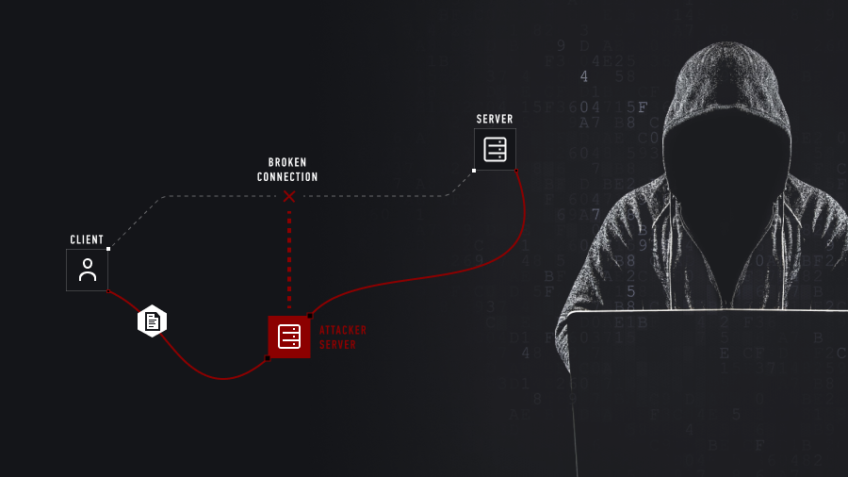
Being an internet user, you might have come across tones of error that would cause due to browsing data, an extension that you have added to the browser, download history, cookies from other sites that can be malicious or suspicious too and other several reasons that can cause the error to occur. Nowadays, you will experience a different type of error that is MITM – Man in The Middle Attack in which a third party gets into a said transfer in a non-going connection.
There have been recorded several incidents about this man in the middle attack error. we will see one that happened in Belgium where the attackers stole €6 million by hacking into a largely sized European organization. The attackers were easily able to gain access to the organizations’ corporate email account and convinced their client to send money. For more, you can click on the link here Europol’s press release. They described the attack was done with the help of social engineering methods and malware. According to the research, the attack was one of the prime examples of the man in the middle attack.
They kept their communication with their client smooth and ongoing for detecting the payments and taking overpayments requests made in the organization.
It’s time for you to understand the man in the middle attack’s working and after that, we will see the types of mitm attacks and at the end man in the middle attack prevention. Now let’s go for a ride!
Working of MITM attack
It is a type of online attack where the hacker gets access between the users and the website the user is visiting. the attack of MITM comes in different ways, for instance, a fake bank website may be used for getting the credential of the users. The fake website saves the credential of the user. The fake website is the man in the middle that is an actual website of banking for the user.
There can be several reasons for making this attack happen or techniques for implementing the attack properly. The common ones are as follows –
- For stealing sensitive information such as credit card details, login details, etc.
- Snooping into private communications or transfers may include the trading sector or other valuable information
Types of MITM attacks
There have been found many types of MITM attacks and they are very reliable and have never gone wrong. But still, some loopholes make the attack vulnerable but research states that performing a MITM attack is not at all difficult. There are cheap online tools available for performing the said attack along with covering all the loopholes that could make the attack go wrong. Some of the types of MITM attack that we are going to talk about is email hijacking, wi-fi eavesdropping, session hijacking, ARP spoofing and man in the browser. Let’s see what is their capacity.
-
Email hijacking
You can get to know by the name email hijacking, where the hacker targets the email account of the company, financial organization, and banking sectors sometimes the general people. After they get access, they monitor the transaction taking place to make the attack convincing
-
Wi-Fi eavesdropping
The attacker majorly implies the attack with the help of a Wi-Fi connection. The attacker makes a Wi-Fi connection and waits for the users to connect their device with it which is called an “Evil twin”. After the user connects to the Wi-Fi the attacker will have access to further stealing the user personal information of the users who are connected to the fake-looking legit Wi-Fi connection. This attack is commonly faced by the café shops.
-
Session hijacking
While logging into the website, a connection gets created between the website and the computer. The hackers can take advantage by hijacking your session as there has been a connection created between the computer and the website. The cookies can also be stolen that contain information such as your credentials, all online activity, pre-fill forms, and sometimes your current location also. After getting the information to your login cookies then it won’t be hard enough for the attacker to login into your account.
-
ARP (Address Resolution Protocol) spoofing
The ARP is used by the LAN, so the attack takes place mainly on LAN. At the time when the user sends an ARP request, the attacker sends a fake reply to the users. The attacker states themselves being the device, for instance, a router that helps the attacker to intrude all the internet traffic of the user.
-
Man in the browser
This attack breaks the vulnerability of the installed browser. Some other attack vectors come under it and are like Trojan horses, Java exploits, SQL injection attacks, Computer worms, Browser addons. The major motive for the error is getting financial information with the help of the attack.
Steps of prevention of MITM attack
-
Have a strong WEP or WAP encrypted access points
Protecting your wireless access point with robust encrypted technologies is a must. It will back you to deflect unwanted users who perform an attack and try to gain access to your network whereas, weak encryption can be attacked easily by the attackers and pave their way into your system or can begin man in the middle attack.
-
Strong login credentials for your routers
When you purchase a router, you get a default login password and this helps the attacker as the login password is easily available online. It’s recommended to change the said login password of your router and Wi-Fi connection and prevent them from being attacked. By not changing the login password the attacker sticks to your connection and they can change the DNS server with their malicious one and it can get worse too. They can infect other routers too, with malicious software.
-
Use a virtual private network
With the help of VPNs provided by the well-known for keeping you secured from the environment from sensitive transfers outside your local area network. It has a key-based encryption technology that provides security as well as anonymity during your session. This will help the user while transferring someone will be sharing the same network, they will not get success in translating the traffic that the router is using a VPN.
-
Forced HTTPS
HTTPS always offers encryption, but the attackers have now found a solution for changing HTTPS to HTTP. So, by giving a serious suggestion for implementing HTTP strict transport security or HSTS for deflecting such situations. The one with HTTPS is only eligible to connect others who has HTTP are blocked and any content which makes use of HTTP protocol. It also prevents cookies from being extracted.
There are a lot of mitm attacks taking place around the globe because of the technology evolves the attack also evolves and can be more fatal in the coming years. You can take a protective measure that doesn’t make a victim of such attacks. MITM attack can be prevented, all you need is a good security measure and in the above article we have suggested some of the best ones. Have a look.