Cloud computing, APIs, and distributed systems, digital security is more important than ever—especially for Java-based enterprise applications that transmit sensitive data across networks. One of the most critical elements in ensuring data confidentiality and secure communication is SSL/TLS encryption. It protects data from man-in-the-middle attacks, eavesdropping, and tampering while it moves between client and server.
To implement SSL/TLS encryption effectively in Java, two essential components come into play: the Keystore and the Truststore. These two files form the backbone of Java’s security architecture, but they’re often confused with each other. While they both store certificates, their roles are very different. The Keystore stores private keys and the certificates representing the identity of the server (or client), whereas the Truststore contains certificates of external parties (Certificate Authorities or trusted servers) that the application should trust.
Understanding the difference between Keystore and Truststore is not just useful—it’s necessary if you’re configuring HTTPS on a Spring Boot application, enabling mutual TLS (mTLS), integrating with secure third-party APIs, or deploying Java apps in production environments where security compliance is mandatory.
This guide aims to provide a complete understanding of Keystore and Truststore in Java, including:
- What they are and how they differ
- Their respective roles in establishing SSL/TLS handshakes
- How to create, configure, and manage them using the Java keytool utility
- Real-world examples and best practices
- Common mistakes and how to avoid them
By the end of this blog post, you’ll be equipped to confidently secure your Java applications using the right certificate strategies and avoid common pitfalls that lead to SSL handshake failures, trust issues, or vulnerabilities.
What is a Keystore?
A Keystore in Java is a secure storage mechanism used to store cryptographic keys, digital certificates, and private key entries. It is essentially a password-protected database file that holds sensitive information required for secure communication and identity verification in Java-based applications.
At the core of the Keystore is the ability to store private keys along with the associated public key certificates. These private keys are used during SSL/TLS handshakes, allowing a server (or sometimes a client) to prove its identity to the other party in the communication. The Keystore ensures that only authorized applications or services can access these private keys, typically by protecting them with strong passwords.
Where is a Keystore Used?
A Keystore is primarily used in Java applications that need to present their own identity. This is most commonly seen in:
- SSL/TLS server-side authentication – where the server presents its digital certificate to the client to prove its identity.
- Mutual TLS (mTLS) – where both the client and the server authenticate each other using certificates.
- Digital signatures – where applications need to sign data or documents securely using a private key.
- Code signing – where a developer signs a JAR file or application build to verify its authenticity and integrity.
In these contexts, the Keystore plays a critical role in securing communications and ensuring trust.
File Formats and Tools
In Java, Keystores are typically managed using the built-in keytool command-line utility. The default file format for a Keystore is JKS (Java KeyStore), although newer formats like PKCS12 (.p12 or .pfx) are also widely used due to better interoperability with non-Java platforms.
A typical Keystore entry includes:
- Private key – used for encrypting or signing.
- Public certificate – used by other parties to verify the identity.
- Certificate chain – a series of certificates leading up to a trusted root CA.
The Keystore ensures that all this sensitive cryptographic data is stored securely and accessed only by trusted applications.
What is a Truststore?
A Truststore in Java is a secure file used to store trusted certificates—specifically, the public certificates of external entities like Certificate Authorities (CAs) or remote servers that your application needs to trust. While a Keystore contains your application’s own credentials, the Truststore contains the credentials of others that you want to trust during secure communication.
The Truststore does not contain private keys. Instead, it stores public certificates or certificate chains issued by CAs. These are used to validate the digital certificates presented by a server or client during an SSL/TLS handshake.
Where is a Truststore Used?
Truststores are used in scenarios where your application acts as a client and needs to validate the identity of a remote server, or in mutual TLS (mTLS), where both parties verify each other’s identities.
Key use cases include:
- SSL/TLS client authentication – When your Java application connects to a remote HTTPS server, it verifies the server’s certificate against the certificates stored in its Truststore.
- Validating server certificates in REST API calls – If your Java app consumes APIs over HTTPS, it uses the Truststore to determine whether the server’s certificate is signed by a trusted CA.
- Mutual TLS – When both client and server verify each other’s certificates using their respective Truststores.
If the server’s certificate—or its issuing CA—is not present in the Truststore, Java will throw an error like PKIX path building failed, which means the SSL certificate is not trusted.
File Formats and Tools
Like Keystores, Truststores are typically managed using Java’s keytool utility and stored in JKS or PKCS12 format. The file is password-protected to prevent unauthorized modification.
A Truststore commonly contains:
- Root CA certificates
- Intermediate CA certificates
- Self-signed certificates (for internal use or development environments)
It’s essential to keep your Truststore updated with the correct and valid public certificates of all systems and services your application communicates with.
Keystore vs Truststore – Key Differences
While both Keystore and Truststore are essential for enabling secure SSL/TLS communication in Java applications, they serve distinct purposes. Understanding the differences between the two is critical to properly configuring secure connections, especially in enterprise-level systems or when implementing mutual TLS authentication.
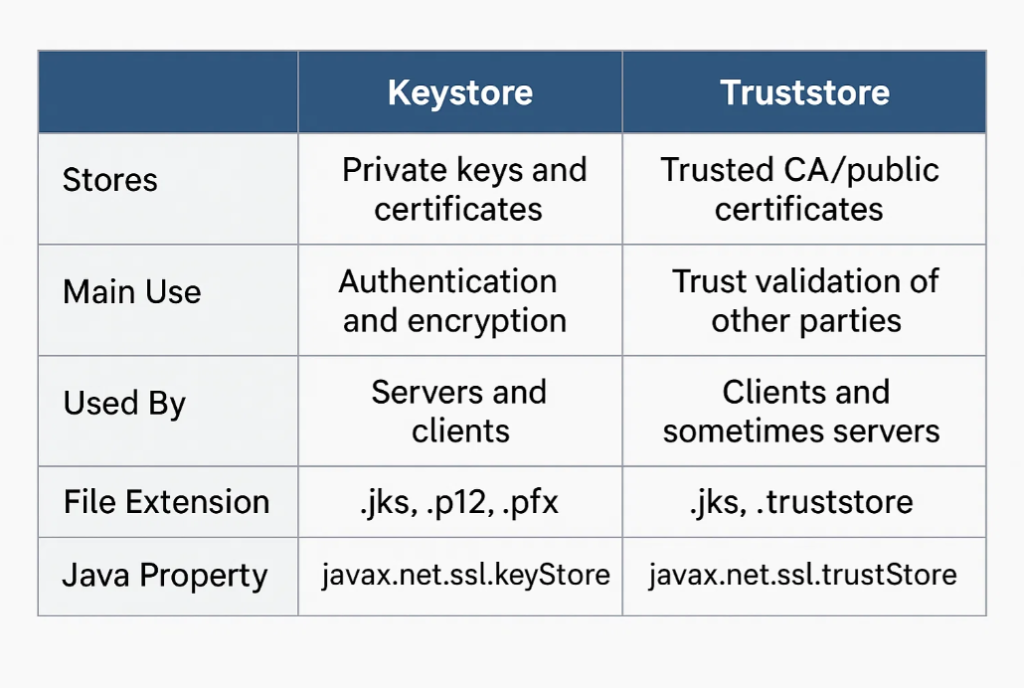
- Keystore stores private keys and certificates required for authentication and encryption, whereas Truststore contains trusted public certificates used to verify external identities.
- Keystore is used by applications (both clients and servers) to prove their own identity, whereas Truststore is used to verify the identity of other parties.
- Keystore supports secure communication by enabling SSL/TLS handshakes with its own credentials, whereas Truststore ensures trust by validating certificates presented by others.
- Keystore files typically have extensions like .jks, .p12, or .pfx, whereas Truststore files often use .jks or .truststore.
- Keystore is configured using the Java system property net.ssl.keyStore, whereas Truststore is configured using javax.net.ssl.trustStore.
Why This Distinction Matters
- A Keystore is essential when your application must prove its own identity, such as when acting as an HTTPS server or making signed API requests.
- A Truststore is required when your application must verify the identity of another party, such as when connecting to an external HTTPS API or database securely.
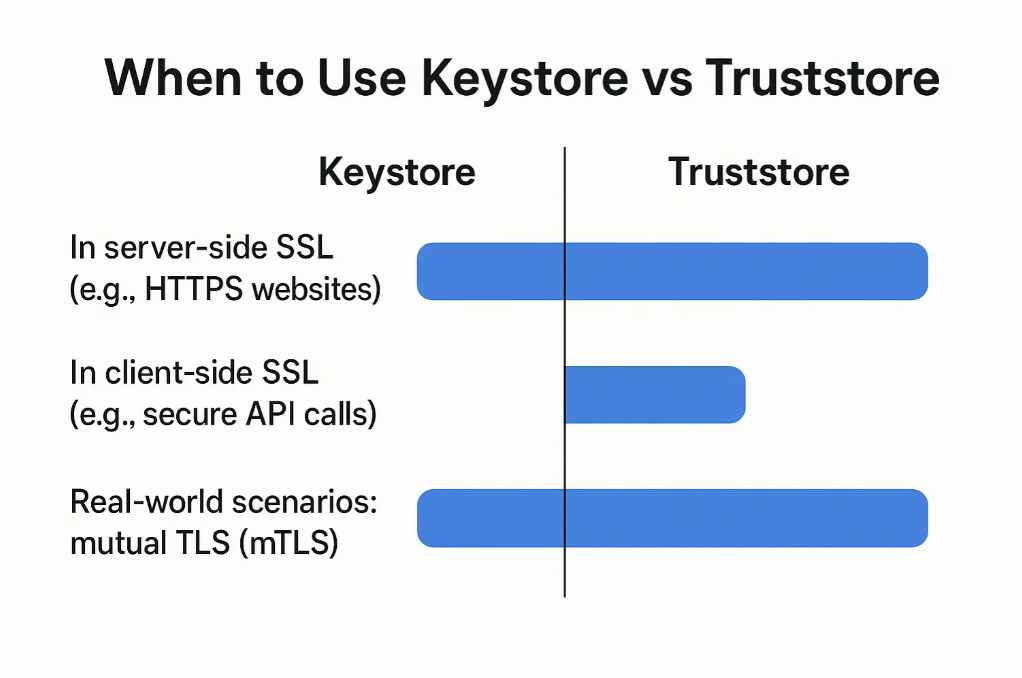
Understanding when to use a Keystore and when to use a Truststore is essential for securing Java-based applications with SSL/TLS encryption. Each serves a unique role—Keystore is used to identify your application, while Truststore is used to verify others. Here’s how they are applied in real-world scenarios:
- Server-Side SSL (e.g., HTTPS Websites)
When you’re running a Java-based HTTPS server (like Tomcat or Spring Boot), you need a Keystore to securely store your private key and SSL certificate. This certificate is presented to clients (such as browsers or API consumers) to prove the identity of your server.
- Use: Keystore
- Java property: javax.net.ssl.keyStore
- Example: Hosting an HTTPS-enabled REST API using Spring Boot.
✅ You only need a Truststore here if the server is also acting as a client to another secure system.
- Client-Side SSL (e.g., Secure API Calls)
If your Java application is making HTTPS requests to external servers (like third-party APIs), it needs to verify the server’s certificate. This is where the Truststore comes in—it contains the trusted Certificate Authorities (CAs) or public certificates of the servers you’re connecting to.
- Use: Truststore
- Java property: javax.net.ssl.trustStore
- Example: Your backend system connects to a payment gateway like Razorpay or Stripe over HTTPS.
🔒 Without a proper Truststore, your app may throw SSL handshake errors due to untrusted certificates.
- Mutual TLS (mTLS)
In mutual TLS (mTLS), both server and client must authenticate each other. This is often used in high-security enterprise environments, financial systems, or inter-microservice communication.
- Server uses:
- Keystore to present its own certificate
- Truststore to validate client’s certificate
- Client uses:
- Keystore to present its own identity
- Truststore to validate the server’s certificate
- Real-world example: A banking app’s microservice authenticates another internal microservice using mTLS for secure data exchange.
🔁 mTLS ensures two-way verification, strengthening authentication and trust.
Summary: Which to Use?
| Scenario | Use Keystore | Use Truststore |
| Running a secure HTTPS server | ✅ | ❌ (optional) |
| Making secure HTTPS API calls | ❌ | ✅ |
| Using mutual TLS (mTLS) | ✅ | ✅ |
How to Create Keystore and Truststore (Step-by-Step)
Creating and managing Keystore and Truststore files is a fundamental task when securing Java applications with SSL/TLS. The Java keytool utility is the standard tool used to create, import, and manage these files, while OpenSSL can also be used for certificate generation and conversion. Below is a step-by-step guide to create and configure Keystore and Truststore.
Step 1: Generate a Keystore with a Self-Signed Certificate
Use the Java keytool command to generate a Keystore that contains a private key and a self-signed certificate. This is useful for development and testing.
keytool -genkeypair -alias myserverkey -keyalg RSA -keysize 2048 -validity 365 -keystore keystore.jks
- Explanation:
- -genkeypair: Generates a key pair (private + public key).
- -alias myserverkey: An identifier for the key.
- -keyalg RSA: Algorithm used for the key.
- -keysize 2048: Size of the key in bits.
- -validity 365: Certificate validity in days.
- -keystore keystore.jks: Output keystore file.
- After running, you’ll be prompted to enter a password for the keystore and provide details like your name, organization, and location.
Step 2: Export the Certificate from the Keystore
If you want to share your public certificate (e.g., for clients or Truststore), export it using:
keytool -exportcert -alias myserverkey -keystore keystore.jks -file myserver.crt
- This exports the certificate in .crt format.
Step 3: Create a Truststore and Import a Certificate
A Truststore contains trusted certificates (usually CA certificates). You can create an empty Truststore and import certificates into it:
keytool -importcert -alias trustedcert -file myserver.crt -keystore truststore.jks
- If the truststore doesn’t exist, this command creates it.
- You’ll be prompted to create a password and confirm trusting the certificate.
Step 4 (Optional): Create Keystore from Existing Certificates Using OpenSSL
Sometimes, certificates and keys come separately in .pem or .crt and .key files. Use OpenSSL to convert and create a PKCS12 keystore that Java can consume:
openssl pkcs12 -export -in certificate.crt -inkey private.key -out keystore.p12 -name myserverkey
Then import this PKCS12 file into a Java keystore if needed:
keytool -importkeystore -destkeystore keystore.jks -srckeystore keystore.p12 -srcstoretype PKCS12 -alias myserverkey
Step 5: Verify Contents of Keystore and Truststore
To check what certificates/keys are inside a keystore or truststore:
keytool -list -v -keystore keystore.jks
keytool -list -v -keystore truststore.jks
This lists all aliases and certificate details, useful for verification.
Summary of Tools
| Tool | Purpose |
| keytool | Java utility to create/manage keystores and truststores |
| OpenSSL | Generate/convert certificates and keys |
Example Output Snippet from keytool -list
Alias name: myserverkey
Creation date: May 25, 2025
Entry type: PrivateKeyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=My Server, OU=Dev, O=Company, L=City, ST=State, C=US
Issuer: CN=My Server, OU=Dev, O=Company, L=City, ST=State, C=US
Serial number: 1234567890abcdef
Valid from: May 25, 2025 until: May 24, 2026
By following these steps, you can create, export, import, and verify your keystore and truststore files for secure SSL/TLS communication in Java applications.
Common Mistakes to Avoid When Working with Keystore and Truststore
When implementing SSL/TLS security in Java applications, understanding the differences and proper use of Keystore and Truststore is critical. Mistakes in managing these files can lead to security vulnerabilities, connection failures, or unexpected errors. Here are some common pitfalls developers should avoid:
- Mixing Up Keystore and Truststore
One of the most frequent errors is confusing the Keystore with the Truststore.
- Keystore stores your application’s private keys and certificates, which are used to authenticate your identity to others (e.g., a server proving itself to clients).
- Truststore stores trusted certificates, usually public certificates from Certificate Authorities (CAs) or other parties you trust.
Mixing them up—for example, importing trusted CA certificates into the Keystore or private keys into the Truststore—can cause SSL handshake failures or compromise security. Always remember: Keystore is for your keys, Truststore is for others’ trusted certificates.
- Using Self-Signed Certificates Incorrectly
While self-signed certificates are convenient for development or internal testing, relying on them in production environments without proper Truststore configuration is a major mistake.
- If clients or other servers don’t explicitly trust your self-signed certificate by adding it to their Truststore, SSL/TLS connections will fail.
- Blindly trusting self-signed certificates or bypassing certificate validation reduces security and exposes your app to man-in-the-middle attacks.
Always use certificates signed by a trusted CA for production, or ensure that any self-signed certificates are explicitly imported into the relevant Truststores.
- Ignoring Truststore in Client-Side SSL
Another common oversight occurs in client applications making secure API calls or connecting to secure servers:
- Many developers configure the Keystore properly but forget to set or configure the Truststore on the client side.
- Without a properly configured Truststore containing the server’s certificate (or its CA chain), the client cannot validate the server’s identity, leading to SSL handshake errors.
- This often causes exceptions like javax.net.ssl.SSLHandshakeException.
Always ensure that your client applications have an up-to-date Truststore with all required trusted certificates to establish secure connections.
Frequently Asked Questions (FAQs)
What is the difference between keystore and truststore in Java?
The keystore is a secure storage file used to hold your application’s private keys and associated certificates. It is primarily used for authenticating your server or client during SSL/TLS handshakes.
On the other hand, the truststore stores trusted certificates from external parties or Certificate Authorities (CAs) that your application trusts. The truststore is used to validate the identity of remote servers or clients during secure communication.
Can a keystore act as a truststore?
Technically, a keystore can contain trusted certificates and thus act as a truststore. However, it is best practice to keep them separate for security and clarity reasons. Keeping keystore and truststore distinct helps avoid configuration errors and clearly separates private keys from trusted public certificates.
Is a keystore required for HTTPS?
Yes, a keystore is required for HTTPS because it holds the private key and SSL/TLS certificate your server uses to establish its identity to clients. Without a keystore containing these credentials, your server cannot properly perform SSL/TLS handshakes to secure HTTPS connections.
How do I check the contents of a keystore or truststore?
You can inspect the contents of both keystore and truststore using the Java keytool utility. The typical command is:
bashCopyEditkeytool -list -v -keystore <path-to-keystore-file>
This command displays detailed information about all entries (keys and certificates) stored inside the keystore or truststore.
What is the default password for Java keystore?
The default password for Java keystore files (with .jks extension) is changeit. However, it is highly recommended to change this password to a strong, unique password for better security.