Every time a browser connects to an HTTPS website, a silent cryptographic negotiation happens in milliseconds. This process is called the TLS handshake. Most explanations stop at a high level overview, but to truly understand performance, security, and common SSL errors, we need to look deeper at what actually happens on the wire.
In this detailed guide, we will break down the TLS handshake at packet level, examine real examples, explain how keys are derived, and analyze how TLS 1.3 changed everything compared to TLS 1.2. Whether you are a developer, security engineer, DevOps administrator, or someone troubleshooting handshake failures, this guide will give you technical clarity without unnecessary complexity.
What Is a TLS Handshake in Technical Terms
A TLS handshake is the process where a client and server:
- Agree on a TLS version
- Select a cipher suite
- Authenticate the server
- Exchange key material
- Derive symmetric encryption keys
After the handshake completes, encrypted application data begins flowing over the established secure channel.
At packet level, this entire exchange occurs after the TCP three way handshake but before any HTTP request is transmitted.
To understand this clearly, we must first look at the network layer sequence.
Where TLS Fits in the Network Stack
TLS operates above TCP and below HTTP. The sequence typically looks like this:
- DNS resolution
- TCP three way handshake
- TLS handshake
- HTTP request and response
The TLS handshake is independent of HTTP. That means APIs, SMTP, IMAP, and other protocols can also use TLS.
Understanding this layering helps when diagnosing errors such as SSL handshake failure or protocol version mismatch. If TCP fails, TLS never starts. If TLS fails, HTTP never executes.
Step Zero: TCP Three Way Handshake
Before TLS even begins, TCP establishes a reliable connection.
The packet sequence is:
- SYN from client
- SYN ACK from server
- ACK from client
Only after TCP confirms a reliable transport channel does TLS start negotiating encryption.
This separation is important when analyzing packet captures in Wireshark. TCP packets are visible first. TLS handshake records follow immediately after.
TLS 1.2 Handshake Packet Level Breakdown
Let us now examine what happens at packet level during a TLS 1.2 handshake.
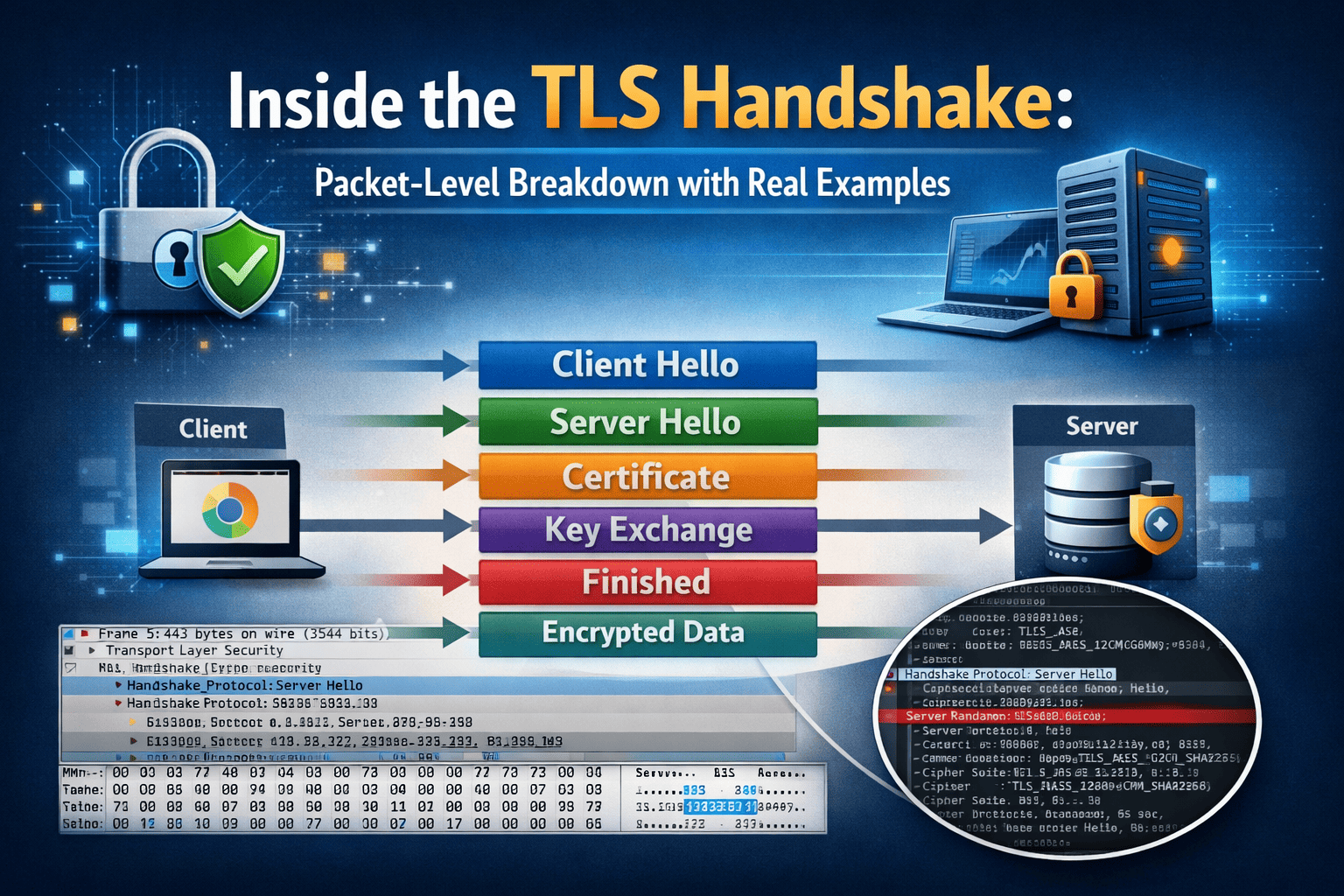
1. Client Hello Packet
The first TLS record sent by the client contains:
- Supported TLS versions
- Random value
- Supported cipher suites
- Compression methods
- Extensions such as SNI
Packet level structure includes:
- Record Layer Header
- Handshake Protocol Header
- ClientHello payload
The random value is critical because it contributes to session key generation later.
SNI or Server Name Indication allows multiple domains to share the same IP address by indicating which hostname the client wants to access.
2. Server Hello Packet
The server responds with:
- Selected TLS version
- Selected cipher suite
- Server random value
- Session ID
This tells the client which cryptographic configuration will be used.
At this stage, the handshake is still unencrypted.
3. Certificate Packet
The server sends its X.509 certificate chain. This includes:
- Server certificate
- Intermediate certificates
- Public key
The client validates:
- Certificate expiration
- Trusted Certificate Authority
- Domain name match
If validation fails, the browser displays a certificate warning.
4. Server Key Exchange
If using ephemeral Diffie Hellman, the server sends key exchange parameters.
This step is where forward secrecy becomes possible. Ephemeral keys are generated for each session rather than using static keys.
5. Client Key Exchange
The client sends its key exchange parameters.
At this point, both sides have enough information to derive a shared secret.
6. Change Cipher Spec and Finished
Both client and server send ChangeCipherSpec messages.
From this moment onward, communication becomes encrypted using symmetric encryption derived from the shared secret.
Only after this stage does the HTTP request get transmitted securely.
Real Packet Example: TLS 1.2 Master Secret Derivation
In TLS 1.2, the shared secret is derived from:
- Client random
- Server random
- Premaster secret
The premaster secret is generated by the client and encrypted using the server’s public key.
Using a pseudorandom function, both sides compute:
Master Secret = PRF(premaster secret, client random, server random)
From the master secret, session keys for encryption and integrity are derived.
This multi step derivation increases computational overhead and adds latency due to extra round trips.
TLS 1.3 Handshake Packet Level Breakdown
TLS 1.3 redesigned the handshake for efficiency and security.
1. Client Hello with Key Share
Unlike TLS 1.2, the client immediately includes a key share.
This eliminates the need for a separate ServerKeyExchange message later.
The ClientHello includes:
- Supported versions
- Supported cipher suites
- Key share extension
- Supported groups
- Signature algorithms
This allows the server to immediately compute shared keys.
2. Server Hello
The server responds with:
- Selected cipher suite
- Its own key share
- Selected TLS version
After this exchange, encryption keys can already be derived.
3. Encrypted Extensions
In TLS 1.3, most handshake messages after ServerHello are encrypted.
This includes:
- EncryptedExtensions
- Certificate
- CertificateVerify
- Finished
This dramatically reduces metadata exposure compared to TLS 1.2.
Key Derivation in TLS 1.3
TLS 1.3 uses HKDF, a more modern key derivation function.
Instead of a single master secret, TLS 1.3 derives multiple traffic secrets in stages:
- Early secret
- Handshake secret
- Application traffic secret
This layered derivation improves compartmentalization and forward secrecy.
Each stage depends on ephemeral Diffie Hellman key exchange, making static RSA key exchange obsolete.
Comparing Packet Flow: TLS 1.2 vs TLS 1.3
TLS 1.2:
ClientHello → ServerHello → Certificate → ServerKeyExchange → ClientKeyExchange → ChangeCipherSpec → Finished
Requires two round trips.
TLS 1.3:
ClientHello with key share → ServerHello with key share → Encrypted messages → Finished
Requires one round trip.
Reducing one round trip significantly improves performance, especially on high latency networks.
0 RTT at Packet Level
TLS 1.3 introduces early data.
When resuming a session:
- Client sends ClientHello
- Includes session ticket
- Immediately sends encrypted application data
This early data is encrypted but not fully forward secure until handshake completes.
Servers must carefully configure replay protection mechanisms.
Analyzing TLS Handshake in Wireshark
To inspect real packet level data:
- Capture traffic
- Filter using tcp.port == 443
- Expand TLS record layer
In TLS 1.2, you will see visible handshake types.
In TLS 1.3, after ServerHello, handshake messages are marked as encrypted.
This visual difference makes it easy to distinguish protocol versions during packet analysis.
Common Handshake Failures at Packet Level
Understanding packets helps diagnose errors.
If ClientHello is sent but no ServerHello returns, the issue may be:
- Firewall blocking traffic
- TLS version unsupported
- Cipher mismatch
If Certificate packet is sent but browser rejects it:
- Expired certificate
- Untrusted CA
- Incorrect hostname
If ChangeCipherSpec never appears:
- Key derivation failure
- OpenSSL version mismatch
Packet analysis often reveals misconfiguration faster than server logs.
Performance Implications of Packet Reduction
Reducing one round trip in TLS 1.3 may appear small, but over millions of connections it translates to:
- Lower server CPU load
- Reduced latency
- Faster API responses
- Improved mobile experience
For API heavy applications, microservices, and CDNs, this improvement is measurable in real performance benchmarks.
Security Improvements Visible at Packet Level
TLS 1.3 encrypts:
- Certificates
- Extensions
- Handshake metadata
In TLS 1.2, observers could inspect handshake messages to fingerprint server configurations.
TLS 1.3 reduces fingerprinting exposure.
This improves privacy and reduces reconnaissance opportunities for attackers.
Why Packet Level Understanding Matters
Most administrators enable TLS 1.3 without understanding what changed internally.
However, packet level awareness helps when:
- Debugging SSL handshake errors
- Diagnosing performance bottlenecks
- Hardening cipher suites
- Auditing compliance
- Investigating security incidents
Security is not just about enabling a protocol. It is about understanding how it behaves under real network conditions.
Final Thoughts
The TLS handshake is more than a simple negotiation. It is a carefully engineered cryptographic exchange designed to balance performance, security, and compatibility.
TLS 1.2 introduced strong encryption to the modern web but required careful configuration and multiple handshake steps.
TLS 1.3 simplified the protocol, reduced packet exchanges, removed insecure algorithms, and encrypted more metadata.
At packet level, the difference is visible, measurable, and meaningful.
If you manage servers, operate APIs, deploy CDNs, or troubleshoot SSL issues, understanding handshake internals gives you a strategic advantage.
Encryption is not magic. It is math, packets, and protocol design working together in milliseconds to secure billions of connections every day.
Frequently Asked Questions About the TLS Handshake
What exactly happens during a TLS handshake?
During a TLS handshake, a client and server negotiate the cryptographic parameters required to establish a secure connection. After the TCP connection is established, the client sends a ClientHello message containing supported protocol versions, cipher suites, and random values. The server responds with a ServerHello message selecting the agreed parameters and sends its digital certificate. Both parties then exchange key material, derive shared symmetric session keys, and confirm encryption readiness through Finished messages. Once this process completes, encrypted application data such as HTTP requests can securely flow between both sides.
Why does the TLS handshake occur before HTTP communication?
TLS operates below HTTP in the network stack. Before any HTTP request such as GET or POST can be transmitted, a secure encrypted tunnel must be established. The handshake ensures that encryption keys are securely negotiated and that the server identity is verified using its certificate. Without this step, HTTP traffic would travel in plaintext and be vulnerable to interception or tampering.
What is the difference between the TCP handshake and the TLS handshake?
The TCP handshake establishes a reliable communication channel between client and server using SYN, SYN ACK, and ACK packets. It ensures both endpoints can exchange data. The TLS handshake happens after TCP and establishes encryption and authentication. TCP guarantees delivery reliability, while TLS guarantees confidentiality, integrity, and identity verification.
What information is contained in the ClientHello packet?
The ClientHello packet contains supported TLS versions, supported cipher suites, a client random value, compression methods, and optional extensions such as Server Name Indication or supported groups. In TLS 1.3, it also includes key share information for immediate key exchange. This packet initiates the secure negotiation process and provides the server with all information necessary to choose compatible cryptographic parameters.
Why is Server Name Indication important in modern hosting?
Server Name Indication, commonly known as SNI, allows a client to specify the hostname it is attempting to connect to during the TLS handshake. This enables multiple domains to share the same IP address while serving different SSL certificates. Without SNI, each domain would require a dedicated IP address for HTTPS, which is inefficient and costly.
How are encryption keys generated during the TLS handshake?
Encryption keys are generated through cryptographic key exchange algorithms such as Diffie Hellman or Elliptic Curve Diffie Hellman. In TLS 1.2, a premaster secret is combined with client and server random values to derive a master secret using a pseudorandom function. In TLS 1.3, keys are derived using HKDF and ephemeral key exchange, creating multiple traffic secrets in stages. The final result is symmetric session keys used for fast and secure data encryption.
Why does TLS 1.3 require fewer packets than TLS 1.2?
TLS 1.3 reduces handshake complexity by eliminating separate key exchange messages and including key share information directly in the ClientHello packet. After receiving the ServerHello, encryption keys can be derived immediately. This eliminates an entire round trip, improving connection speed and reducing latency, especially on high latency networks.
What is encrypted during the TLS 1.3 handshake?
In TLS 1.3, most handshake messages after the ServerHello are encrypted. This includes certificate transmission, extensions, and verification messages. In contrast, TLS 1.2 exposes more handshake metadata in plaintext. Encrypting these messages improves privacy and reduces information leakage that attackers could use for reconnaissance or fingerprinting.
What causes a TLS handshake failure?
TLS handshake failures typically occur when the client and server cannot agree on a common protocol version or cipher suite. Other causes include expired certificates, invalid certificate chains, incorrect hostname validation, firewall interference, or outdated server software. Analyzing packet captures often reveals at which stage the negotiation failed, allowing faster troubleshooting.
How can I capture and inspect TLS handshake packets?
You can use network analysis tools such as Wireshark to capture and inspect TLS handshake packets. By filtering traffic on port 443, you can view ClientHello and ServerHello messages, observe certificate exchanges, and determine whether TLS 1.2 or TLS 1.3 is being used. In TLS 1.3, handshake messages become encrypted shortly after the ServerHello, making the protocol version identifiable.
What is forward secrecy and how does it relate to the handshake?
Forward secrecy ensures that if a server’s private key is compromised in the future, previously recorded encrypted sessions remain secure. It is achieved using ephemeral key exchange algorithms. In TLS 1.2, forward secrecy depends on cipher suite selection. In TLS 1.3, it is mandatory and built into the protocol design.
What is Zero Round Trip Time in TLS 1.3?
Zero Round Trip Time, often called 0 RTT, allows returning clients to resume a previous session and send encrypted data immediately without waiting for the full handshake to complete. This reduces latency for repeat visitors. However, early data can be vulnerable to replay attacks, so it must be configured carefully depending on application sensitivity.
How does the TLS handshake impact website performance?
The TLS handshake contributes to connection latency before content begins loading. TLS 1.2 requires two round trips, while TLS 1.3 requires only one. Reducing round trips decreases Time to First Byte and improves user experience, especially for mobile users and global audiences. For high traffic applications and APIs, this performance improvement can significantly reduce overall response times.
Can TLS handshake packets be decrypted in Wireshark?
TLS handshake packets can only be decrypted if you have access to session keys or private keys and proper configuration within Wireshark. Without these keys, encrypted portions of the handshake in TLS 1.3 cannot be read. This encryption ensures confidentiality and protects sensitive negotiation data.
Why is understanding packet level TLS important for administrators?
Understanding TLS at packet level helps administrators diagnose handshake failures, analyze performance bottlenecks, verify cipher suite configurations, audit compliance requirements, and investigate security incidents. Rather than relying solely on error messages, packet analysis provides precise insight into where and why negotiation fails.
Does every HTTPS request require a full TLS handshake?
Not necessarily. Modern browsers use session resumption techniques such as session IDs or session tickets to avoid repeating full handshakes. TLS 1.3 also supports 0 RTT resumption. These mechanisms reduce computational overhead and improve performance for returning visitors.