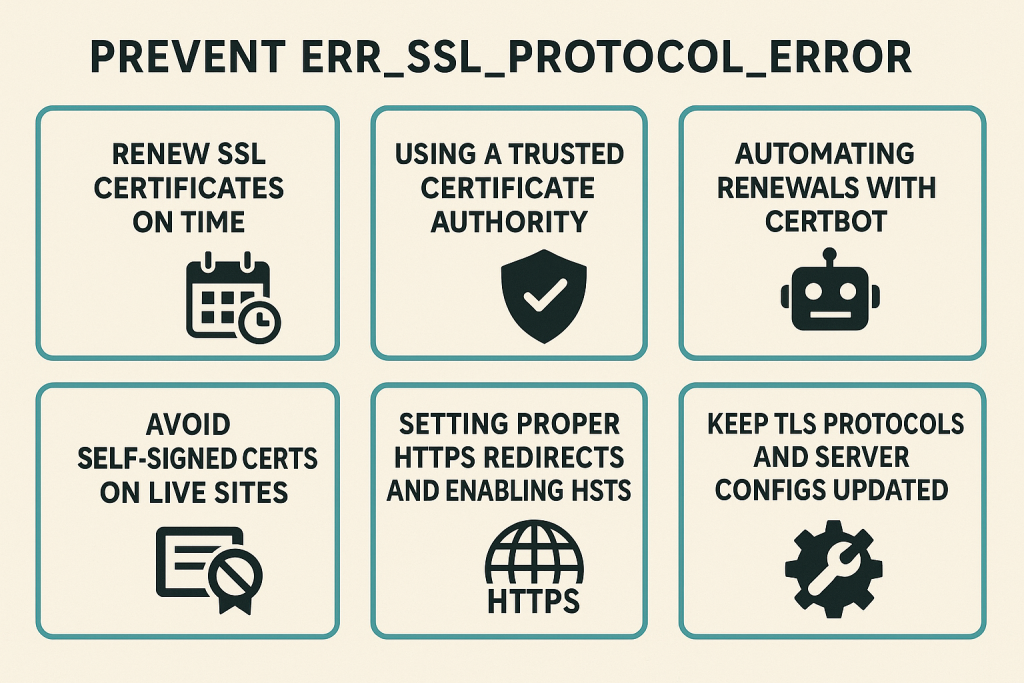
Below are best practices to prevent ERR_SSL_PROTOCOL_ERROR from impacting your users again.
1. Renew SSL Certificates Before Expiry
Letting an SSL certificate expire is one of the most common causes of connection errors. Modern browsers block access to expired certs immediately.
-
Set reminders 30 days before expiry
-
Use automation where possible
-
Monitor with uptime/SSL checker tools
Tip: Use a 90-day certificate (like Let’s Encrypt) only if you’ve automated renewal.
2. Use a Trusted, Reliable Certificate Authority (CA)
Avoid unknown or untrusted CAs — some browsers may block them or require extra configuration.
-
Stick with globally trusted providers like:
-
Sectigo
-
DigiCert
-
GlobalSign
-
SSL.com
-
Let’s Encrypt (for DV only)
-
3. Avoid Self-Signed Certificates on Public-Facing Sites
Self-signed certs are fine for internal/test environments — but public websites must use CA-issued certs or they’ll trigger trust and protocol errors.
4. Automate Renewals with Tools Like Certbot
Manual renewal = high risk of forgetting. Use automation tools such as:
-
🔄 Certbot (for Let’s Encrypt)
-
💻 ACME clients (for automated certificate lifecycle)
-
📦 Hosting control panel integrations (like cPanel AutoSSL)
5. Use Proper Redirection Rules (301 from HTTP to HTTPS)
Incorrect or insecure redirection from HTTP to HTTPS can disrupt the SSL handshake.
-
Use 301 redirects, not 302
-
Ensure all redirects occur before SSL negotiation
-
Test redirects with curl or SSL Labs
6. Implement HTTP Strict Transport Security (HSTS)
HSTS ensures browsers always use HTTPS, reducing downgrade attacks and protocol mismatches.
-
Set the
Strict-Transport-Securityheader:
Caution: Don’t enable HSTS unless you’re confident in your SSL uptime, as browsers will enforce HTTPS-only mode.
Additional Pro Tips
-
Disable old protocols (SSLv3, TLS 1.0, 1.1)
-
Keep server software and TLS libraries updated (OpenSSL, nginx, Apache, etc.)
-
Monitor SSL cert status using tools like:
-
UptimeRobot
-
SSLMate
-
Cron-based OpenSSL checks
-
Quick Comparison: Common ERR_SSL_PROTOCOL_ERROR Causes vs. Fixes
| Problem | Who It Affects | Fix |
|---|---|---|
| Expired SSL certificate | Website | Renew the certificate before expiry |
| Browser cache or cookies | Visitor | Clear browser cache and cookies |
| Outdated TLS version | Website | Enable TLS 1.2 or TLS 1.3 on server |
| Antivirus HTTPS scanning | Visitor | Disable HTTPS scanning in antivirus |
| Incorrect date/time | Visitor | Sync system time with an internet server |
Use This Table To:
-
Quickly diagnose SSL-related issues
-
Understand whether it’s a visitor-side or server-side problem
-
Implement the correct fix without trial-and-error
Tools to Diagnose SSL Protocol Errors
When facing the ERR_SSL_PROTOCOL_ERROR, identifying the root cause is half the battle. Whether you’re a developer, sysadmin, or curious user, the following tools help you pinpoint where the SSL handshake is breaking down — and why.
Recommended SSL Diagnosis Tools
| Tool | Purpose | How to Use |
|---|---|---|
| 🔍 SSL Labs (ssllabs.com/ssltest) | Analyze full SSL config, grade TLS support, detect chain issues | Enter your domain and view results in minutes |
| 🧑💻 Browser Developer Tools (Chrome/Firefox) | See certificate details, protocol versions, and handshake failures | Go to F12 > Network > Security tab while loading the site |
| 💻 OpenSSL CLI | Test SSL handshake manually, check protocol and cipher support | Run: openssl s_client -connect domain.com:443 |
| 🔁 Curl (Verbose Mode) | Check redirect paths, certificate status, and SSL errors | Run: curl -Iv https://domain.com |
| 🌐 DNS Propagation Checker (e.g., DNSChecker.org) | Ensure recent DNS or SSL cert changes have propagated globally | Input your domain and check results across locations |
Bonus Tools for Deeper Debugging
-
Wireshark: Inspect SSL/TLS packets (advanced use)
-
SSLMate Cert Spotter: Monitor and alert on certificate issues
-
Hardening tools: Test against PCI DSS, NIST, and browser standards
Bonus: How to Fix ERR_SSL_PROTOCOL_ERROR on Android
The ERR_SSL_PROTOCOL_ERROR can show up on Android too — often when browsing in Google Chrome, using a VPN, or after installing certain apps.
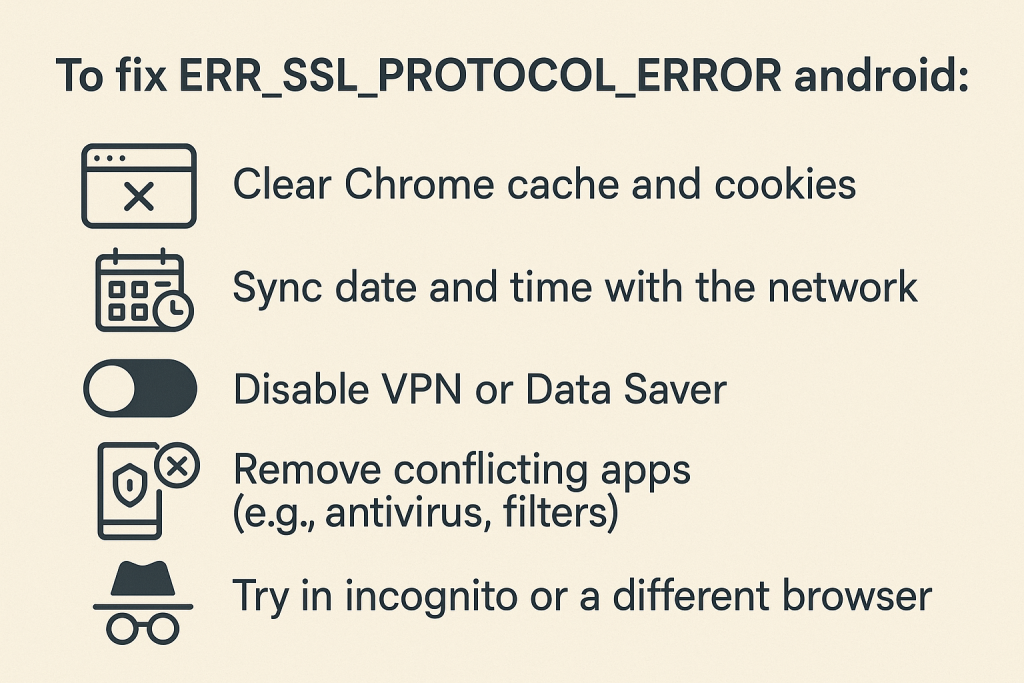
Here’s how to fix it quickly on your Android phone or tablet:
1. Clear Chrome Cache and Browsing Data
Corrupted cache or old SSL state can break the connection.
-
Open Chrome → Tap Menu (⋮) > History > Clear Browsing Data
-
Select Cached Images and Files and Cookies and Site Data
-
Tap Clear Data
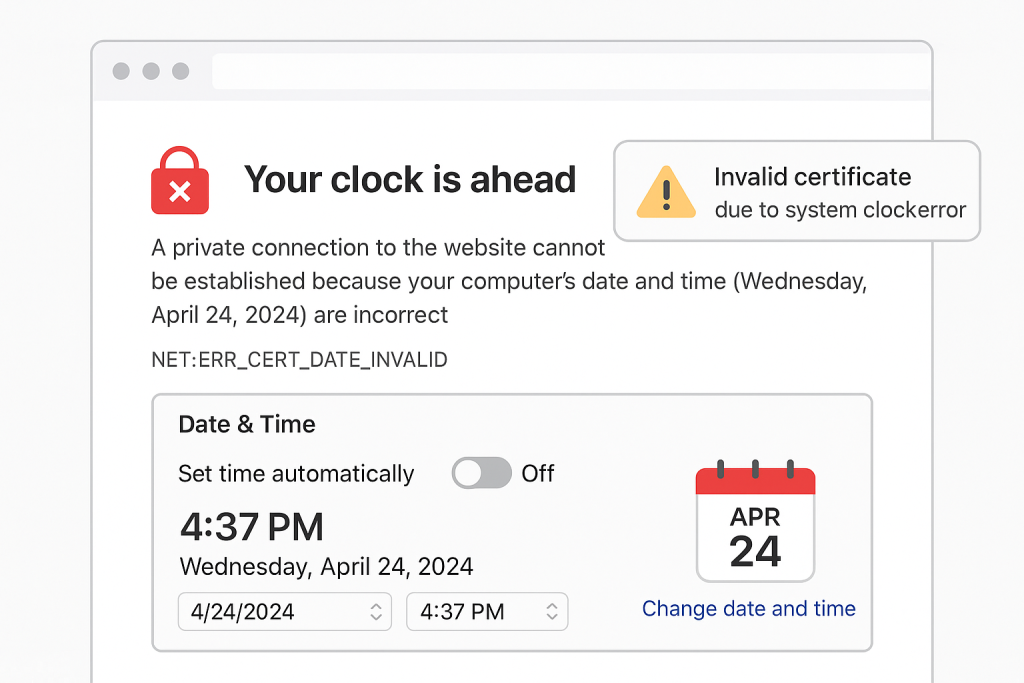
2. Check and Correct Date & Time Settings
Incorrect system time is a common cause of SSL certificate validation failure.
-
Go to Settings > System > Date & Time
-
Enable “Use network-provided time” and “Time zone”
3. Remove or Reinstall Problematic Apps
Apps that inject network filters or perform SSL inspection (e.g., parental control, antivirus, or ad-blocking apps) may cause the error.
-
Uninstall recently added apps
-
Reboot and test again in Chrome
4. Disable Data Saver or VPN Temporarily
VPNs and Android’s built-in Data Saver mode can interfere with SSL handshakes.
-
Turn off Data Saver:
Settings > Network & Internet > Data Saver > Off -
Turn off VPN (if using one) and try reloading the site
5. Check Antivirus or Security Apps
Mobile antivirus apps with HTTPS scanning or web filtering may block SSL certificates.
-
Temporarily disable or uninstall apps like Kaspersky Mobile, Avast, or Norton
-
Test if the site loads after disabling
Extra Tip: Try in Incognito Mode or Different Browser
To isolate Chrome-specific problems, test the site in:
-
Incognito Mode
-
Firefox or another browser
If it works elsewhere, Chrome settings are likely to blame.
When to Contact Support
If you’ve tried the browser, network, and server-side fixes but are still seeing ERR_SSL_PROTOCOL_ERROR, it may be time to escalate the issue to support teams.
Here’s who to contact — and when:
1. Contact Your Hosting Provider
If:
-
Your SSL certificate isn’t installing properly
-
The server is missing intermediate certs
-
HTTPS redirect rules are misconfigured
-
TLS 1.2 or 1.3 isn’t enabled
✅ Ask them to:
-
Reinstall or reissue your SSL certificate
-
Verify proper server-level HTTPS support
-
Confirm latest OpenSSL or TLS settings
2. Reach Out to Your CDN Provider (Cloudflare, Akamai, etc.)
If you’re using a CDN or reverse proxy, the SSL error might stem from:
-
Improper SSL mode (Flexible vs. Full/Strict in Cloudflare)
-
Origin certificate mismatch
-
Caching of expired certs
✅ Check with CDN support to:
-
Confirm proper SSL mode
-
Purge SSL cache
-
Re-sync with origin server SSL settings
3. Contact Your Certificate Authority (CA)
If the certificate was:
-
Revoked
-
Misissued
-
Showing up as untrusted
-
Issued to the wrong domain (SAN/CN mismatch)
✅ Contact providers like:
-
Sectigo
-
DigiCert
-
SSL.com
-
Let’s Encrypt (via Certbot or forum support)
They can reissue, revoke, or correct any CA-side problems.
TL;DR: Who to Contact for SSL Errors
| Issue | Who to Contact |
|---|---|
| SSL not installing or redirect issues | Hosting Provider |
| CDN/SSL mode conflict | CDN Provider (e.g., Cloudflare) |
| Certificate revocation/mismatch | Certificate Authority |
Conclusion & Key Takeaways
The ERR_SSL_PROTOCOL_ERROR may seem like a technical nightmare, but it’s usually fixable with the right steps — whether you’re a casual site visitor, a website owner, or a sysadmin managing SSL infrastructure.
Recap of Common Causes
-
Expired or misconfigured SSL certificates
-
Outdated TLS protocols or weak ciphers
-
Browser cache, SSL state, or extensions
-
Antivirus, VPNs, or firewalls blocking SSL handshakes
-
Incorrect system time or insecure redirects
Recap of Fixes
For Users:
-
Clear browser cache and cookies
-
Check date/time and browser updates
-
Disable HTTPS scanning in antivirus tools
-
Test on a different browser, device, or network
For Site Owners:
-
Renew and install SSL certificates correctly
-
Validate intermediate certs and full trust chain
-
Enable TLS 1.2 or 1.3; disable outdated protocols
-
Use diagnostic tools (SSL Labs, OpenSSL, curl)
-
Implement secure 301 redirects and HSTS properly
Why SSL Hygiene Matters
A secure, functional SSL/TLS setup is critical for website security, trust, SEO performance, and user experience.
Even one misstep — like an expired cert or broken redirect — can block visitors, tank search rankings, and damage your brand.
Final Recommendations
-
Audit your SSL/TLS configuration regularly
-
Use reputable Certificate Authorities and automation tools (e.g., Certbot)
-
Monitor certificate status to avoid expiry surprises
-
Test changes in all major browsers and devices
FAQs About ERR_SSL_PROTOCOL_ERROR
What does ERR_SSL_PROTOCOL_ERROR mean?
It means the browser failed to establish a secure connection due to a problem with the SSL/TLS handshake. This could be caused by a misconfigured server, expired SSL certificate, or browser/network-related issue.
Why am I getting ERR_SSL_PROTOCOL_ERROR in Chrome or Firefox?
Common reasons include:
-
Outdated TLS protocol support
-
Corrupted browser cache or SSL state
-
Antivirus software scanning HTTPS traffic
-
Incorrect system date/time
-
Issues with the website’s SSL certificate
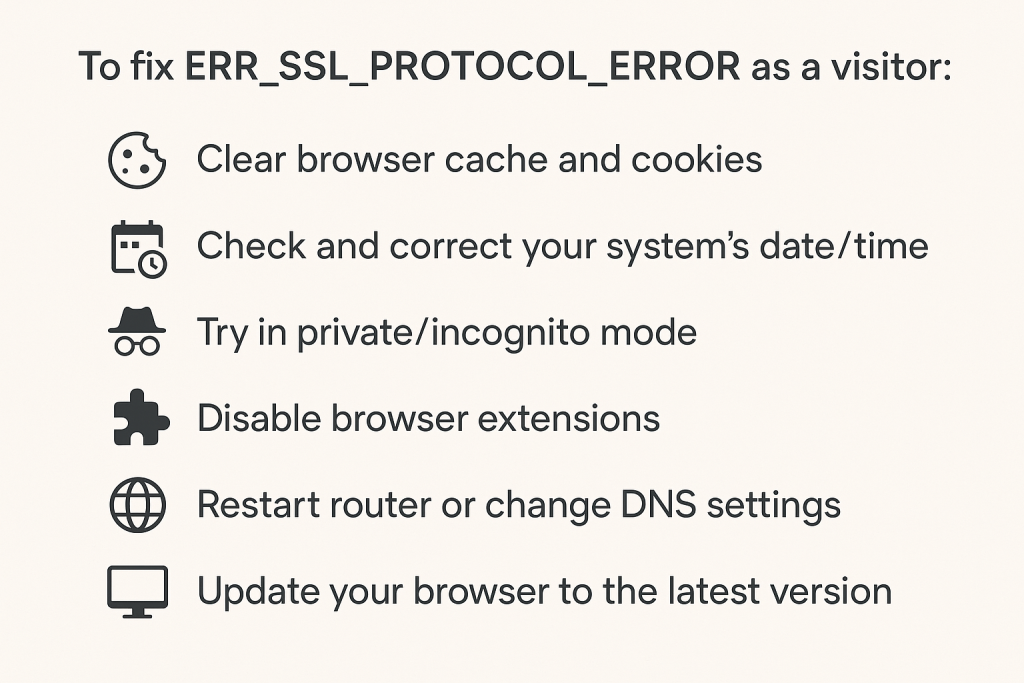
How do I fix ERR_SSL_PROTOCOL_ERROR as a user?
You can:
-
Clear browser cache and cookies
-
Check date/time settings
-
Try in incognito mode or another browser
-
Disable antivirus HTTPS scanning temporarily
-
Switch DNS to Google (8.8.8.8) or Cloudflare (1.1.1.1)
How can website owners fix ERR_SSL_PROTOCOL_ERROR?
-
Install the correct SSL certificate with full chain
-
Ensure TLS 1.2+ is enabled, and weak ciphers are disabled
-
Configure proper redirects (HTTP to HTTPS)
-
Use SSL Labs or OpenSSL to detect handshake issues
-
Fix misconfigured CDN or reverse proxy settings
Can antivirus or VPN cause SSL protocol errors?
Yes. Many antivirus programs perform HTTPS scanning, which can interrupt the SSL handshake. VPNs may also route traffic through insecure servers. Try disabling these temporarily to test.
Is ERR_SSL_PROTOCOL_ERROR dangerous?
Not inherently. It blocks insecure connections and protects users. But if seen on your own site, it indicates a serious SSL misconfiguration that must be fixed to restore trust and access.
Will this error fix itself?
Sometimes — especially if caused by DNS propagation or temporary cache issues. But if the underlying SSL certificate or server configuration is incorrect, it requires manual intervention.