Last updated: Nov 2, 2025
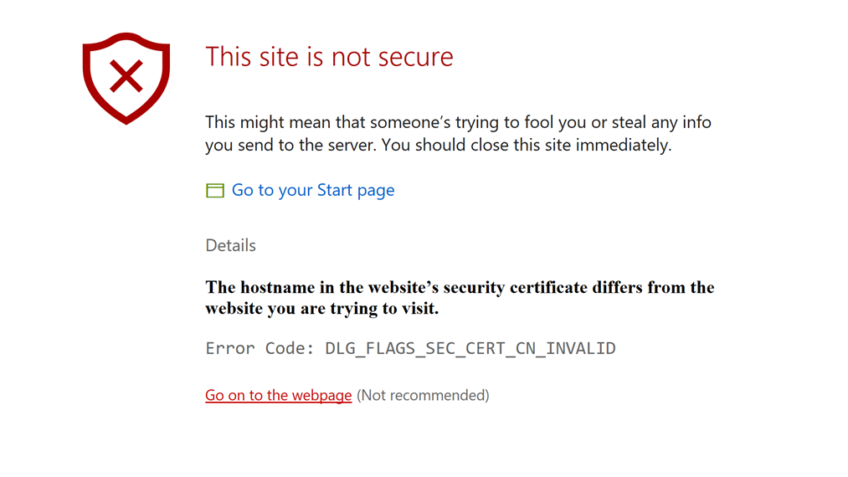
You’ve secured your website with HTTPS, installed an SSL certificate, and expect users to see the reassuring padlock icon in their browser. Instead, they’re met with a full-screen warning like “Your connection is not private”, “This site can’t provide a secure connection”, or “NET::ERR_CERT_AUTHORITY_INVALID”. Even worse, some users may be blocked entirely, search rankings begin to drop, and analytics show traffic plummeting.
These errors don’t just scare users — they destroy trust, harm conversion rates, and drastically impact SEO, especially now that Google uses HTTPS as a ranking factor.
The underlying issue? Even if a site appears fully secured with HTTPS, the smallest SSL/TLS misconfiguration can trigger browser errors. These may include:
-
An expired or incorrectly installed SSL certificate
-
Mixed content — loading insecure images or scripts on an HTTPS page
-
Incorrect server setup on Apache, Nginx, IIS, or cloud hosting
-
Outdated TLS protocol versions (e.g., only supporting TLS 1.0 or SSLv3)
-
Certificate authority trust failures, especially with self-signed or unchained certs
-
Improper redirects, CDN conflicts, or handshake issues
These are solvable — once you know how to identify what’s really going wrong.
This in-depth guide is built for two key audiences:
Website Visitors (Non-Technical Users)
You’ll learn what browser warnings really mean, whether it’s safe to proceed, and what quick steps you can take to ensure your data is protected. If you’re not ready to take risks, we’ll show you how to notify the website owner so they can fix things on their end.
Webmasters, Developers, and Server Admins
You’ll get a complete troubleshooting framework that includes:
-
A breakdown of every major HTTPS error code and its root cause
-
Fixes for popular servers like Apache, Nginx, and IIS
-
Solutions for SiteGround, Cloudflare SSL errors, WordPress mixed content issues, and cPanel misconfigurations
-
Real examples of server commands, config changes, SSL chain repair, and browser-specific diagnosis
-
Preventive strategies to avoid future downtime, including automated renewals and SSL health monitoring
You’ll walk away with the confidence to debug, fix, and prevent SSL/TLS security errors at scale — and a full checklist to ensure that your website stays trusted, user-friendly, and SEO-ready.
💡 Whether you’re a site visitor or the technical owner, this guide takes a do-not-skip approach: we solve both the symptom (browser error message) and the root cause (technical misconfig).
Understanding Security Error Codes on HTTPS Websites
When a browser raises a security warning while loading an HTTPS site, it’s an indication that the connection between the client (the user’s browser) and the server (your website) has failed some aspect of SSL/TLS verification. These browser warnings and error codes are not random — they result from broken trust in the secure connection.
Understanding what these messages mean is the first step toward solving the problem, whether you’re an end user or a site owner.
What Happens Behind the Scenes?
When a browser attempts to load a website via HTTPS (https://example.com), it expects four things to happen:
-
Valid SSL Certificate
-
The certificate must not be expired, revoked, or self-signed unless explicitly trusted.
-
The certificate must match the domain name (
example.com, not some-other-domain.com).
-
-
Complete Certificate Chain
-
In most cases, your server needs to send not just your SSL certificate, but also intermediate CA certificates that connect it to a trusted root.
-
-
Modern TLS Protocol Support
-
Browsers are dropping support for older protocols like TLS 1.0 and 1.1.
-
If your server doesn’t support TLS 1.2+ or uses deprecated cipher suites, users may be blocked.
-
-
Fully Secure Content
-
Every script, image, stylesheet, iframe, or font must be loaded via HTTPS. One insecure resource triggers mixed content warnings or blocked content.
-
When any of these steps fail, the browser sends up a flare — a security error code or full-page warning.
How to Decipher the Error Message
Every error message is a clue to the exact part of the HTTPS chain that broke. Here’s a preview of what common error codes mean:
| Error Code (Chrome/Firefox) | Meaning | Most Likely Cause |
|---|---|---|
NET::ERR_CERT_DATE_INVALID |
Expired certificate | SSL not renewed in time |
NET::ERR_CERT_COMMON_NAME_INVALID |
Hostname mismatch | Wrong domain on cert, or subdomain missing |
NET::ERR_CERT_AUTHORITY_INVALID |
Not trusted / self-signed certificate | Using private CA or missing intermediate cert |
ERR_SSL_PROTOCOL_ERROR |
SSL/TLS handshake failed | Outdated protocol or cipher mismatch |
SSL_ERROR_BAD_CERT_DOMAIN (Firefox) |
Certificate domain mismatch | Redirecting to a different domain |
| “Mixed Content Blocked” | Site is HTTPS but loads HTTP resources | Images/scripts/fonts over insecure link |
Each browser has slight variations in how these errors are worded, but the underlying causes are consistent.
If You’re a Website Visitor
Knowing what the error means helps you decide whether it’s safe to continue. For example:
-
If the issue is an expired certificate, it’s likely the site admin forgot to renew.
-
If the certificate is self-signed or untrusted, it might indicate a fake site or an unsafe network.
Later in this guide, we’ll walk you through a simple checklist to determine whether it’s safe to proceed — or best to exit immediately.
If You’re a Webmaster or Developer
Understanding these security errors in depth is critical to troubleshooting. This guide will explain how to:
-
Use tools like
openssl s_client, curl, SSL Labs, and browser developer tools to diagnose issues -
Fix certificate chain issues (e.g., missing intermediates or incorrect file formats)
-
Configure HTTPS correctly in Apache, Nginx, Cloudflare, and cPanel
-
Resolve mixed content at scale (e.g., WordPress migrations)
What to Do When You See Security Error Codes as a Website Visitor
You’re browsing the web, and suddenly, instead of the page you expected, your screen turns red or yellow, warning you:
“Your connection is not private.”
“Attackers might be trying to steal your information from this site.”
“The site’s security certificate is not trusted.”
These warnings can be alarming — and they’re meant to be. Browsers like Chrome, Firefox, and Safari block access and show these error messages to protect users from insecure or unsafe sites. But not all security errors are created equal. Sometimes the issue is with the website. Other times the problem may be on your end.
Here’s how to decode what’s happening — and decide whether it’s safe to proceed, or better to walk away.
When You Should Not Proceed
These are signs that something is seriously wrong:
-
The certificate is expired or revoked
-
The certificate was issued for a different website
-
The certificate is self-signed, or issued by an unknown certificate authority
-
The site is trying to load login forms, payment data, or personal info over HTTPS but fails
In these cases, proceeding could expose your data to hackers, especially if you’re on a public or insecure network (like airport Wi-Fi). This is how phishing and man-in-the-middle attacks can happen undetected.
If you see messages like:
-
NET::ERR_CERT_AUTHORITY_INVALID
-
SSL_ERROR_BAD_CERT_DOMAIN
-
This site may be trying to trick you
…it’s safer to leave the site immediately.
Quick Checks You Can Run Before Deciding What to Do
Sometimes, the problem can be temporary or due to a simple misconfiguration. Here’s what you can try:
1. Check the Website URL
Make sure you’ve typed the correct address. Attackers often use similar-looking URLs in phishing scams.
Example:
✅ paypal.com
❌ paypa1.com (with the number “1”)
2. Try Refreshing the Page
Sometimes a certificate loads incorrectly due to a connection glitch.
3. Check the Time and Date on Your Device
This is a very common cause of “certificate expired” or “not valid yet” errors — especially after a system restart, battery issue, or timezone change.
4. Try Visiting from Another Browser or Device
It could be a single browser showing cached certificate errors or suffering from a bad extension.
5. Try Loading the Website Over a Different Network
Corporate networks, hotels, and even some antivirus software intercept HTTPS traffic and may replace or block certificates — which triggers warnings.
Try switching to mobile data or a different Wi-Fi network.
How to Tell If It’s Safe to Proceed
It’s sometimes safe to click “Proceed anyway” if ALL of the following are true:
-
You personally know and trust the website (like your home router or dev server)
-
You’re not entering personal/payment data
-
The certificate error message says the site is using a self-signed certificate, and you know what that means
-
The site owner or business confirms there’s a temporary SSL issue (e.g., just expired and about to be renewed)
⚠️ But if the website involves login credentials, billing info, banking, healthcare, or sensitive data — even a small warning is a sign to back away.
What to Do If You’re Affected as a Visitor
If you believe the site is legitimate and someone made a technical mistake, here’s how to help:
-
Contact the site owner. Many small businesses aren’t aware their SSL has expired.
-
Use contact forms, LinkedIn, or email if available.
-
If it’s an e-commerce site with your order pending, reach out via social media and let them know the issue.
Most business owners will fix these errors quickly once aware — but until then, don’t enter any data on the page.
Up next: we’re going to transition into the full Webmaster/Developer Fix Guide, where you’ll get detailed instructions on how to identify, fix, and prevent HTTPS and SSL errors — across real-world configurations like WordPress, Apache, Nginx, Cloudflare, and more.
How Webmasters and Developers Can Fix Security Error Codes on HTTPS Websites
If you’re responsible for maintaining a website and users are encountering HTTPS or SSL-related errors, the impact goes far beyond broken trust. These errors can cause drop-offs in conversions, negative SEO signals, and lost revenue — even if they’re caused by a minor configuration mistake. The good news? Almost every HTTPS-related error has a clear cause, and with a methodical troubleshooting approach, you can resolve them efficiently.
This section offers a complete, hands-on framework to troubleshoot, diagnose, and fix HTTPS security errors. Whether you’re running Apache, Nginx, IIS, Cloudflare, or WordPress — this guide gives you the tools and exact steps to eliminate errors and restore a secure browsing experience.
Why Are HTTPS Security Errors Appearing?
When your site fails HTTPS validation, browsers interpret it as a potential security threat. This is often due to a failure in one or more of these areas:
-
Incorrect or expired SSL certificate
-
Mismatched domain names (hostname vs certificate)
-
Missing or unordered intermediate certificates
-
Unsupported SSL/TLS protocols or ciphers
-
Faulty server configurations (Apache, Nginx, IIS, etc.)
-
Mixed content (HTTPS page loading HTTP resources)
-
CDN or reverse proxy misconfiguration
-
SSL handshake failure or redirect loops
To solve the problem, you need to determine which part of the SSL/TLS chain is breaking and fix it accordingly.
A Step-by-Step Diagnostic Framework
Before you start adjusting your server configs or reinstalling certificates, follow this process to identify what’s going wrong.
Step 1: Reproduce the Error Yourself
-
Load the affected URL in Chrome and Firefox (each browser gives different error messages)
-
Use incognito/private mode to eliminate caching, extensions, etc.
-
Check the browser’s full technical error message (e.g., click “Advanced” in Chrome)
Step 2: Run an External SSL Test
Tools like SSL Labs’ SSL Server Test or Hardenize give you a full breakdown of:
-
Certificate details (issuer, CN, expiration)
-
Installed intermediates
-
Supported protocols and cipher suites
-
Chain of trust status
-
Whether protocols like TLS 1.0/1.1 are active (bad)
-
Whether TLS 1.2+/1.3 are supported (good)
If the test flags chain issues, unsupported protocols, weak ciphers, or expired certificates — you can confirm server-side fault.
Step 3: Use openssl or curl to Test from CLI
Example commands:
# Display full certificate chain
openssl s_client -connect yourdomain.com:443 -servername yourdomain.com -showcerts
# Test handshake and verify trust
echo | openssl s_client -connect yourdomain.com:443 -servername yourdomain.com -verify_return_error
# Fetch HTTP headers to check redirects
curl -I https://yourdomain.com
Command output will tell you:
-
Whether the correct certificate is being served
-
Whether the chain is complete
-
Whether the domain name matches
-
What protocols/ciphers are being negotiated
Step 4: Check Hosting/Reverse Proxy/CDN Layers
If you’re using Cloudflare, Sucuri, or a load balancer, make sure:
-
The origin server has a working certificate
-
The CDN is set to “Full (strict)” or equivalent, not “Flexible” SSL
-
No conflicting certificate exists between layers
Step 5: Fix the Issue Based on What You Found
This may involve:
-
Reinstalling or renewing the SSL certificate properly
-
Fixing the chain of trust
-
Adjusting your web server config
-
Enforcing HTTPS redirects correctly
-
Cleaning up mixed content in CMS or frontend markup
Each scenario is explained below.
Fixing Specific HTTPS Error Codes
Let’s go through each major browser error code and how to fix it — whether it’s on Apache, Nginx, IIS, WordPress, or a cloud provider.
Error: NET::ERR_CERT_AUTHORITY_INVALID
What it means:
The certificate is not signed by a known Certificate Authority (CA). This happens when:
-
You’re using a self-signed certificate on production
-
The certificate is signed by a private/internal CA
-
Intermediate certificates are not installed
How to fix it:
-
Ensure you’re using a certificate from a trusted public CA like Let’s Encrypt, DigiCert, or Sectigo.
-
Install the full certificate chain (including intermediate certificates). On Apache, you typically need:
SSLCertificateFile /etc/ssl/certs/yourcert.pem
SSLCertificateKeyFile /etc/ssl/private/yourkey.key
SSLCertificateChainFile /etc/ssl/certs/intermediate.pem
-
If using Nginx, combine the server certificate and intermediate certificate into a single bundle and reference it like:
ssl_certificate /etc/nginx/ssl/yourdomain_fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/yourkey.key;
-
Restart the server and re-test using SSL Labs.
Error: NET::ERR_CERT_DATE_INVALID
What it means:
This indicates the certificate is expired (or not yet valid). Users and tools will refuse the connection.
How to fix it:
-
Renew the certificate immediately using your hosting panel, Let’s Encrypt, or your CA
-
Replace the old certificate files with the renewed ones, and reload the server:
sudo systemctl reload nginx
# or
sudo systemctl reload apache2
-
Automate renewal so this doesn’t happen again. With Let’s Encrypt:
sudo certbot renew --dry-run
Error: ERR_SSL_PROTOCOL_ERROR / ssl_error_rx_record_too_long
What it means:
Handshake protocol failure. Browser and server can’t agree on TLS version or cipher.
How to fix it:
Apache:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite HIGH:!aNULL:!MD5
Nginx:
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5;
Restart the server and retest.
Also ensure port 443 is listening and mapped properly.
Error: NET::ERR_CERT_COMMON_NAME_INVALID
What it means:
The certificate doesn’t match the domain name being accessed — e.g. you’re visiting https://example.com but the certificate is for www.example.com.
How to fix:
-
Re-issue a certificate that includes all domains (use SAN certificates)
-
Check DNS and redirects — ensure
wwwand non-wwwaren’t pointed to separate hosts -
On Apache and Nginx, use SNI and server blocks to serve the correct certificate for each domain
Fixing Mixed Content Errors (WordPress, PHP, HTML)
What it means:
Your page is served via HTTPS, but some resources (e.g. images, CSS, JS) are using http://.
How to fix it:
-
Update all resource URLs to
https://or protocol-relative (//) -
For WordPress, use a plugin like Better Search Replace to replace
http://yourdomain.comwithhttps://yourdomain.comin the database -
Enforce HTTPS using
.htaccessor server blocks, and consider enablingContent-Security-Policy: upgrade-insecure-requests
Fixing HTTPS and Security Errors by Platform and Server Environment
Now that we’ve covered the common error codes and their causes, it’s time to apply full-lifecycle fixes based on where your website is hosted and how it’s configured. SSL/TLS troubleshooting varies depending on your stack — so below, you’ll find actionable, platform-specific steps for Apache, Nginx, cPanel, Cloudflare, and WordPress.
Fixing SSL/TLS Errors on Apache Server
Apache powers a large number of websites, and most SSL issues here stem from outdated configurations or incomplete certificate installations.
Common Causes on Apache:
-
Incomplete certificate chain (no intermediate certs)
-
Serving the wrong certificate to the wrong VirtualHost
-
Outdated SSL/TLS protocols enabled
-
HTTP served on port 443 (misconfigured
VirtualHost)
How to Fix:
1. Install the Correct Certificate + Chain
Make sure your Apache config includes:
SSLCertificateFile /etc/ssl/certs/yourdomain.crt
SSLCertificateKeyFile /etc/ssl/private/yourdomain.key
SSLCertificateChainFile /etc/ssl/certs/intermediate-ca.crt
Note: On Apache 2.4+,
SSLCertificateChainFilecan also be appended to the main certificate for use inSSLCertificateFile.
2. Enable High-Security TLS Protocols
Disable insecure protocols like SSLv2, SSLv3, TLS 1.0, and TLS 1.1. Use:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite HIGH:!aNULL:!MD5
SSLHonorCipherOrder on
3. Ensure Only HTTPS is Served on Port 443
Inside your VirtualHost:
<VirtualHost *:443>
ServerName example.com
SSLEngine on
# SSL configs...
</VirtualHost>
Restart Apache:
sudo systemctl reload apache2
Fixing SSL/TLS Errors on Nginx Server
Nginx is commonly used for high-performance sites and reverse proxies.
Typical Causes in Nginx:
-
Fullchain not configured (missing intermediate certs)
-
Wrong SSL certificate served for the domain
-
No SNI config for multiple domains
-
Using weak or legacy ciphers
How to Fix:
1. Use a Full Chain Certificate
Nginx expects the .crt or .pem file to be the full chain:
ssl_certificate /etc/nginx/ssl/yourdomain_fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/yourdomain.key;
To build a fullchain (if your CA did not supply one):
cat yourdomain.crt intermediate.crt > yourdomain_fullchain.pem
2. Enforce Modern TLS Protocols
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
3. Reload Nginx and Re-Test
sudo nginx -t
sudo systemctl reload nginx
Test via SSL Labs or:
openssl s_client -connect yourdomain.com:443 -servername yourdomain.com
Fixing SSL Errors in cPanel / WHM
cPanel hosts often encounter SSL issues due to auto-install or expired certs.
How to Fix Expired or Misconfigured SSL:
-
Log into cPanel → SSL/TLS → Manage SSL Hosts
-
Upload or re-install the correct certificate (with private key and CA bundle)
-
Confirm “AutoSSL” is enabled via WHM → SSL/TLS → Manage AutoSSL
-
Debug AutoSSL logs if a renewal has failed
Tip: If you’ve recently moved servers, rekey and reissue your certificate based on the new CSR.
Fixing SSL Issues with Cloudflare
Cloudflare often gets blamed for HTTPS errors, but the root cause is usually an origin server issue or an incorrect Cloudflare SSL mode.
Common Causes:
-
Using “Flexible” SSL when the origin needs HTTPS
-
Self-signed or invalid certificate at the origin server
-
Wrong SSL mode (Off, Flexible, Full, or Full Strict)
How to Fix:
1. Set SSL Mode to Full (Strict) if the origin has a valid certificate
Go to Cloudflare Dashboard → SSL/TLS → Overview → select “Full (Strict)”.
2. If Your Origin Uses Self-Signed SSL
Use “Full” mode instead of “Full (Strict)” — but be aware this is not fully secure. Better: install a Cloudflare Origin Certificate on your server.
3. Purge Cloudflare Cache after certificate install or renewal
4. Disable Universal SSL Temporarily if resolving errors during migration:
Dashboard → SSL/TLS → Edge Certificates → Disable → wait → re-enable.
5. Check for Mixed Content Errors via Cloudflare Automatic HTTPS Rewrites
Fixing Mixed Content Errors on WordPress
WordPress migrations from HTTP to HTTPS frequently leave behind hardcoded http:// content in:
-
Database links
-
Theme files
-
Widgets, menus, page builders
How to Fix:
1. Update the Site URLs
In Settings → General, confirm:
Site Address and WordPress Address use https://
2. Search and Replace Database URLs
Use WP-CLI or a plugin like Better Search Replace:
wp search-replace 'http://yourdomain.com' 'https://yourdomain.com' --all-tables
3. Install a Mixed Content Fixer Plugin
E.g., Really Simple SSL — temporarily helpful during a transition
4. Check your theme and plugin code for hardcoded URLs
Fixing Handshake Errors and Deprecated Protocols
You may encounter errors like:
-
ERR_SSL_PROTOCOL_ERROR -
SSL_ERROR_RX_RECORD_TOO_LONG -
ssl_error_no_cypher_overlap -
ERR_SSL_OBSOLETE_VERSION
These typically mean there’s a mismatch between what your server supports vs what the browser requires.
How to Fix:
-
Disable old protocols (SSLv2, SSLv3, TLS 1.0, and 1.1)
-
Enable TLS 1.2 or higher
-
Ensure SNI is configured if hosting multiple SSL domains on a single IP
-
Check cipher suites: use Mozilla SSL Config Generator
Preventing Future HTTPS and SSL Security Errors: A Complete Checklist for Webmasters
Solving SSL/TLS security errors once is great — but preventing them from happening again is the key to maintaining trust, protecting your SEO, and ensuring uninterrupted access to your site. Once your certificate is renewed and the issues are fixed, you don’t want to be caught off-guard the next time an expiration date arrives or a protocol update hits.
Below is a comprehensive prevention and maintenance strategy designed specifically for production websites, hosting environments, and teams that rely on savings in time, trust, and uptime.
1. Automate SSL Certificate Renewals
If you are using Let’s Encrypt or another ACME-supported certificate provider, enable automatic renewal and validate it works:
sudo certbot renew --dry-run
In cPanel or Plesk environments, turn on AutoSSL or Let’s Encrypt SSL via plugin or tools interface.
If using a paid SSL certificate, set calendar reminders or use DNS-level ACME integrations to avoid manual renewals.
2. Monitor SSL Certificate Status
Don’t wait for your users to see “certificate expired” errors.
Use tools like:
-
UptimeRobot (SSL expiration alerts)
-
cron-based OpenSSL checks
-
Qualys SSL Labs API
-
StatusCake, FreshPing, or Site24x7
Monitoring should alert you when:
-
SSL is expiring within 30 days
-
SSL chain is broken
-
TLS protocol fails validation
-
Server is returning invalid certificate after rebuild/migration
3. Enforce Strict HTTPS Usage
In your web application configuration (regardless of platform), make sure:
-
HTTP is redirected to HTTPS
-
Use permanent redirects (301) from HTTP to HTTPS
-
Enable HTTP Strict Transport Security (HSTS)
Example header configuration:
Strict-Transport-Security: max-age=31536000; includeSubDomains; preload
Submit to the HSTS preload list if ready — this ensures browsers only ever try HTTPS for your domain.
4. Disable Legacy TLS and Ciphers
Leaving insecure protocols like TLS 1.0, TLS 1.1, or SSLv3 enabled can trigger errors like:
-
ERR_SSL_OBSOLETE_VERSION -
ssl_error_no_cypher_overlap -
“obsolete TLS configuration” in Chrome dev tools
Example secure TLS configuration (Nginx):
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384';
ssl_prefer_server_ciphers on;
Use the Mozilla SSL Configuration Generator to generate secure configs for:
-
Apache
-
Nginx
-
HAProxy
-
Lighttpd
-
Node.js
5. Always Install the Full Certificate Chain
Many SSL errors stem from missing intermediate certificates. Browsers like Chrome and Firefox require the full chain to trust the cert.
Verify after installation using:
openssl s_client -connect yourdomain.com:443 -servername yourdomain.com -showcerts
Or use SSL Labs to confirm “Chain issues: None”.
6. Fix Mixed Content at Scale
Even after migrating to HTTPS, insecure content can still exist in:
-
Database records
-
WordPress theme files
-
Hardcoded scripts in HTML
-
External embeds or ads
Post-migration checklist:
-
Crawl site with a tool like Why No Padlock or Screaming Frog
-
Use search-replace on database (for WordPress or similar)
-
Add CSP header:
Content-Security-Policy: upgrade-insecure-requests
7. Use a CDN or Load Balancer Correctly
If you’re using Cloudflare, AWS CloudFront, or Cloud Load Balancers:
-
Use Full (Strict) SSL when possible
-
Install origin certificates
-
Make sure proxy/CDN SSL mode matches backend configuration
-
Test directly against the origin without CDN with:
curl -Ik https://youroriginserver.com
8. Document Your SSL Setup
SSL issues often arise when new team members deploy updates or migrate hosts without understanding that SSL configs are in place. Document:
-
Certificate path locations
-
Renewal processes
-
Web server configs
-
Environment differences (production vs staging)
-
Steps for applying HSTS and redirects
Even better: create an internal playbook/checklist to follow after migrations or upgrades.
9. Stay Up-to-Date with TLS and Browser Security Changes
Browsers regularly deprecate older protocols and security configurations. Track industry changes via:
-
Mozilla Security Blog
-
Chrome Security Updates
-
SSL Labs news
-
Let’s Encrypt blog
Being proactive means one less SSL surprise.
10. Test Regularly After Deploys
After any deployment involving changes to server blocks, SSL settings, reverse proxies, or hosting environment:
-
Re-test via browser, curl, and SSL Labs
-
Check
openssl s_clientfrom local and remote machines -
Validate correct redirects, headers, and SAN coverage
At this point, your site should not only be free from current SSL errors — you’ve also built protection against future failures. The next time a browser updates its security features or your certificate auto-renews, your setup will remain bulletproof.
Frequently Asked Questions (FAQs)
Q1: Why is my website showing “Your connection is not private” even though I installed an SSL certificate?
This usually happens due to one of the following: an expired certificate, missing intermediate certificates, incorrect certificate installation, or a hostname mismatch. Use an SSL checker (like SSL Labs) to confirm whether your certificate chain and domain configurations are valid. Also ensure that the certificate covers all necessary domains, including both www and non-www.
Q2: How do I fix mixed content warnings on an HTTPS website?
Mixed content occurs when an HTTPS page is trying to load resources (like images, JavaScript, or CSS) over HTTP. To fix it:
-
Replace all
http://links in HTML, CSS, or JS withhttps:// -
Use search-and-replace in databases (especially in WordPress)
-
Enforce HTTPS redirects, and add
Content-Security-Policy: upgrade-insecure-requestsheader if supported
Q3: What does “NET::ERR_CERT_AUTHORITY_INVALID” mean in Chrome?
It means the SSL certificate is not signed by a trusted Certificate Authority. This can be due to:
-
Self-signed certificate
-
Incorrect certificate bundle (missing intermediates)
-
Using a certificate from a private/internal CA
Install the full certificate chain and use a trusted public CA for production websites.
Q4: Why am I getting “ERR_SSL_PROTOCOL_ERROR” on my website?
This usually indicates a handshake or protocol mismatch between client and server. Common causes include:
-
Outdated or insecure TLS versions enabled on the server (like TLS 1.0/1.1)
-
No SNI configured when using multiple SSL domains on the same server
-
Incorrect HTTPS listener setup
Update your SSL/TLS config to support modern versions like TLS 1.2 or 1.3.
Q5: Do I need HTTPS if my website doesn’t collect user data?
Yes. Modern browsers mark all non-HTTPS pages as “Not Secure,” and search engines may lower your ranking. HTTPS ensures data integrity, privacy, and builds trust with both visitors and AI-powered search engines.