Last updated: Oct 26, 2025
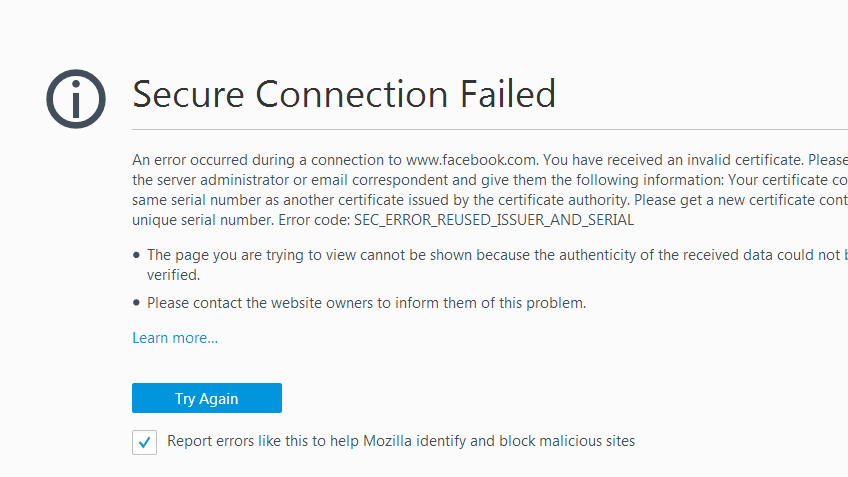
The SEC_ERROR_REUSED_ISSUER_AND_SERIAL error in Mozilla Firefox appears when the browser detects that a TLS certificate is reusing the same issuer and serial number as another certificate already stored or trusted. In the X.509 standard, this combination must be globally unique. If two different certificates share the same issuer + serial pair, Firefox blocks the connection to prevent potential impersonation or forged certificates.
While the message appears inside Firefox, this is not usually a browser bug — it is most often the result of a misconfigured certificate on the server side. This happens frequently with self-signed certificates, internal PKI (Active Directory Certificate Services), OpenSSL-generated certs that reused the serial file, reverse proxies (Nginx/Traefik) reissuing the same cert incorrectly, or DevOps environments (Docker/Kubernetes) that clone certificates across nodes.
However, in some cases, the certificate was fixed server-side, but Firefox still shows the error because it has cached the old certificate with the same issuer/serial inside its local store. That’s why resolving this issue usually requires a hybrid approach: clearing or removing the stale certificate locally and ensuring the server or CA reissues a new certificate with a unique serial number.
In this guide, we’ll explain:
-
Why this error occurs in Firefox
-
When it is a browser-side vs server-side issue
-
How to fix it as a user
-
How to fix it properly as a system admin or developer
-
How to prevent the error when issuing certificates in the future
This is exactly where competing guides fall short — they either tell users to clear the cert store (half solution), or they explain PKI theory without showing practical fixes. This guide covers both, so you can resolve the error permanently instead of masking it.
Why Does the SEC_ERROR_REUSED_ISSUER_AND_SERIAL Error Occur?
This error occurs when Firefox detects that two different certificates share the same issuer and serial number, which is a direct violation of the X.509 certificate standard. In PKI, the combination of (Issuer + Serial Number) must be globally unique. If a certificate authority — or a misconfigured server — generates another certificate with the same serial, Firefox assumes the connection may be unsafe or impersonated and blocks it to protect the user.
The root cause is usually not the browser, but the way the certificate was created or reused. This happens most often with self-signed or internally generated certificates, where the same serial number is accidentally reused across multiple instances or servers. However, if Firefox still has the old certificate cached in its certificate database, it may continue showing the error even after the server operator replaces the certificate with a corrected one.
Common Technical Causes (Server / CA Side)
-
The certificate was reissued but reused the same serial number
-
Self-signed certificates generated without incrementing serials
-
OpenSSL using the same
serialfile for multiple cert issuances -
Internal corporate CA (ADCS or OpenSSL) using duplicate serials
-
Reverse proxies serving a stale or cloned certificate (Nginx/HAProxy)
-
Docker / Kubernetes nodes copying the same certificate instance
Browser-Side Causes (User Perspective)
-
Firefox previously cached the old certificate in its local store
-
Importing a manually trusted certificate with the same issuer/serial
-
Multiple internal hosts using the same cert but different endpoints
-
Security appliances performing TLS inspection with reused cert metadata
In short, Firefox is rejecting the certificate not because the encryption is broken, but because the identity uniqueness requirement is violated — meaning it cannot trust that the certificate presented truly represents the server.
How to Fix SEC_ERROR_REUSED_ISSUER_AND_SERIAL (User-Side Fixes)
In some cases, the certificate on the server has already been fixed or replaced, but Firefox still shows the error because it has cached the old version of the certificate in its local trust store. Clearing that stale entry forces Firefox to fetch the new certificate and resolve the conflict. These steps are safe for end users and should be tried before assuming the server is still misconfigured.
1. Remove the Cached Certificate from Firefox
When Firefox stores a previous version of a certificate with the same issuer and serial number, it continues to treat it as a duplicate. Removing it resets the trust relationship.
Steps:
-
Open Firefox
-
Go to Settings → Privacy & Security
-
Scroll to Certificates → View Certificates
-
Find the affected domain under Servers
-
Delete the stored certificate
-
Restart Firefox and reconnect
2. Clear Firefox’s SSL State and Certificate Database
If the browser has cached more than one conflicting certificate entry, clearing the SSL state and certificate DB eliminates all stale records so that Firefox can revalidate the certificate fresh.
Steps:
-
Exit Firefox completely
-
Navigate to your Firefox profile directory
-
Delete the files:
-
cert9.db(certificate database) -
key4.db(if corruption is suspected)
-
-
Reopen Firefox and retry the site
Note: Firefox will recreate
cert9.dbautomatically.
3. Test in a New Firefox Profile
If the profile itself holds conflicting cert history, creating a new temporary profile can help confirm whether the issue is local or server-side.
Steps:
-
Open
about:profilesin Firefox -
Create a new temporary profile
-
Launch it and visit the same site
-
If the error disappears → old profile stored a duplicate cert
Once these user-side steps are completed, if the error persists, it means the server is still presenting a duplicate or reused serial — and the real fix must happen on the certificate issuance side.
Server-Side Fixes (Permanent Resolution for Administrators)
If the error persists even after clearing Firefox’s local certificate cache, then the TLS certificate being served by the server is still reusing the same issuer + serial number from an earlier certificate. This typically occurs when administrators reissue or regenerate certificates without ensuring a new serial number is assigned. Since Firefox strictly enforces uniqueness on these values, the problem must be fixed at the certificate generation or CA configuration level.
The correct solution is to reissue a new certificate with a unique serial number, ensuring the issuer/serial pair is not duplicated. How this is fixed depends on whether you are using Let’s Encrypt, a corporate/internal CA, or self-signed/OpenSSL certificates.
1. Fix for Self-Signed / OpenSSL Certificates
If you use OpenSSL and reused the same serial file during reissuance, OpenSSL will assign the same serial number again.
Steps to fix:
-
Delete or rotate the existing
serialfile before regenerating -
Or specify a new unique serial manually using
-set_serial -
Then reissue the certificate with a new serial
2. Fix for Internal Corporate CA (ADCS / On-prem PKI)
Windows ADCS or similar internal PKI systems can unintentionally reuse issuer/serial if the same template is misconfigured or an old cert is cloned.
Steps to fix:
-
Revoke the old certificate
-
Force renewal via the CA with fresh serial
-
Confirm revocation has propagated before reissuing
3. Fix for Reverse Proxies (Nginx / Apache / HAProxy / Traefik)
Reverse proxies often continue serving a stale certificate even after a new one is installed.
Steps to fix:
-
Ensure the correct certificate file is referenced in config
-
Restart or reload the proxy (e.g.,
nginx -s reload) -
Check if intermediate files are duplicated across backends
4. Fix for Kubernetes / Docker / Load Balanced Clusters
In containerized environments, the same certificate bundle may be mounted and reused across pods/nodes, causing Firefox to see duplicates from multiple hosts.
Steps to fix:
-
Regenerate certificate with unique serial per environment
-
Or ensure new deployments pick up the reissued cert
-
Restart pods/nodes after replacement to clear stale certs
Once the server is serving a certificate with a unique serial number, Firefox will no longer reject it — assuming user-side cached entries have been cleared.
Advanced Fixes & Prevention (DevOps / PKI Best Practices)
The SEC_ERROR_REUSED_ISSUER_AND_SERIAL error is almost always a sign of improper certificate lifecycle handling. Fixing it once is easy — preventing it requires ensuring future certificates always receive unique serial numbers and that no stale copies remain in rotation. This is especially important in automated environments where CI/CD pipelines, Kubernetes secrets, or internal CAs may silently reuse certificate metadata.
Preventing this error permanently involves two layers:
-
Ensuring certificates are issued correctly (unique serials), and
-
Ensuring clients do not retain outdated conflicting copies.
1. Enforce Unique Serial Numbers in Internal CA Pipelines
Internal PKI deployments (OpenSSL, ADCS, HashiCorp Vault, EasyRSA, etc.) can accidentally reuse serials if not configured properly.
Best practices:
-
Never reuse the same
serialfile when regenerating certs -
For OpenSSL automation, rotate
serialon each issuance -
Use timestamp-based or UUID-based serial generation when possible
-
Ensure your CA increments serials monotonically
2. Don’t “Clone” Certificates Across Multiple Hosts
This error is common in Docker and Kubernetes clusters where the same cert is copied across multiple nodes, all pretending to be “different” endpoints with the same identity.
Best practices:
-
If the endpoint hostname differs → generate a new cert
-
Avoid reusing
.crt / .pemfiles across separate services -
Use SAN certificates properly instead of duplicating certs per host
3. Always Reload or Restart Services After Reissuing
Even when a fresh certificate is issued, proxies or load balancers may continue serving a stale one from memory.
Best practices:
-
Reload Nginx/Apache/HAProxy after cert replacement
-
For Kubernetes, restart/redeploy pods mounting the cert
-
Clear old
.crtbundles from backup directories
4. Automate Renewal with a CA That Handles Serial Correctly
Let’s Encrypt and other public CAs never reuse serial numbers, which is why this issue rarely occurs with public TLS. The problem is most common with self-signed or internal CA certificates.
Best practices:
-
Prefer ACME-based issuance when possible
-
If using internal CA, configure unique serial policy
-
Use short-lived certificates to reduce revocation risks
5. For Firefox Users in Managed Environments: Use Policy-Level Trust
If this error recurs in corporate networks where TLS inspection appliances reuse cert metadata:
Best practices:
-
Install enterprise root CA via Firefox policies
-
Ensure the MITM appliance reissues proper unique serials
-
Avoid sharing a single cert identity across multiple proxies
Quick Prevention Summary
| Root Cause | Prevention Strategy |
|---|---|
| Serial reused | Force unique serial per issuance |
| Proxy caching | Restart/reload services |
| Kubernetes reuse | Do not clone certs across pods |
| Internal CA bug | Configure incremental / UUID serials |
| Browser cache | Clear cert9.db on update |
| TLS inspection | Use enterprise PKI with proper serial handling |
Troubleshooting Checklist (Step-by-Step Diagnosis)
Before applying fixes randomly, use this checklist to determine whether the issue is browser-side or server-side. This ensures the correct solution is applied the first time.
Step 1 – Test the Site in Another Browser
If the site works in Chrome/Edge but fails in Firefox, the problem is likely cached certificate data in Firefox, not the live certificate.
Step 2 – Try a Private Window or Fresh Profile
If the site loads in Firefox Private mode or in a new profile, the old certificate is stored in your main profile.
→ User-side fix required
Step 3 – Inspect the Certificate Serial Number
If multiple servers, proxies, or nodes present the same serial number while claiming to be different certs, Firefox correctly rejects them.
→ Server-side fix required
Step 4 – Check for Reverse Proxy Caching
If you use Nginx, Apache, HAProxy, Traefik, Envoy, or Cloudflare, verify the backend cert was actually replaced, not just stored in memory.
→ Reload / restart required
Step 5 – If Using a Corporate/Internal CA
Verify whether your CA generates unique serial numbers, not static or reused ones.
→ CA configuration fix
Step 6 – If Using Docker/Kubernetes
Check whether the certificate is being mounted (copied) across nodes instead of being issued individually per endpoint.
→ Deployment fix
Quick Rules of Thumb
| Behavior | Root Cause |
|---|---|
| Works in other browsers but not Firefox | Cached cert conflict (client-side) |
| Fails across all browsers | Real server-side duplicate serial |
| Works after cert9.db reset | Local trust store issue |
| Fails again after restart | Proxy serving stale cert |
| Works on one node, fails on another | Cluster/copy reuse issue |
With this diagnostic checklist complete, the final step of the blog is to wrap with a conclusion and final takeaway so users understand not just how to fix it, but why it matters for TLS trust.
Conclusion
The SEC_ERROR_REUSED_ISSUER_AND_SERIAL error in Firefox isn’t a random browser glitch — it is Firefox correctly enforcing the X.509 requirement that every certificate must have a globally unique issuer + serial number. When that uniqueness is violated, Firefox assumes the certificate may be forged, duplicated, or reused improperly across systems, and blocks it to prevent identity spoofing.
In many cases, the browser simply has a cached older version of the certificate stored locally, which is why clearing Firefox’s certificate database resolves the issue for end users. But when the certificate itself was generated incorrectly — especially with self-signed certs, internal PKI, proxies, Docker/Kubernetes clusters, or cloned certificates — the real fix must happen at the server or CA level, by reissuing the certificate with a new unique serial number.
By combining client-side cleanup with proper certificate issuance practices, you can eliminate this error permanently and prevent it from reappearing in future deployments. Modern TLS infrastructure expects uniqueness and proper rotation — and Firefox enforces that rule more strictly than other browsers, which is why this error appears more frequently here than in Chrome or Edge.
The browser is warning you because the certificate identity is not unique — fix the serial at the CA level, and clear the cached cert in Firefox to restore trust.
Frequently Asked Questions (FAQ)
1. What causes the SEC_ERROR_REUSED_ISSUER_AND_SERIAL error in Firefox?
This error occurs when Firefox detects two different certificates using the same issuer and serial number, which violates X.509 uniqueness rules. It is most commonly caused by self-signed or internally generated certificates being reused without changing the serial number.
2. Is this a browser issue or a server issue?
It can be either, but most of the time it is a server-side issue caused by reissuing or cloning certificates with duplicate serial numbers. In some cases, Firefox still stores an old certificate locally and must have its certificate cache cleared.
3. Why does Firefox enforce this error more strictly than Chrome?
Firefox performs stricter identity checks on certificate serial uniqueness. Chrome sometimes accepts reused serial numbers temporarily, while Firefox blocks them immediately to prevent potential impersonation or MITM risks.
4. How do I fix this error as a user (without server access)?
You can remove the cached certificate from Firefox by deleting it from Settings > Privacy & Security > View Certificates, or by clearing cert9.db in your Firefox profile folder.
5. How do I fix this error as a sysadmin?
You must reissue or regenerate the certificate with a new unique serial number. For OpenSSL or internal CA setups, ensure the serial file is rotated or incremented before issuing a replacement certificate.
6. Does this error happen with Let’s Encrypt certificates?
Rarely. Public CAs like Let’s Encrypt automatically generate unique serials. This issue mostly happens with self-signed certs, custom internal CAs, reverse proxies, or manually generated certificates.
7. Can Docker, Kubernetes, or load balancers cause this error?
Yes. If the same certificate file is cloned across multiple nodes, Firefox sees repeated issuer/serial reuse and flags it. Each endpoint should either use a SAN certificate or a properly reissued unique certificate.
8. What if the site works in Chrome but fails in Firefox?
That means Firefox is strictly enforcing the issuer+serial uniqueness check and Chrome is not. The server still needs a proper certificate reissue, or Firefox’s cached cert must be cleared.
9. Can revocation fix this issue?
No. Revoking the certificate does not change the reused serial number. The certificate must be reissued with a new serial — revocation alone is not enough.
10. How can I prevent this in the future?
Do not reuse or clone certificate files, especially in automation pipelines. Always issue a fresh certificate with a unique serial, and restart proxies or services after replacement.