The “SSL Certificate with Wrong Hostname” error appears when the domain name in the SSL/TLS certificate does not match the website address the user is visiting. In simple terms, the browser expects the certificate to be issued for a specific domain — but the certificate is registered for a different domain or subdomain. When this mismatch happens, the browser cannot verify the site’s identity, and it treats the connection as insecure.
This error is a protection mechanism built into modern browsers to prevent impersonation, phishing, and man-in-the-middle attacks. Because SSL/TLS certificates are responsible for verifying both encryption and identity, a hostname mismatch means the browser cannot be sure it is talking to the right website.
The good news? This issue is usually easy to fix once you understand why it happens. In this guide, we’ll break down the reasons behind the hostname mismatch and walk you through practical solutions for both site owners and end users.
What is an SSL Certificate with Wrong Hostname Error?
An SSL/TLS certificate is issued for a specific hostname (domain or subdomain). If the domain the user is visiting does not exactly match the domain listed inside the certificate — in either the Common Name (CN) field or the Subject Alternative Name (SAN) field — the browser will reject the connection and display a hostname mismatch error.
In simpler terms:
The browser expects the certificate to belong to the exact domain you’re visiting — and if it belongs to a different domain, the browser assumes the site may be impersonating another server.
This is a critical identity check in TLS. Encryption alone is not enough — the browser must confirm it is talking to the right destination.
How the Browser Displays the Error
Different browsers show slightly different warnings, but the meaning is the same: the certificate does not match the hostname.
| Browser | Typical Message |
|---|---|
| Chrome | “Your connection is not private” → NET::ERR_CERT_COMMON_NAME_INVALID |
| Firefox | “Warning: Potential Security Risk Ahead” |
| Edge | “This site’s security certificate does not match the site’s address” |
| Safari | “This certificate is not valid for this website” |
These warnings appear before the web page loads, because modern browsers block SSL/TLS handshake completion when hostname verification fails.
Why the Hostname Must Match
When a certificate is issued, the CA (Certificate Authority) binds it to:
-
A Common Name (CN) → the primary domain (e.g.,
www.example.com) -
One or more SAN entries → additional valid hostnames (e.g.,
example.com,blog.example.com)
If a user visits any domain outside that list, the certificate is considered invalid for that hostname.
A Simple Example
| Certificate Issued For | User Visits | Result |
|---|---|---|
www.example.com |
example.com |
❌ Mismatch |
example.com |
www.example.com |
❌ Mismatch |
*.example.com (Wildcard) |
blog.example.com |
✅ OK |
*.example.com |
example.com (root) |
❌ Not covered |
example.com + SAN: www.example.com |
Either | ✅ Correct |
This is one of the most common mistakes when setting up SSL, especially when migrating domains, switching from HTTP to HTTPS, or using subdomains.
Why the Browser Treats This as a Security Risk
A hostname mismatch may indicate:
-
Configuration mistake (most common)
-
Expired old certificate still being used
-
Proxy or CDN serving the wrong certificate
-
Potential spoofing / impersonation attempt
To prevent man-in-the-middle attacks, browsers block access unless the user bypasses the warning manually (not recommended).
Why Does the SSL Certificate with Wrong Hostname Error Occur?
This error happens when the hostname (domain or subdomain) in the URL does not match the hostname that the SSL/TLS certificate was issued for. Because SSL certificates are tied to identity verification, the browser assumes there is a potential security risk when the hostname does not match exactly — and blocks the connection.
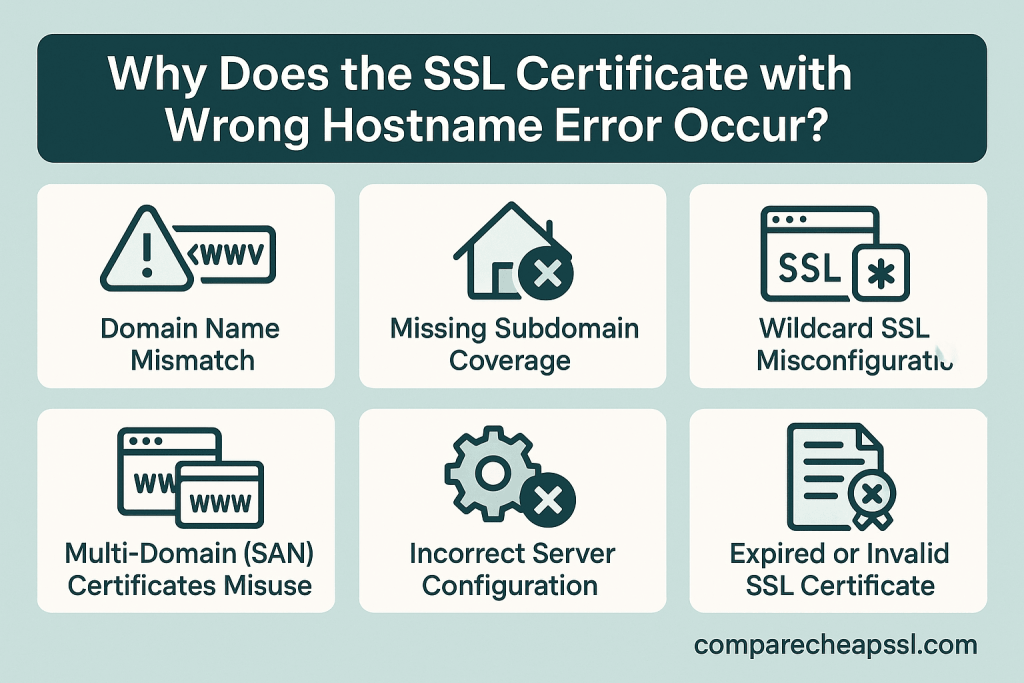
1. Domain Name Mismatch (Most Common Cause)
If the certificate was issued for one hostname (e.g., www.example.com) but the user visits a different hostname (e.g., example.com or shop.example.com), the browser detects a mismatch and throws the error.
2. Missing “www” or Root Domain Coverage
A very common scenario:
-
Certificate issued for
www.example.com -
User accesses
example.com(without www)
Unless both hostnames are included in the CN or SAN fields, the certificate is treated as invalid.
3. Wildcard Certificate Misconfiguration
Wildcard SSL certificates only cover:
*.example.com → blog.example.com, shop.example.com, etc.
They do not cover:
example.com (root domain)
sub.sub.example.com (deep subdomains)
If a site relies on *.example.com but users access the root domain or a deeper subdomain, the browser reports a hostname mismatch.
4. Multi-Domain / SAN Certificate Not Including the Accessed Hostname
SAN (Subject Alternative Name) certificates can secure multiple domains — but only the domains explicitly listed.
If the SAN list misses even one variant (e.g., app.example.com), any attempt to access it will trigger this error.
5. CDN or Reverse Proxy Serving the Wrong Certificate
In modern architectures (Cloudflare, AWS, Nginx, load balancers), the certificate delivered to the browser might not be the one installed on the origin server.
Common misconfigurations include:
-
CDN presenting a generic/shared certificate
-
Origin certificate not matching the public hostname
-
Proxy forwarding to a different hostname internally
6. Server Redirecting to a Different Hostname
If the server redirects traffic to another domain (for example, example.com → new.example.com) but the certificate was not reissued for the new hostname, the browser sees a mismatch.
7. Expired or Incorrectly Renewed SSL Certificate
If the certificate is renewed but:
-
The hostname field changes
-
The SAN list is incomplete
-
The old certificate is still cached on the server
…the browser may still detect a mismatch.
The error occurs when the SSL certificate’s CN/SAN does not match the domain being accessed — often due to missing hostname coverage, wildcard misuse, CDN/proxy misconfiguration, or redirecting to a hostname the certificate wasn’t issued for.
How to Solve SSL Certificate with Wrong Hostname Error
Now that we understand why the error occurs, let’s explore how to fix it. Follow these steps to resolve the SSL certificate with wrong hostname error.

Step 1: Check the SSL Certificate Details
The first step in fixing the error is to verify whether the hostname matches the domain listed in the SSL certificate.
In Google Chrome:
- Visit the website displaying the error.
- Click the padlock icon in the address bar.
- Click Certificate.
- Review the Common Name (CN) and Subject Alternative Name (SAN) fields to ensure they match the domain name you’re trying to visit.
In Mozilla Firefox:
- Visit the website and click the padlock icon in the address bar.
- Click More Information and select View Certificate.
- In the Details tab, verify the Common Name and SAN to confirm that they match the domain name.
If the certificate does not match the domain you are visiting, proceed to the next steps.
Step 2: Reissue or Replace the SSL Certificate
If the domain does not match, you need to reissue the SSL certificate to reflect the correct hostname.
- Contact your Certificate Authority (CA): If you already have an SSL certificate, contact your CA to request a reissue of the certificate with the correct hostname.
- Ensure the Right Domain is Included: When requesting the SSL certificate, ensure that the domain name in question is listed in the Common Name (CN) field or as a Subject Alternative Name (SAN). For multi-domain certificates, all domains you want to secure must be listed.
- Purchase the Correct SSL Certificate:
- For a Single Domain: Make sure you buy the SSL certificate for the exact domain name.
- For Multiple Domains/Subdomains: If you need coverage for multiple domains, purchase a multi-domain or wildcard SSL certificate.
Step 3: Ensure Domain is Correctly Configured in Server Settings
Once the SSL certificate is reissued or replaced, you need to ensure that the web server is configured to serve the certificate for the correct domain.
For Apache Servers:
- Locate the SSL configuration file (often found in /etc/httpd/conf.d/ssl.conf or /etc/apache2/sites-available/ssl.conf).
- Ensure that the
SSLCertificateFile,SSLCertificateKeyFile, andSSLCertificateChainFilepoint to the correct files. - Add a
ServerNamedirective that matches the domain name.
<VirtualHost *:443>
ServerName www.example.com
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /etc/ssl/certs/example.com.crt
SSLCertificateKeyFile /etc/ssl/private/example.com.key
SSLCertificateChainFile /etc/ssl/certs/example.com.ca-bundle
</VirtualHost>
- Restart Apache: Run
sudo service apache2 restartorsudo systemctl restart apache2to apply the changes.
For Nginx Servers:
- Open the Nginx configuration file (usually /etc/nginx/sites-available/default or /etc/nginx/nginx.conf).
- Ensure the SSL certificate directives (
ssl_certificate,ssl_certificate_key, andssl_trusted_certificate) point to the correct certificate files. - Add the
server_namedirective for the correct domain.
server {
listen 443 ssl;
server_name www.example.com;
ssl_certificate /etc/nginx/ssl/example.com.crt;
ssl_certificate_key /etc/nginx/ssl/example.com.key;
ssl_trusted_certificate /etc/nginx/ssl/example.com.ca-bundle;
}
- Restart Nginx: Run
sudo service nginx restartorsudo systemctl restart nginxto apply the changes.
Step 4: Implement Redirects (If Necessary)
If your SSL certificate is issued for www.example.com, but users are accessing example.com without “www,” you may need to set up a redirect from the non-www version to the www version.
Redirect HTTP to HTTPS in .htaccess (Apache Servers):
- Open the .htaccess file in your website’s root directory.
- Add the following lines to enforce the HTTPS version of your domain:
RewriteEngine On
RewriteCond %{HTTP_HOST} ^example\.com [NC]
RewriteRule ^(.*)$ https://www.example.com/$1 [L,R=301]
Redirect HTTP to HTTPS in Nginx Config:
- Edit the Nginx configuration file.
- Add the following server block to redirect non-www to www:
server {
listen 80;
server_name example.com;
return 301 http://www.example.com$request_uri;
}
Step 5: Clear Cache and Test
After making the necessary changes, clear your browser’s cache to ensure the new certificate is being used. You can also use tools like SSL Labs’ SSL Test to check the validity and configuration of your SSL certificate.
Prevention & Best Practices
Preventing the “SSL Certificate with Wrong Hostname” error is much easier than fixing it after it appears. By following SSL/TLS best practices during certificate issuance, renewal, and server configuration, you can ensure that your certificate always matches the correct domain and maintains browser trust.
1. Always Include Both www and Non-www Versions
Many hostname mismatch errors happen because the certificate only protects one version of the domain.
Example:
-
Issued for:
www.example.com -
But user visits:
example.com→ ❌ mismatch
When issuing a certificate, always include both hostnames:
-
example.com -
www.example.com
2. Use SAN or Wildcard Certificates for Multiple Domains
If your site uses multiple subdomains, choose:
-
Wildcard SSL (
*.example.com) for unlimited subdomains -
SAN (Subject Alternative Name) SSL for multiple unrelated domains or hostnames
Make sure every hostname a user may visit is listed in the SAN field.
3. Update the Certificate After Domain Changes or Migration
If you:
-
Switch hosting providers
-
Change from
httptohttps -
Move from
example.comtonewsite.com -
Add or remove subdomains
…you must reissue the SSL certificate. Simply copying the old one will result in a mismatch.
4. Configure CDN/Proxy Certificates Correctly
In modern cloud setups, the certificate at the edge (CDN or load balancer) must also match the hostname — not just the origin server.
Double-check:
-
Cloudflare / AWS / Akamai certificate settings
-
Reverse proxy (Nginx, Apache, HAProxy) hostname mapping
-
Origin vs edge certificate consistency
5. Monitor SSL Expiration and Hostname Coverage
Use automated monitoring tools or ACME clients (Let’s Encrypt / ZeroSSL) to ensure:
-
Certificates renew on time
-
Renewed certificates retain the same hostname coverage
-
No intermediate mismatch during issuance
6. Avoid Deep Subdomain Mistakes
Wildcard certificates (*.example.com) do not cover:
-
example.com(root) -
deep.sub.example.com(nested subdomain)
If you need coverage for nested subdomains, SAN is required.
Quick Checklist for Prevention
| Best Practice | Prevents |
|---|---|
| Include both www + non-www | Common Name mismatch |
| Use SAN/wildcard | Subdomain errors |
| Reissue after migration | Old hostname retained |
| Check CDN config | Wrong certificate served |
| Auto-renew + monitor | Expired/misaligned certs |
Conclusion
The “SSL Certificate with Wrong Hostname” error occurs when the SSL/TLS certificate installed on a server does not match the exact domain or subdomain that the user is trying to access. Because the certificate is tied to identity verification, a mismatch signals to the browser that the site may not be legitimate — which is why access is blocked or warned as unsafe.
- Verify the SSL certificate details and identify the mismatch.
- Reissue or replace the SSL certificate with the correct domain.
- Ensure your web server is configured to use the correct certificate.
- Set up redirects if necessary.
- Clear the cache and test the website for proper SSL configuration.
This error is not just a technical glitch — it is a security measure designed to prevent domain spoofing. Matching the certificate hostname with the served domain ensures both encryption and identity verification.
By following these steps, you can solve the SSL certificate with wrong hostname error and ensure a secure, seamless browsing experience for your users.
FAQs
What does an SSL certificate hostname mismatch error mean?
This error means the domain or subdomain you are accessing does not match the Common Name (CN) or Subject Alternative Name (SAN) listed on your site’s SSL certificate.
Why am I seeing a wrong hostname SSL certificate error on my site?
Common reasons include:
- The SSL certificate was issued for a different domain or subdomain
- The certificate was installed on the wrong website
- The hostname in your site or network configuration doesn’t match the certificate
- Accessing the site via IP address rather than domain name
How do I fix an SSL certificate hostname mismatch error?
- Check the SSL certificate details to ensure they match your domain
- Update your site/server configuration to match the certificate hostname
- Reinstall the SSL certificate if it’s for the wrong hostname
- Reissue or renew your SSL certificate with the correct domain/subdomain
Does an “SSL Certificate with Wrong Hostname” error affect SEO?
Yes, a mismatched SSL certificate can negatively impact your SEO, as search engines like Google prioritize secure websites. Visitors may also see security warnings, which can decrease your site’s credibility.
Can SSL certificate errors hurt my site’s user experience (UX)?
Definitely. Visitors who encounter SSL errors will receive a security warning, which can prevent them from browsing your website. This can lead to a high bounce rate and loss of trust in your site.
Can I avoid hostname errors in the future?
Double-check all hostnames needed for your site when ordering your SSL certificate, and keep your certificate and DNS configurations in sync. Regularly verify your SSL installation after making website or server changes.
Can I test if my SSL certificate and hostname are set up correctly?
Yes, you can use online SSL checker tools or manually view your certificate details in your browser to confirm the hostname matches the certificate.


