TL;DR: “SSL” is the legacy name people still use for the technology that secures the web. Today we use TLS. An SSL/TLS certificate (X.509) proves your site’s identity and enables HTTPS (HTTP over TLS) so data is encrypted, authentic, and tamper‑evident.
What is SSL?
SSL (now TLS) is the security protocol that encrypts traffic between a browser and a server. An SSL/TLS certificate verifies the site’s identity and turns HTTP into HTTPS. A website, online shop, or any platform that collects data uses SSL Certificate to create an encrypted connection between the user’s browser and the server. This means any data transmitted between the web server and the browser cannot be read without first being decrypted. In short, when you see SSL HTTPS or the HTTPS protocol, it ensures that communication is secure.
SSL meaning has evolved over time. SSL stands for Secure Sockets Layer, which is a standard security technology for establishing encrypted links between a web server and a browser in online communication. While SSL itself is now deprecated and replaced by TLS (Transport Layer Security), many people still refer to TLS as SSL. So, when you ask, “What does SSL mean?” or search for the SSL full form, it refers to Secure Sockets Layer—a protocol ensuring encrypted and private communication online.
The SSL definition dates back to 1994, when Netscape developed it as a way to make internet browsing safer. Initially, it wasn’t widely adopted because the internet was not as risky. However, with increasing cases of data breaches and identity theft, SSL became crucial. By 2015, SSL/TLS adoption became standard practice across websites. This is why today, when you see “https://” in a URL, you’re really seeing the implementation of SSL HTTPS (or more accurately, TLS).
SSL stands for Secure Sockets Layer, and it is a standard security protocol for establishing encrypted links between a web server and a browser in an online communication. The encrypted connection ensures that the data transmitted between the web server and the browser remains confidential and secure.
“SSL” originally referred to Secure Sockets Layer, a cryptographic protocol from the 1990s that encrypted data in transit.
However, SSL itself is now fully deprecated — modern sites use TLS (Transport Layer Security), which replaced SSL due to major security flaws in SSLv2 and SSLv3. When people still say “SSL certificate,” they actually mean a TLS (X.509) certificate — installed on the server to enable HTTPS (HTTP over TLS) by providing:
-
Authentication (proves the server’s identity)
-
Encryption (protects data from interception)
-
Integrity (prevents tampering or injection)
How does SSL/TLS work?
SSL/TLS works by creating a secure, encrypted channel between a client (like your browser) and a server (like a website). This prevents attackers from intercepting, reading, or tampering with any data exchanged over the connection. The process that sets up this secure channel is called the TLS handshake.
In modern web security (especially TLS 1.3), this handshake is optimized for speed, forward secrecy, and stronger encryption standards. Here’s how it works step by step:
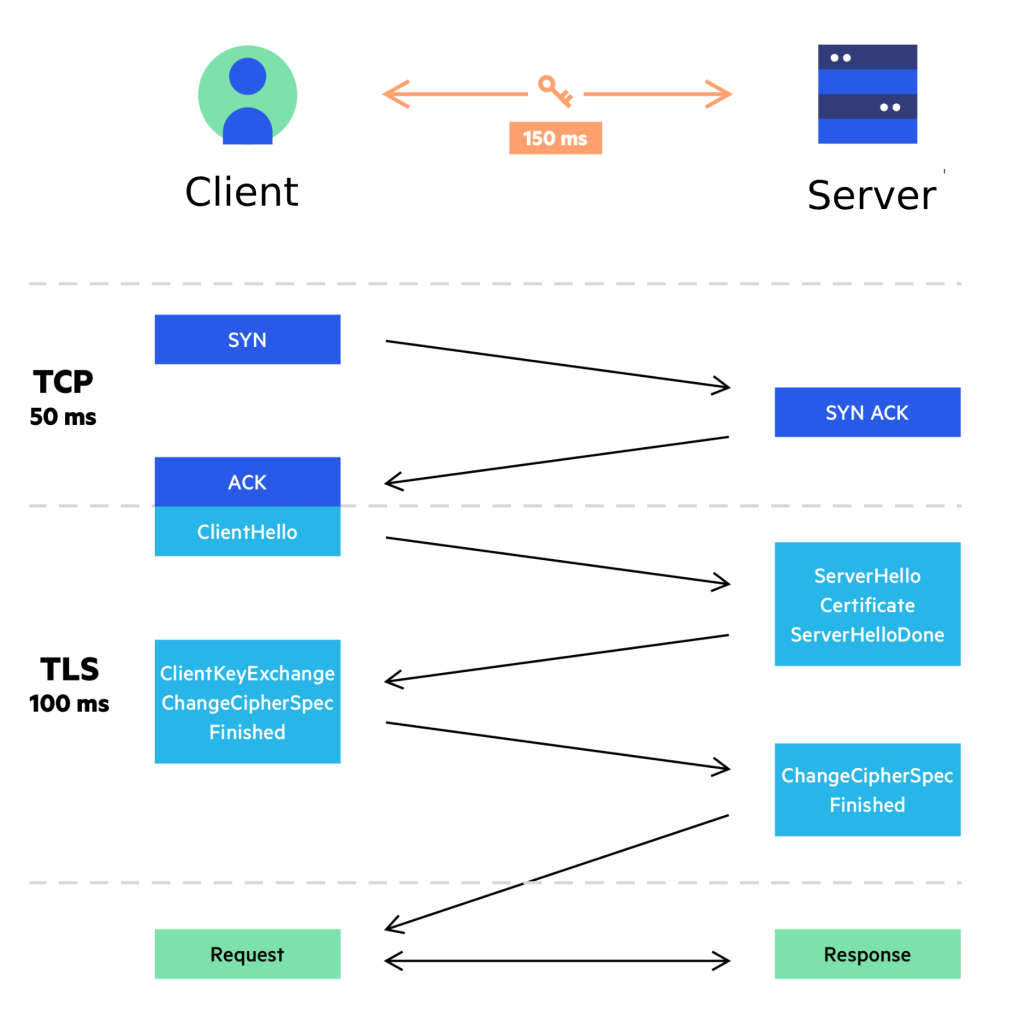
1. Handshake Initialization
The client begins the connection by sending a ClientHello message to the server. This message includes:
-
Supported TLS versions
-
Supported encryption algorithms (cipher suites)
-
A random value used in key generation
The server replies with a ServerHello, confirming which version and cipher suite will be used. TLS 1.3 always selects strong, modern algorithms by default.
2. Server Authentication
Next, the server proves its identity by sending its digital certificate, signed by a trusted Certificate Authority (CA).
The client (browser) verifies:
-
The certificate is valid and not expired
-
The domain matches the certificate
-
The CA is trusted
This prevents man-in-the-middle attacks and impersonation.
3. Key Exchange (Forward Secrecy)
Once the server is authenticated, both sides perform a key exchange.
In older TLS (like TLS 1.2), the client encrypted a pre-master secret using the server’s public key.
But in TLS 1.3, a more modern and secure approach is used: Ephemeral Diffie-Hellman (ECDHE).
This means:
-
A temporary (ephemeral) key is generated just for this session
-
Even if someone stole the server’s private key later, past data could not be decrypted
-
This property is called forward secrecy
From this exchange, both client and server independently derive the same symmetric session key.
4. Symmetric Encryption (Secure Channel Established)
After the key is agreed upon, the connection switches from public-key cryptography to symmetric encryption. This is much faster and efficient for ongoing data transfer.
All further communication — page requests, passwords, payment details — is now encrypted using this shared secret key.
TLS also ensures integrity, meaning if data is modified during transit, it will be detected.
5. Secure Data Transfer
At this point, the handshake is complete, and a fully secure channel is active.
The client and server can now send data privately and reliably without exposure to eavesdropping or tampering.
6. Session Resumption (Speed Optimization)
To improve performance on repeat visits, TLS allows session resumption.
In TLS 1.3, this can even work with 0-RTT (zero round-trip time), meaning the client can send encrypted data immediately without repeating the entire handshake — significantly reducing load time.
Why is SSL/TLS important?
If you’ve ever wondered “Why do websites need SSL?” or “What does SSL really do?”, the answer is simple: it keeps your data private, authentic, and tamper-proof while you browse the web. SSL (Secure Sockets Layer) and its modern successor TLS (Transport Layer Security) form the foundation of secure communication on today’s internet. Below are the key reasons SSL/TLS is so important:
Data Encryption:
SSL/TLS encrypts the data exchanged between your device and the server, making it unreadable to anyone who might try to intercept it. This is especially critical for sensitive information like:
-
login credentials
-
personal data
-
payment and banking details
Even if someone captures the data, they cannot decode it without the encryption key.
Confidentiality:
Encryption ensures privacy. Only the intended sender and recipient can see the actual contents of the communication. Any intercepted data looks like random gibberish to outsiders.
Authentication:
SSL/TLS verifies that you are really connected to the legitimate website—not a fake or malicious copy. This is done using a digital certificate, issued by a trusted Certificate Authority (CA). When your browser sees a valid certificate, it confirms the site’s identity and prevents impersonation attacks.
Integrity:
Beyond just hiding data, SSL/TLS also ensures it hasn’t been altered in transit. If an attacker tries to modify or inject malicious content along the way, the protocol detects the tampering immediately.
Trust and Credibility:
Websites using SSL/TLS display https:// and the padlock icon in the browser address bar. Users instinctively trust these signs of security, which boosts credibility and improves conversion rates — especially for e-commerce and login-based platforms.
Regulatory Compliance:
Many laws and industry standards require the encryption of sensitive data — for example, GDPR (Europe), HIPAA (healthcare), and PCI DSS (payment processing). Implementing SSL/TLS helps organizations meet these compliance requirements and avoid penalties.
Securing Login Credentials:
Without SSL/TLS, usernames and passwords would travel in plain text — easy for attackers to steal. Encryption locks down the authentication process, protecting user accounts from unauthorized access.
E-Commerce Protection:
Online stores rely heavily on trust. SSL/TLS protects credit card numbers, payment information, and checkout details, making secure online transactions possible.
Protection Against Man-in-the-Middle Attacks:
One of the biggest threats on unsecured networks is someone secretly sitting between the client and server. SSL/TLS blocks this by encrypting data and validating identities, making MITM attacks extremely difficult to pull off successfully.
Better Browser and Search Ranking:
Modern browsers warn users when a site is “Not Secure.” Search engines like Google also give ranking boosts to HTTPS-enabled websites. So SSL/TLS not only protects users — it can also improve SEO and visibility.
What is TLS?
TLS (Transport Layer Security) is the modern standard for securing data in transit across the internet. It ensures that any information exchanged between a client and a server is encrypted, authenticated, and protected from tampering. Although it evolved from SSL (Secure Sockets Layer), SSL is now fully deprecated — which is why today’s security stack relies entirely on TLS.
Unlike older protocols, TLS does more than encrypt traffic. It also verifies the identity of the server and provides data integrity, ensuring nothing is modified in transit. Modern versions such as TLS 1.3 offer faster handshakes, forward secrecy, and stronger cryptography by default, making them the foundation of secure communication in today’s online world.
Where TLS Is Used Today
TLS is widely used across modern internet infrastructure, including:
-
HTTPS for secure websites and web apps
-
APIs and microservices communication
-
Mobile and desktop applications
-
Email security (SMTPS, IMAPS, POP3S)
-
VPNs and cloud networking
-
HTTP/3 and QUIC traffic
In short, TLS is not just for “browsing” anymore — it secures nearly all trusted data exchanges across the modern internet.
Are SSL and TLS the same thing?
SSL and TLS are related, but they are not the same thing. SSL (Secure Sockets Layer) was the original protocol used to secure internet communications, but it is now outdated and insecure. TLS (Transport Layer Security) is its modern replacement and is the protocol actually used by all secure websites today.
Even though people still say “SSL certificate” or “SSL encryption,” what browsers and servers are really using underneath is TLS, not SSL.
What Was SSL?
SSL was created in the 1990s to secure data over the internet. However, multiple vulnerabilities were later discovered in SSL 2.0 and SSL 3.0. Because of these security flaws, SSL has been officially deprecated and is no longer considered safe.
What Is TLS?
TLS is the improved and upgraded version of SSL. It was introduced in 1999 and has continued to evolve through multiple versions (TLS 1.0, 1.1, 1.2, and today’s latest TLS 1.3). Modern TLS provides:
-
Stronger encryption
-
Better authentication
-
Protection against known SSL attacks
-
Faster and more efficient handshake (especially in TLS 1.3)
-
Forward secrecy by default
Why People Still Say “SSL”
The term “SSL” stuck around simply because:
-
It was widely used for many years
-
Certificate providers still use “SSL certificate” as a marketing term
-
Users became familiar with the phrase “SSL HTTPS”
But in practical terms:
When you see HTTPS in the browser today, it’s TLS — not SSL.
Quick Comparison
| Feature | SSL | TLS |
|---|---|---|
| Status | Deprecated | Current standard |
| Security | Vulnerable | Secure |
| Versions | SSL 2.0, 3.0 | TLS 1.0 – 1.3 |
| Used Today? | No | Yes |
| Browser Support | Disabled | Fully supported |
What are the types of SSL certificates?
SSL/TLS certificates come in different types based on how much identity verification they provide and how many domains they can secure. Choosing the right certificate depends on the level of trust your website needs and the number of domains or subdomains you want to protect.
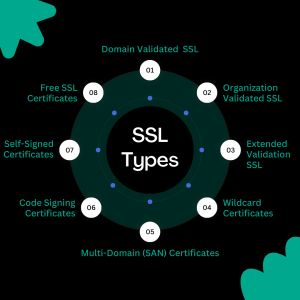
Domain Validated (DV) Certificates:
DV certificates verify only domain ownership. They are issued quickly — sometimes within minutes — because the Certificate Authority (CA) only checks if the requester controls the domain. These certificates are ideal for personal websites, blogs, or small landing pages where encryption is needed but organization identity is not critical.
Organization Validated (OV) Certificates:
OV certificates verify both domain ownership and business identity. The CA checks official business records to confirm the organization’s legal existence. This provides visitors with a higher level of trust, making OV certificates suitable for small to medium-sized businesses, SaaS platforms, and company websites.
Extended Validation (EV) Certificates:
EV certificates provide the highest level of verification. The Certificate Authority performs extensive checks on legal status, physical address, and operational existence. These are commonly used by large enterprises, banks, and e-commerce platforms.
(Note: modern browsers no longer highlight EV with a green bar, but the certificate still offers the strongest identity assurance.)
Types by Coverage (How Many Domains Are Protected)
Single-Domain Certificates
These certificates secure one fully qualified domain name, such as example.com. They are a simple and cost-effective option for standalone websites.
Wildcard Certificates:
A wildcard certificate secures a domain and all its subdomains under it, such as blog.example.com, shop.example.com, etc. This is ideal for businesses hosting multiple services or departments under the same root domain.
Multi-Domain (SAN) Certificates:
Also called SAN (Subject Alternative Name) certificates, these can secure multiple different domains under a single certificate. For example: example.com, example.org, and myshop.net can all be protected simultaneously — perfect for enterprises managing a portfolio of domains.
Unified Communications (UC) Certificates:
Similar to SAN certificates, UC certificates are designed for use with Microsoft Exchange and Microsoft Office Communication Server products. They allow secure communication for multiple domain names and services.
Code Signing Certificates:
Often confused with SSL, but they are a different type of certificate used to verify the authenticity of software, not to secure website traffic.
Self-Signed Certificates:
Generated manually without a CA. They encrypt traffic but are not trusted by browsers, so they’re mostly used in internal networks, testing, or development environments.
Free SSL Certificates:
Usually DV-level. Popular for automation, DevOps, cloud deployments, and small sites thanks to free renewal and ACME protocol support.
Should I Use SSL/TLS on My Website?
Yes — you should absolutely use SSL/TLS to secure your website or online service. In fact, it is no longer “optional” but a baseline requirement for security, trust, and search visibility. While older terminology still says “SSL,” all modern secure connections actually use TLS, the newer and more secure version of the protocol.
Why SSL/TLS Is Necessary Today
1. Protects Data in Transit
TLS encrypts the data exchanged between the browser and server, shielding sensitive information like passwords, personal details, or payment data from eavesdroppers and attackers.
2. Builds User Trust
Visitors instantly recognize secure websites by the padlock icon and the “https://” prefix. These visual signals tell users that your site is safe and trustworthy, which increases engagement and conversions.
3. Improves Search Engine Ranking
Google and other major search engines treat HTTPS as a ranking factor. Secure websites generally rank higher than non-secure ones, which helps with SEO and visibility.
4. Prevents Browser Security Warnings
Modern browsers display “Not Secure” warnings on HTTP websites. These alerts discourage visitors, reduce credibility, and increase bounce rates. TLS removes those warnings.
5. Required for Compliance
Regulations like GDPR, PCI-DSS, HIPAA, and other data protection laws require encryption for sensitive data. Using TLS helps you meet compliance requirements and avoid legal penalties.
6. Protects Login and Account Access
Without TLS, usernames and passwords travel in plain text — very easy to intercept. TLS prevents credential theft and account compromise.
7. Essential for E-Commerce
Online transactions must be encrypted to protect payment information. Without TLS, no modern payment gateway or bank will authorize transactions.
8. Boosts Performance with TLS 1.3
The latest TLS version (TLS 1.3) is not just more secure — it’s faster. It reduces handshake time and works seamlessly with newer protocols such as HTTP/2 and HTTP/3.
9. Prevents Man-in-the-Middle Attacks
TLS ensures authenticity and integrity of the connection, making it extremely difficult for attackers to tamper with or intercept data in transit.
10. Future-Proofs Your Website
TLS keeps your site aligned with evolving security standards. As the internet moves toward a fully encrypted-by-default model, HTTPS/TLS is the new normal.
Final Verdict
Yes, you should absolutely use TLS (commonly called SSL). It protects your users, improves your search ranking, prevents browser warnings, and is now a universal standard for trustworthy websites and online applications.
Is SSL/TLS Good for SEO?
Yes — using SSL/TLS (HTTPS) is good for SEO, and in today’s search landscape it is no longer optional. Google treats HTTPS as a ranking signal, and unsecured (HTTP) websites are actively flagged as “Not Secure” in modern browsers, which leads to lower trust and higher bounce rates — both of which hurt SEO performance.
Why HTTPS Improves SEO
1. Official Google Ranking Signal
Google has confirmed that HTTPS is part of its ranking algorithm. While it started as a “light boost,” today websites without HTTPS can be pushed down in search results because they are considered unsafe.
2. Better User Trust & Engagement
Users are more likely to stay on a website when they see the padlock icon and a secure connection. More trust = longer visits and lower bounce rates — both positive SEO signals.
3. Avoids Browser Security Warnings
Chrome, Firefox, Edge, and Safari now label HTTP websites as “Not Secure.” These warnings scare users away before they even interact with your content, killing engagement and rankings.
4. Enables Faster Protocols (HTTP/2 & HTTP/3)
Modern performance features like HTTP/2 and HTTP/3 (QUIC) require TLS. These protocols improve loading speed, especially on mobile — and site speed is a major SEO factor.
5. Supports Core Web Vitals & Trust Signals
HTTPS is part of the broader trust ecosystem used by search engines. It supports Google’s EEAT (Experience, Expertise, Authoritativeness, Trustworthiness), which directly affects visibility for informational and transactional content.
6. Required for Compliance & Professional Credibility
Regulations like GDPR and PCI-DSS expect encryption by default. When users (and search engines) see TLS enabled, it signals professionalism and legitimacy.
Final Verdict
HTTPS is not just “good for SEO” — it is a minimum requirement for ranking, trust, performance, security, and future-proofing your website.
Without SSL/TLS, your site will:
-
trigger warnings
-
lose visitor trust
-
rank lower
-
miss modern performance upgrades like HTTP/3
How can I tell if my website has SSL?
You can easily check whether your website is secured with SSL/TLS by looking at the URL, browser indicators, or using online verification tools. Here are the most reliable ways to confirm if HTTPS is enabled and working correctly:
1. Check the URL (HTTPS)
Look at your website’s address in the browser. If it starts with https:// instead of http://, your site is using SSL/TLS encryption.
2. Look for the Padlock Icon
Modern browsers display a padlock icon next to the URL when the connection is secure. Clicking the padlock will show certificate details, including who issued it and whether it is valid.
3. Check for “Not Secure” Warnings
If your site does not have SSL/TLS (or if the certificate is expired), browsers like Chrome will display a “Not Secure” warning. On mobile, this warning is even more prominent.
No padlock = unencrypted
Warning = certificate missing or expired
4. Use an SSL Checking Tool
Tools like SSL Labs, WhyNoPadlock, and built-in hosting dashboards can verify:
-
whether your certificate is installed correctly,
-
what type it is (DV/OV/EV),
-
and when it will expire.
These tools are especially helpful for avoiding downtime caused by expired certificates.
5. View Certificate Details
You can view the full certificate by clicking the padlock and selecting “Connection is secure” → “Certificate” (wording varies slightly by browser). This shows:
-
Issuer (which CA provided it)
-
Validity period
-
Expiration date
-
Domain name(s) covered
Important Note About EV Certificates
Older versions of browsers used to show a green address bar for EV (Extended Validation) certificates. That design has been retired, so EV no longer looks “green” — it simply shows as a standard HTTPS connection with enhanced identity details in the certificate view, not in the address bar.
Quick Summary
| Indicator | Meaning |
|---|---|
https:// + padlock |
Secure (TLS active) |
| “Not Secure” label | No valid certificate |
| Certificate shows issuer + validity | TLS correctly installed |
| Expired certificate | Triggers warnings / SEO penalty |
Can an SSL/TLS Certificate Be Used on Multiple Servers?
Yes — an SSL/TLS certificate can be installed on multiple servers, as long as the certificate matches the domain(s) and the private key is correctly shared across those servers. This is common in environments with load balancing, high availability clusters, cloud hosting, and CDN-based deployments.
However, whether a certificate can protect multiple domains or subdomains depends on the type of certificate you use.
Certificates and Multi-Server Usage
| Certificate Type | Multi-Server Use | Covers Multiple Domains/Subdomains? |
|---|---|---|
| Single-Domain | ✅ Yes | ❌ No |
| Wildcard | ✅ Yes | ✅ All subdomains |
| Multi-Domain (SAN) | ✅ Yes | ✅ Multiple domains |
| EV/OV/DV (any validation) | ✅ Yes | ✅ Depends on scope |
Modern CAs generally allow unlimited server installations as long as you control the private key.
Single Domain SSL Certificate:
A single domain SSL certificate is issued for a specific domain (e.g., www.example.com). It is valid only for that single domain and cannot be used for other domains or subdomains.
Wildcard SSL Certificate:
A wildcard SSL certificate is issued for a main domain and all its subdomains. For example, a wildcard certificate for “*.example.com” is valid for www.example.com, blog.example.com, and any other subdomain under example.com.
Multi-Domain (SAN) SSL Certificate:
A Multi-Domain SSL certificate, also known as a Subject Alternative Name (SAN) certificate, can secure multiple domains and subdomains. Each domain or subdomain must be listed in the certificate’s Subject Alternative Name field. This type of certificate is versatile and allows securing multiple websites with a single certificate.
Unified Communications (UC) SSL Certificate:
Similar to Multi-Domain certificates, Unified Communications (UC) certificates are designed specifically for Microsoft Exchange and Microsoft Office Communication Server products. They support multiple domain names and services.
Important Considerations:
1. Private Key Security
To use the same certificate on multiple servers, the same private key must be installed everywhere. This means you need a secure key distribution process. If the key leaks, every server using it is at risk.
2. Load Balancers and CDNs
In many modern architectures, TLS termination doesn’t happen on the origin server — it happens on an edge network like Cloudflare, AWS CloudFront, or a load balancer. The same certificate is reused across all nodes automatically.
3. ACME / Automation (Modern Trend)
Tools like Let’s Encrypt and ZeroSSL allow automatic installation and renewal across multiple servers using the ACME protocol. This is now standard practice for cloud-native deployments and Kubernetes clusters.
Legacy Note: UC Certificates
“Unified Communications” certificates were once marketed separately for Microsoft Exchange or Office Communications servers. Today, they’re simply SAN (multi-domain) certificates — the same technology, just with an older name.
Final Answer
Yes — you can use an SSL/TLS certificate on multiple servers.
But:
-
If you need multiple domains → use SAN
-
If you need many subdomains → use Wildcard
-
If you need identity assurance → OV/EV
-
Just one host → Single-domain is enough
What happens when an SSL certificate expires?
When an SSL/TLS certificate expires, your website can no longer be considered secure by browsers, and users are blocked or warned from proceeding. While the server may still technically support encryption, browsers stop trusting the connection, which makes the site appear unsafe and unreliable.
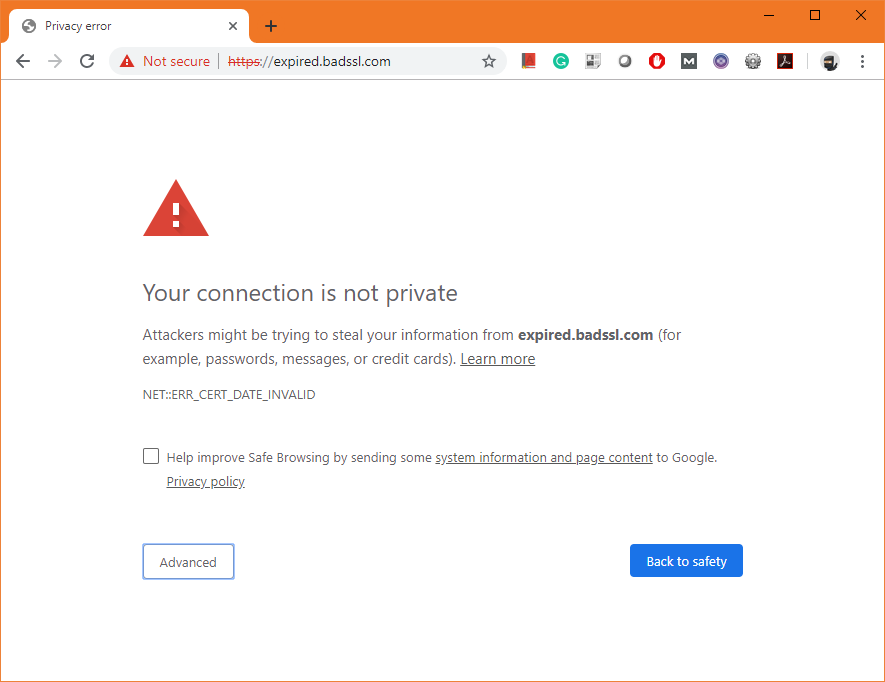
1. Browsers Show a Security Warning
Modern browsers display a full-screen warning such as “Your connection is not private” or “Certificate Expired.” Most users will leave immediately, which leads to a sharp drop in traffic and conversions.
2. Loss of Trust and Credibility
Visitors are unlikely to share personal or payment information on a site with an expired certificate. For e-commerce, this can instantly kill checkout conversions.
3. Potential SEO Impact
Search engines like Google treat expired certificates as a security failure. As a result:
-
Your site may lose ranking
-
“Not Secure” labels can appear in SERPs
-
Bounce rate increases (which further harms SEO)
4. Payment Gateways Stop Working
Most payment processors require a valid TLS certificate. With an expired cert, online transactions may fail or be blocked entirely.
5. Risk of Exploitation (MITM Attacks)
Since the certificate is no longer trusted, attackers could impersonate the site or intercept traffic more easily through man-in-the-middle attacks, especially on public or insecure networks.
Avoiding Expired Certificate Problems
To prevent downtime and trust loss:
-
Enable auto-renewal (via Let’s Encrypt, ZeroSSL, or your hosting provider)
-
Monitor certificate expiration dates
-
Use ACME automation for multi-server environments
-
Keep CA contact details updated so renewal alerts are received
Most modern platforms (Cloudflare, AWS, cPanel, etc.) now automate renewals, eliminating most manual maintenance.
Final Takeaway
An expired SSL/TLS certificate doesn’t just “turn off encryption” — it breaks trust. Browsers block access, users leave, SEO suffers, and payments can fail.
Staying ahead of certificate expiration is essential for a secure, reliable, and trustworthy online presence.
What are the key principles in SSL/TLS certificate technology?
SSL/TLS certificate technology is based on several key principles to provide secure and encrypted communication over the internet. Here are the fundamental principles in SSL/TLS certificate technology:
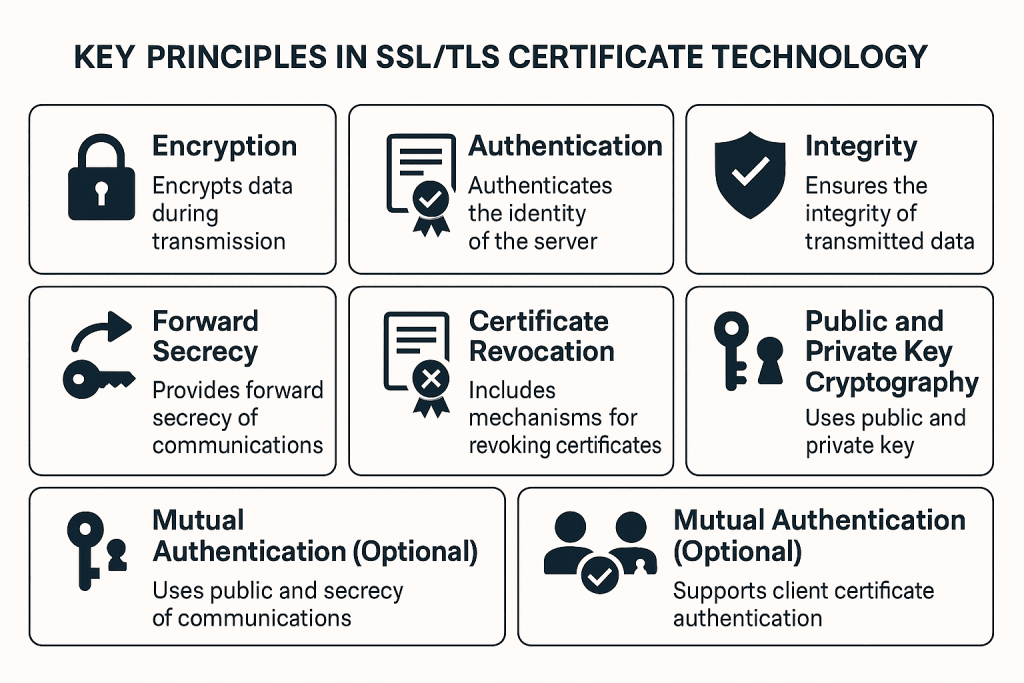
Encryption:
Principle: The primary purpose of SSL/TLS is to encrypt data during transmission, ensuring that sensitive information remains confidential and secure.
Implementation: SSL/TLS uses cryptographic algorithms to encrypt the data exchanged between the client and server. Symmetric key encryption is often used for the actual data transfer, while asymmetric key encryption is used during the initial handshake to establish a secure connection.
Authentication:
Principle: SSL/TLS provides a mechanism for authenticating the identity of the server to the client, assuring users that they are connecting to a legitimate and trusted website.
Implementation: The server presents a digital certificate during the handshake process. The certificate is issued by a trusted Certificate Authority (CA) and includes the server’s public key. The client verifies the certificate to ensure its authenticity.
Integrity:
Principle: SSL/TLS ensures the integrity of the transmitted data, preventing tampering or modification during transit.
Implementation: Hash functions are used to create message digests (hashes) of the data. These digests are included in the exchanged messages, and both the client and server verify them to detect any alterations.
Key Exchange:
Principle: SSL/TLS establishes a secure session key that is used for encrypting and decrypting data during the secure communication session.
Implementation: The client and server perform a key exchange during the handshake process. The symmetric session key is derived from a pre-master secret, which is exchanged securely.
Forward Secrecy:
Principle: Forward secrecy ensures that even if the private key of the server is compromised in the future, past communications remain secure.
Implementation: Some SSL/TLS configurations support forward secrecy by using ephemeral key exchange mechanisms. This means that the session key is not derived solely from long-term keys but includes temporary keys exchanged during the handshake.
Certificate Revocation:
Principle: SSL/TLS includes mechanisms for revoking certificates if they are compromised or if the entity’s status changes.
Implementation: Certificate Revocation Lists (CRLs) and Online Certificate Status Protocol (OCSP) are used to check the current status of certificates. Browsers and clients can verify whether a certificate has been revoked by checking these sources.
Public and Private Key Cryptography:
Principle: Asymmetric key cryptography is used for secure key exchange during the handshake, while symmetric key cryptography is employed for efficient data encryption and decryption during the actual data transfer.
Implementation: The server’s public key is included in the digital certificate and shared during the handshake. The private key, kept secret by the server, is used to decrypt messages encrypted with the public key.
Mutual Authentication (Optional):
Principle: In some cases, SSL/TLS supports mutual authentication, where the client also presents a certificate to the server for verification.
Implementation: Mutual authentication requires the client to have a digital certificate. This is less common on the web but is used in scenarios like client-certificate authentication in enterprise environments.
Who validates SSL/TLS certificates?
SSL/TLS certificates are validated and issued by Certificate Authorities (CAs)—trusted third-party organizations responsible for confirming the identity of websites and securely signing their certificates. These CAs form the backbone of the public key infrastructure (PKI) that powers secure internet communication.
What Certificate Authorities Do
-
Verify Domain and Identity
The CA checks whether the requester controls the domain. For OV and EV certificates, it also verifies the legal identity of the organization. -
Authenticate Ownership
Validation can be done through DNS records, email verification, or automated ACME challenges (used by Let’s Encrypt and ZeroSSL). -
Issue the Certificate
Once verified, the CA issues a certificate signed with its private key. Browsers can then trust the website because they trust the CA that signed it. -
Maintain Trust (Chain of Trust)
CAs use root and intermediate certificates to form a trust chain. Browsers and operating systems include these trusted roots by default. -
Revoke Compromised Certificates
If a certificate is misused or compromised, the CA can revoke it using mechanisms like OCSP (Online Certificate Status Protocol).
Modern Validation Also Involves Browsers
It’s not just the CA that decides trust.
Browsers (Chrome, Firefox, Safari, Edge) and operating systems (Windows, macOS, Android, iOS) maintain their own root trust programs. They can:
-
accept or distrust a CA
-
enforce stricter rules
-
log all certificates in Certificate Transparency (CT) logs
If a CA fails security audits, browsers can remove it — instantly distrusting millions of certificates (this happened to Symantec).
Examples of Trusted CAs Today
-
DigiCert
-
Let’s Encrypt
-
Sectigo (formerly Comodo)
-
GlobalSign
-
IdenTrust
-
ZeroSSL
- SSL.com
(Symantec roots are no longer trusted — DigiCert acquired their PKI.)
Final Summary
SSL/TLS certificates are validated by Certificate Authorities, but they are ultimately enforced and trusted by browsers and operating systems through public key infrastructure and certificate transparency logs.
Without this ecosystem of CAs + browser trust programs working together, HTTPS would not be possible.
What is the validity period for the SSL/TLS certificate?
Publicly trusted SSL/TLS certificates today have a maximum validity of 398 days (approximately 13 months). This limit is enforced not just by Certificate Authorities, but also by browser vendors and the CA/Browser Forum to improve security and reduce the risk of long-lived compromised certificates.
Why the Limit Was Reduced
Historically, SSL/TLS certificates could last 3 or even 5 years. Over time, the industry shortened this limit to make key rotation more frequent and reduce the attack window if a certificate or private key was ever compromised.
In 2020, Apple first announced that Safari would only trust certificates valid for 398 days or less. Soon after, Chrome, Firefox, and Edge adopted the same policy, making 13 months the universal standard.
Current Validity Rules (2025)
| Certificate Type | Maximum Validity |
|---|---|
| Public DV/OV/EV | 398 days (13 months) |
| Multi-year plans | Allowed, but renewed annually (reissued each year) |
| Free (Let’s Encrypt / ZeroSSL) | 90 days, auto-renewed |
| Private/internal certs | Custom — can be longer depending on internal PKI |
Multi-Year Certificates: How They Work Now
Some CAs still sell “multi-year” plans, but these are reissued annually to comply with the 398-day rule. You’re essentially paying upfront for multiple renewals, not getting a multi-year cert.
The Industry Trend: Automation
Modern SSL/TLS deployments rely on ACME-based auto-renewal (e.g., Let’s Encrypt, ZeroSSL), especially in cloud and container environments. This eliminates manual renewals and prevents expiration-related outages.
What is included in an SSL/TLS certificate?
An SSL/TLS certificate contains the information needed for a browser or client to verify the identity of a website and establish an encrypted connection. It is a digital identity card for a server, backed by a trusted Certificate Authority (CA) within the global PKI (Public Key Infrastructure).
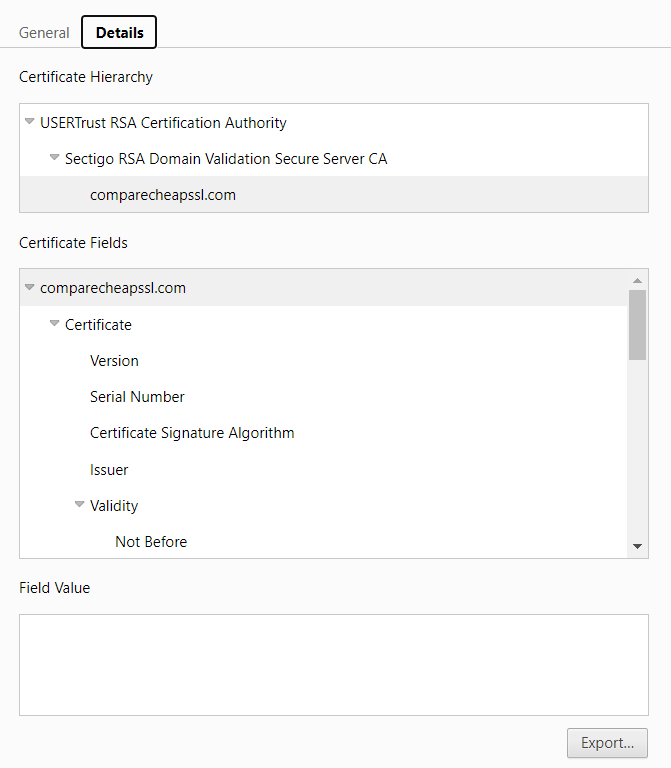
Here are the key elements included in a modern SSL/TLS certificate:
1. Public Key
The certificate contains the public key that is used during the TLS handshake. The matching private key remains securely stored on the server and is never shared.
2. Certificate Holder Information
Details about the domain or organization the certificate belongs to, including:
-
Common Name (CN) → main domain
-
Organization (O) → company (OV/EV only)
-
Country / Location details (for OV/EV)
3. Validity Period
The start and end dates indicating how long the certificate is valid. Today, publicly trusted certificates are limited to a maximum of 398 days.
4. Issuer (Certificate Authority)
Information about the CA that issued the certificate, plus its digital signature confirming authenticity.
5. Digital Signature
A cryptographic signature from the CA that proves the certificate has not been altered and is trusted.
6. Key Usage & Extended Key Usage
Indicates how the key can be used — typically for:
-
server authentication
-
key encipherment
-
digital signatures
7. Subject Alternative Names (SANs)
Lists additional domains or subdomains the certificate secures. This is used for multi-domain and wildcard-style coverage.
8. Revocation Information
Details on how the certificate’s status can be checked (via OCSP or CRL endpoints), in case it is revoked before expiration.
9. Certificate Version & Extensions
Most modern certificates use X.509 v3, with extensions like SANs, key usage, and policy information.
10. Chain of Trust Reference
The certificate includes identifiers linking it to intermediate and root certificates. Browsers follow this “chain of trust” to verify authenticity.
Modern Additions (Post-2023)
In today’s TLS ecosystem, certificates also participate in:
-
Certificate Transparency (CT) logs – public logs required by browsers to prevent fraudulent certificates
-
Modern signature algorithms like RSA 2048+ and ECC/ECDSA, which improve performance


