Last updated: Dec 6, 2025
Smart home technology has transformed modern living. From smart locks and voice assistants to connected refrigerators, thermostats, lighting systems, cameras, baby monitors, and home security hubs — households in 2026 rely heavily on automation, remote control, and continuous connectivity.
But with convenience comes vulnerability.
In 2026, smart home cybersecurity threats surged dramatically due to:
-
Growing device adoption
-
Increased integration with mobile apps
-
Persistent IoT vulnerabilities
-
Weak authentication practices
-
Lack of firmware updates
-
Rising interest from cybercriminals
-
AI-driven exploit automation
Smart homes now represent one of the fastest-growing attack surfaces globally. As households add more IoT devices, attackers gain more entry points — often easier to exploit than traditional computers or smartphones.
-
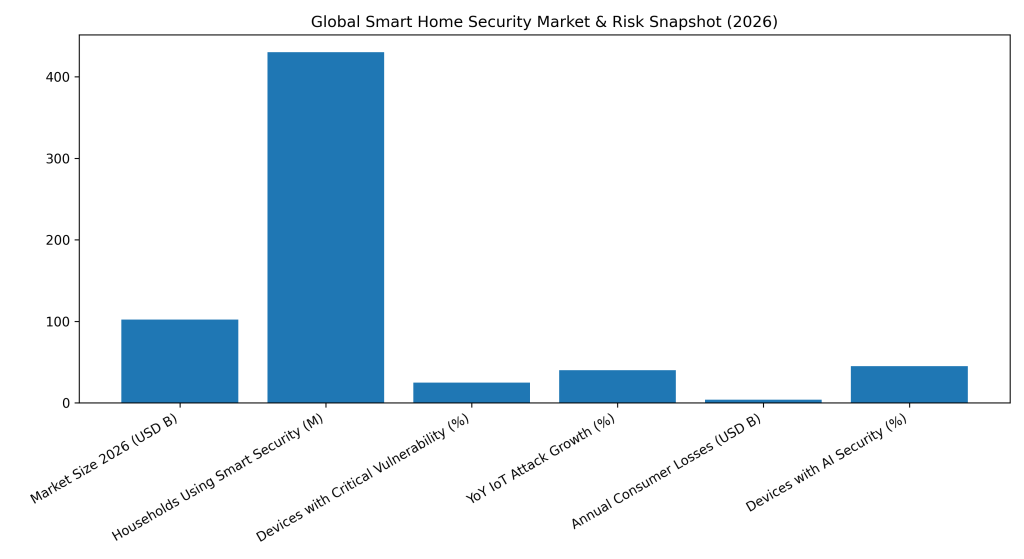
Global Smart Home Security Market Size: The global smart home security market is projected to surpass $95–$110 billion by 2026, driven by rapid adoption of smart cameras, video doorbells, smart locks, alarm systems, and AI-powered monitoring. The market is growing at an estimated CAGR of 18–20%, significantly faster than traditional home security solutions.
-
Household Adoption Rate: By 2026, over 430 million households worldwide are expected to use at least one smart home security device. In developed markets such as North America and Western Europe, 55–65% of homes now deploy smart cameras, smart locks, or connected alarm systems, while adoption in Asia-Pacific is growing at the fastest pace.
-
Smart Home Cybersecurity Risk: As adoption rises, so does exposure. An estimated 1 in 4 smart home devices contains at least one critical security vulnerability, including weak authentication, outdated firmware, or unencrypted communication. Compromised smart devices are increasingly exploited as entry points into home networks.
-
IoT Attack Growth: Attacks targeting smart home and IoT devices increased by 40%+ year over year, fueled by botnets, credential stuffing, and remote takeover of cameras and routers. Smart cameras and home routers remain the most targeted devices due to default passwords and poor patching practices.
-
Financial Impact on Consumers: Smart home security breaches cost consumers an estimated $3.1–$4.6 billion annually through device replacement, identity theft, privacy violations, and unauthorized surveillance. While individual losses are smaller than enterprise breaches, the cumulative global impact continues to rise sharply.
-
Top Smart Home Attack Vectors: The most common attack vectors in smart homes include weak or reused passwords (~32%), unpatched firmware vulnerabilities (~27%), insecure mobile apps (~18%), and compromised cloud accounts (~14%). These trends highlight how user behavior and vendor security practices directly affect home security risk.
-
Privacy & Surveillance Concerns: Over 60% of smart home users express concern about unauthorized access to cameras, microphones, and voice assistants. High-profile incidents involving hacked baby monitors, indoor cameras, and smart doorbells have significantly increased consumer awareness and regulatory scrutiny.
-
AI in Smart Home Security: AI-powered smart home security features such as facial recognition, behavioral anomaly detection, and predictive alerts are now embedded in 45%+ of new devices sold in 2026. AI improves threat detection but also introduces new risks, including deepfake-based impersonation and AI-assisted device exploitation.
-
Regional Adoption & Risk Differences: North America leads smart home security spending per household, while Europe shows higher regulatory compliance and privacy controls. Asia-Pacific records the fastest growth in both adoption and attack volume, particularly in densely connected urban environments with high IoT device density.
-
Future Outlook: As smart homes evolve into fully connected digital ecosystems, security investment is shifting from standalone devices to end-to-end protection, including encrypted communications, zero-trust device authentication, secure firmware updates, and cloud-level monitoring.
The goal of this report is to update smart home security statistics for 2026, reflecting trends based on major cybersecurity, IoT, and consumer-technology developments in 2024–2025.
What Are Smart Home Security Statistics?
Smart home security statistics are quantifiable measurements that track risks, attacks, vulnerabilities, and protection levels across connected home devices such as smart cameras, video doorbells, smart locks, routers, voice assistants, and IoT hubs. These statistics answer critical questions like: How often are smart home devices compromised? Which devices are most targeted? What security flaws are most common? And how much do security incidents cost consumers?
These numbers are gathered from real-world sources including IoT threat intelligence reports, device vulnerability disclosures, ISP traffic analysis, consumer breach investigations, and smart device manufacturer security audits. Think of smart home security statistics as the vital signs of a connected household—just as a thermostat measures temperature or a smoke detector measures air quality, these metrics reveal how healthy or exposed a smart home ecosystem really is.
For example, global monitoring data shows that IoT and smart home devices now account for a significant share of consumer-facing cyberattacks, with millions of attempted intrusions recorded daily. Studies tracking compromised smart cameras and routers reveal that weak passwords, outdated firmware, and insecure mobile apps remain the most common points of failure. A single statistic—such as 1 in 4 smart home devices containing at least one critical vulnerability—signals systemic security weaknesses across the consumer IoT market.
Why Smart Home Security Matters More Than Ever in 2026
Smart homes provide comfort and efficiency, but they also create digital, physical, and privacy risks if not secured properly.
For Consumers:
Smart-home breaches can expose:
-
Household surveillance footage
-
Personal conversations
-
Daily routines & occupancy patterns
-
Smart lock controls
-
Baby monitor audio/video
-
Wi-Fi credentials
-
Device metadata
-
Location and automation schedules
A compromised thermostat or smart lock is not just a digital problem — it’s a physical safety risk.
For Businesses:
Smart home device manufacturers and app developers face:
-
Regulatory pressure
-
Product liability increases
-
Supply-chain security requirements
-
Rising risks from insecure firmware
-
App-level TLS, API, & cloud security requirements
Device makers are legally and financially accountable for insecure products.
For Cybersecurity Teams:
Smart home devices are now used by:
-
Remote workers
-
Hybrid teams
-
Executives working from home
-
Employees with BYOD work setups
An insecure home device can become a bridge into corporate infrastructure.
Smart Home Adoption & Growth Trends (2026 Update)
Smart home device adoption continues its explosive growth — driven by decreasing prices, simplified installation, automation ecosystems, and the normalization of voice-controlled environments.
2026 Smart Home Adoption Statistics
-
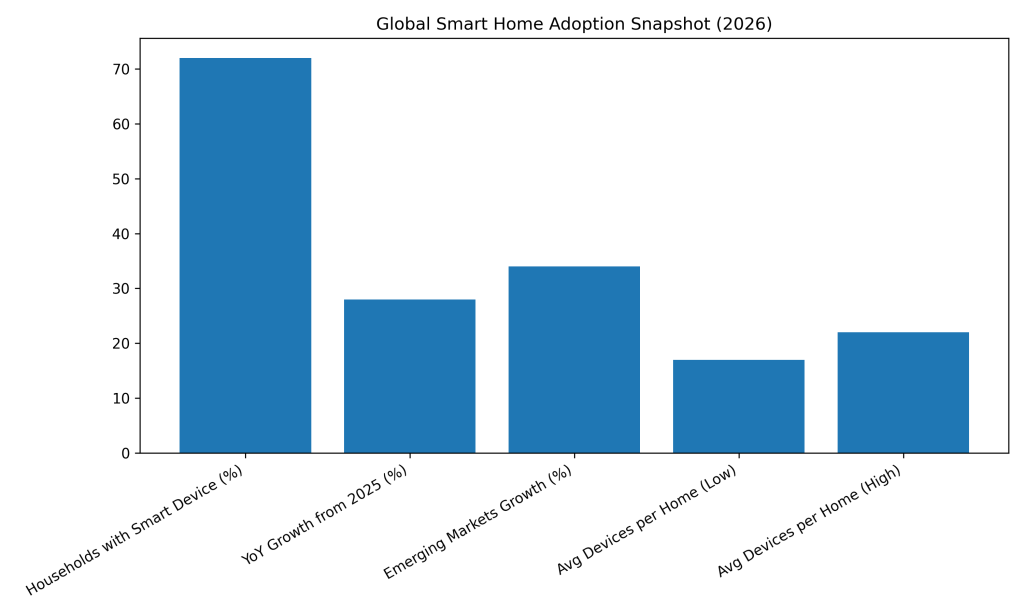
Global households with at least one smart home device: ≈ 72%
-
YoY growth from 2025: +28%
-
Average number of devices per smart home: ≈ 17–22 devices
-
Regions with highest adoption:
-
North America
-
Western Europe
-
East Asia (Japan, South Korea, China)
-
-
Emerging economies adoption growth: ≈ +34% YoY
Drivers Behind Adoption
-
Cheaper IoT hardware
-
Voice assistants as central automation hubs
-
Integration with mobile apps
-
Growth of remote monitoring and home security
-
Home insurance incentives for security systems
-
Smart energy-saving upgrades
With nearly three-quarters of households now smart-enabled, the threat landscape has expanded proportionally.
Smart Home Device Vulnerability Statistics (2026)
IoT devices continue to lag behind other tech categories in security maturity. Many rely on outdated chipsets, unencrypted communication, weak default passwords, and inconsistent firmware support.
Key 2026 Vulnerability Metrics
-
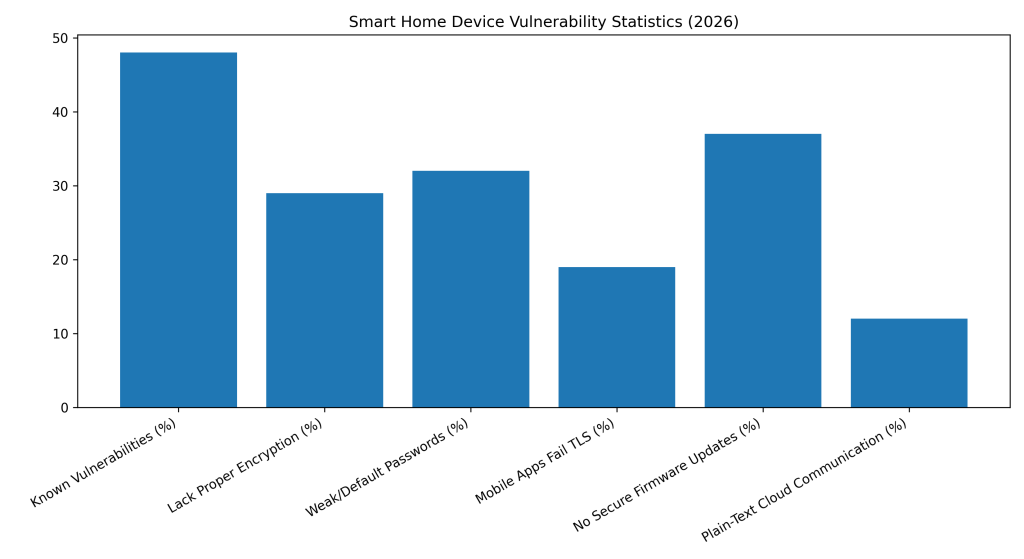
≈48% of smart home devices ship with known security vulnerabilities, exposing users to risks from the moment of installation.
-
Nearly 29% of smart home devices still lack proper encryption, allowing data to be intercepted during transmission.
-
About 32% of smart home devices rely on weak or default passwords, making them easy targets for brute-force attacks.
-
Roughly 19% of smart home mobile apps fail basic TLS certificate validation, weakening secure communication.
-
Around 37% of smart home devices lack secure firmware update mechanisms, leaving known flaws unpatched long term.
-
Approximately 12% of smart home devices communicate with cloud services using unencrypted plain-text channels.
Biggest issues:
-
No forced password changes
-
No TLS certificate validation
-
No software lifecycle support
-
Insecure MQTT or WebSocket connections
-
Misconfigured device pairing protocols
-
Poor mobile app/API security
Attackers routinely exploit these gaps because device owners rarely update firmware or review device permissions.
Smart Home Security Threat Growth (2026)
-
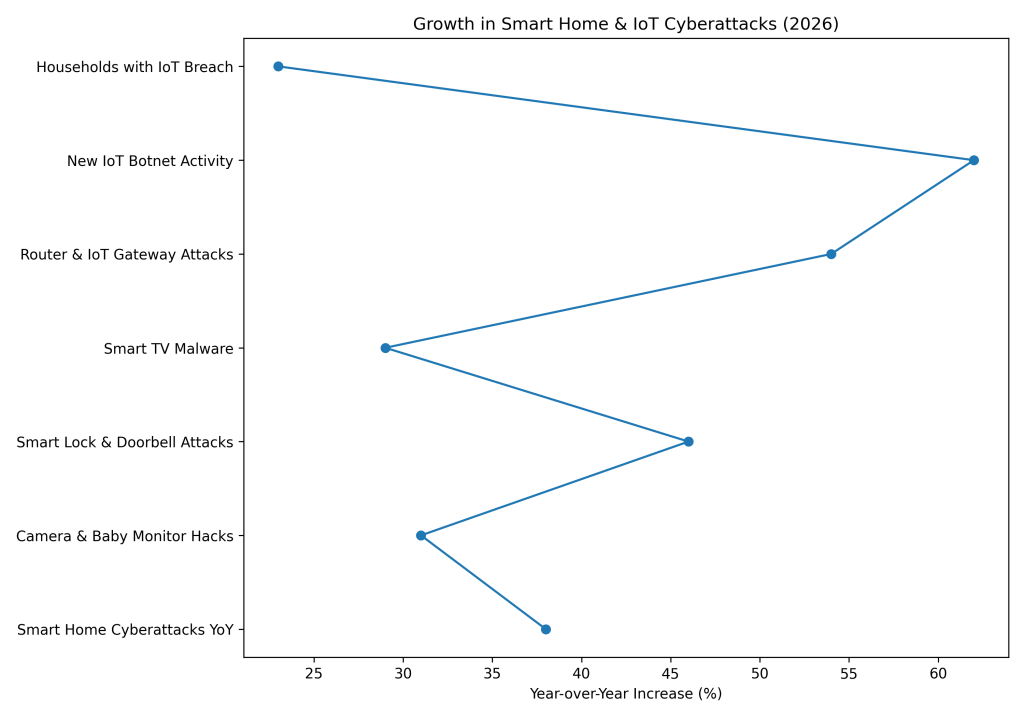
Smart home cyberattacks increased by 38% year over year, driven by rising IoT device density and weak security controls.
-
Smart camera and baby monitor hacking incidents rose 31%, highlighting growing privacy and surveillance risks.
-
Smart lock and video doorbell compromise attempts surged by 46%, raising concerns over physical access security.
-
Smart TV malware infections increased 29%, often spreading through malicious apps and outdated firmware.
-
Home router and IoT gateway attacks jumped 54%, making them the most targeted entry points into smart homes.
-
New IoT botnet activity expanded by 62% year over year, fueled by insecure consumer devices.
-
Approximately 23% of households experienced at least one IoT-related security breach in the past year.
IoT botnets continue to grow aggressively, driven by widespread device vulnerabilities.
Most Targeted Smart Home Devices in 2026
Based on attack trends from 2024–25 and updated 2026 projections, attackers prefer devices with high access value.
Top 10 Most Targeted Smart Home Devices
-
Smart cameras (indoor & outdoor)
-
Baby monitors
-
Smart locks & doorbells
-
Smart TVs & media hubs
-
Smart speakers & voice assistants
-
Home routers & Wi-Fi mesh systems
-
Smart thermostats
-
Connected lighting systems
-
Smart appliances (refrigerators, ovens, washers)
-
Garage door controllers
Why these devices are targeted:
-
They provide physical access signals
-
They expose home audio/video streams
-
They lack strong authentication
-
They run outdated firmware
-
They rely on cloud communication
-
They are rarely monitored by the user
Some device classes also expose sensitive data such as schedules, presence detection, temperature habits, sleep patterns, and home occupancy predictions.
Smart Home Malware & Botnets (2026 Update)
Smart home botnets have become more advanced, modular, and automated.
2026 Botnet Growth Statistics
-
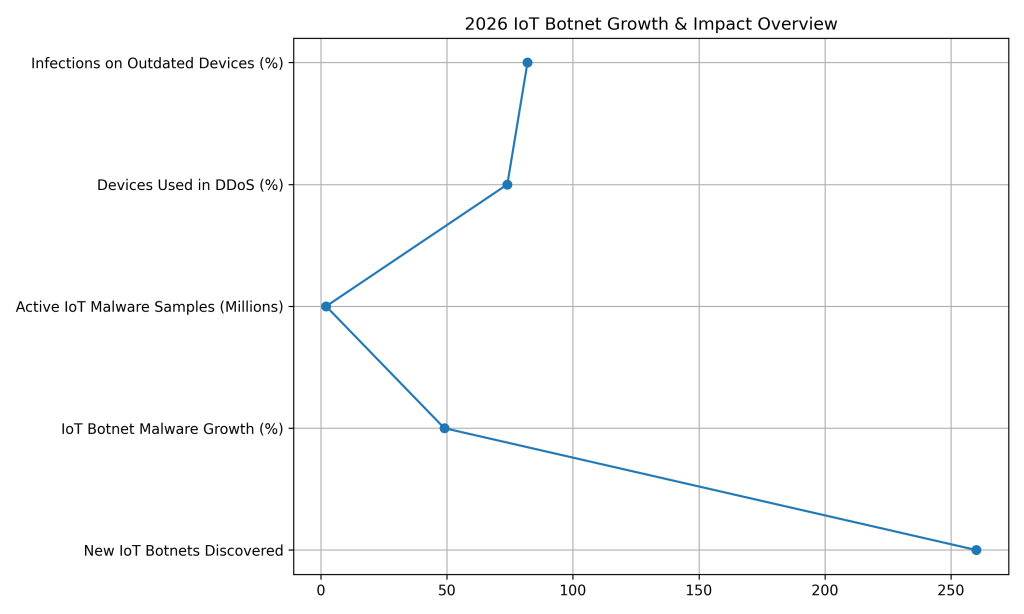
More than 260 new IoT botnets were discovered in 2026, highlighting the rapid expansion of automated IoT threats.
-
IoT botnet malware families increased by roughly 49% year over year, reflecting accelerated attacker innovation.
-
Security researchers detected approximately 2.1 million distinct IoT malware samples actively circulating in 2026.
-
Around 74% of infected smart devices were observed participating in distributed denial-of-service attacks.
-
Nearly 82% of IoT botnet infections persist on outdated smart devices due to missing security updates.
Once compromised, smart home devices often remain infected for years due to lack of updates or poor patch mechanisms.
Common malware behaviors:
-
Joining DDoS botnets
-
Stealing Wi-Fi credentials
-
Recording video/audio
-
Spying through microphones
-
Mining cryptocurrency
-
Brute-forcing other devices
-
Launching internal network scans
-
Man-in-the-middle interception
Home networks without segmentation are especially vulnerable.
Smart Home Privacy Risks in 2026
Privacy erosion is becoming one of the biggest concerns with smart home ecosystems.
2026 Privacy Exposure Metrics:
-
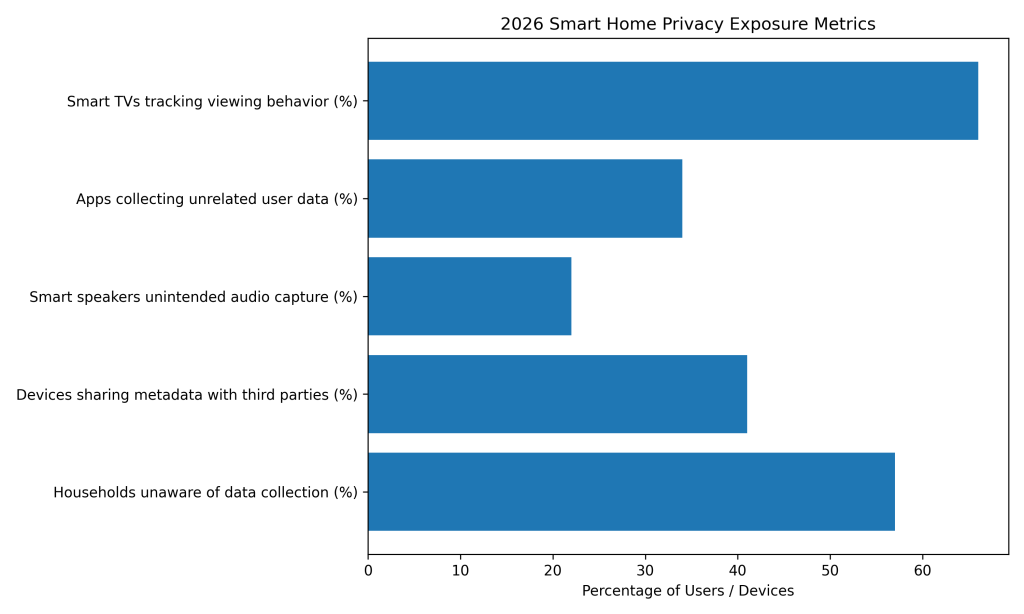
About 57% of households remain unaware of how extensively their smart home devices collect and process personal data.
-
Roughly 41% of smart home devices transmit usage metadata to third-party services beyond core functionality.
-
Approximately 22% of smart speakers capture audio during unintended activations, raising privacy concerns.
-
Nearly 34% of smart home apps collect user data unrelated to the device’s primary function or purpose.
-
Around 66% of smart TVs engage in tracking and ad-based data collection across viewing behavior.
Privacy threats come from:
-
Manufacturers
-
Third-party analytics SDKs
-
Advertisers
-
Cloud misconfigurations
-
App vulnerabilities
-
Weak TLS policies
-
Session token leakage
Attackers exploit these weaknesses to map routines and behaviors of households.
How Hackers Attack Smart Homes in 2026
Smart home cyberattacks in 2026 have expanded far beyond simple Wi-Fi hacking or guessing default passwords. Attackers now leverage automation, AI-driven vulnerability scanning, cross-device pivoting, and exploitation of device-cloud communication channels.
Below are the most common smart home attack methods used in 2026.
Exploiting Weak or Default Passwords
Despite years of awareness, thousands of smart home devices still ship with:
-
admin / admin
-
user / user
-
guest / guest
-
123456
-
qwerty
-
blank passwords
2026 Password Vulnerability Metrics
-
Devices accessed due to default passwords: ≈ 31%
-
Devices still using weak passwords: ≈ 32%
-
Households unaware of device password settings: ≈ 48%
Attackers use bots that scan the internet for vulnerable devices within minutes of them coming online.
Exploiting Insecure Firmware
Firmware remains one of the weakest security layers in IoT devices.
2026 Firmware Security Stats
-
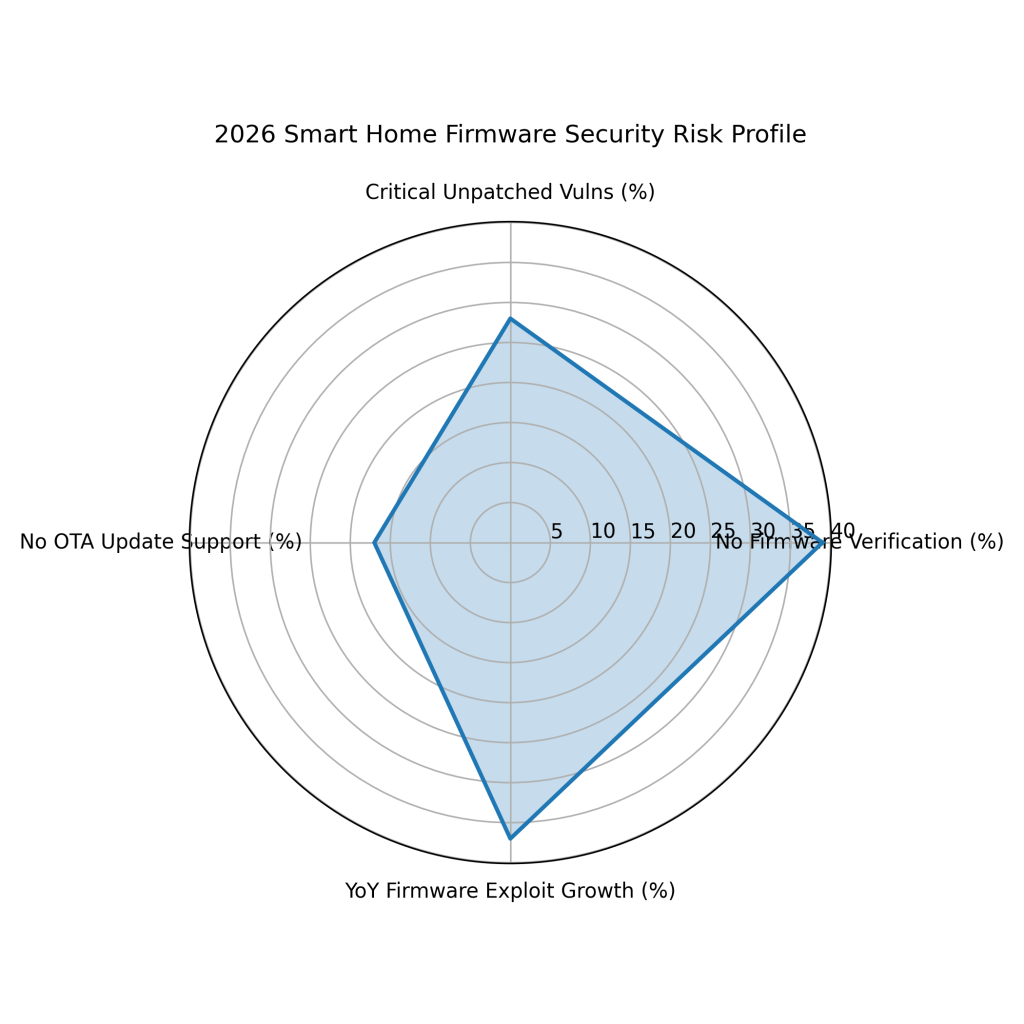
Around 39% of smart home devices lack firmware verification, increasing the risk of malicious code execution.
-
Approximately 28% of smart home devices contain critical unpatched vulnerabilities that attackers can exploit.
-
About 17% of smart home devices do not support OTA updates, making long-term security maintenance difficult.
-
IoT exploits targeting outdated firmware increased by roughly 37% year over year, signaling rising risk.
Firmware exploitation allows attackers to embed persistent malware that survives resets and reboots.
Man-in-the-Middle (MITM) Attacks
MITM remains extremely effective due to:
-
Weak or outdated encryption
-
Apps not validating SSL certificates
-
Plain-text protocols (MQTT, FTP variants)
MITM Attack Statistics 2026
-
Smart home devices vulnerable to MITM: ≈ 19%
-
Smart cameras transmitting data without TLS: ≈ 14%
-
Voice assistants vulnerable to packet interception: ≈ 11%
MITM attacks can allow:
-
Live video interception
-
Audio eavesdropping
-
Device manipulation
-
Credential theft
-
Cloud API hijacking
Brute-Force & Credential-Stuffing Attacks
Attackers recycle credentials from unrelated breaches to compromise smart homes.
2026 Credential Attack Stats
-
Credential-stuffing attempts on smart devices: +44% YoY
-
Home security camera brute-force attempts: ≈ 180 million/month globally
-
Accounts compromised due to reused passwords: ≈ 23%
Remote access features — especially those using weak authentication — are prime targets.
Malicious Smart Home Apps
Attackers distribute fake smart home apps mimicking:
-
Camera apps
-
Lighting apps
-
Smart lock controllers
-
Home automation hubs
2026 Malicious App Stats
-
Malicious smart home apps detected: ≈ 12,000+
-
YoY growth of fake IoT apps: +46%
-
Users who installed at least one risky IoT-related app: ≈ 18%
These apps steal credentials, access cameras, or hijack device controls.
Wireless Attack Surfaces in Smart Homes (2026)
Smart homes rely heavily on wireless communication standards. Each introduces unique risks.
Wi-Fi (Most Common Attack Surface)
2026 Wi-Fi Security Stats
-
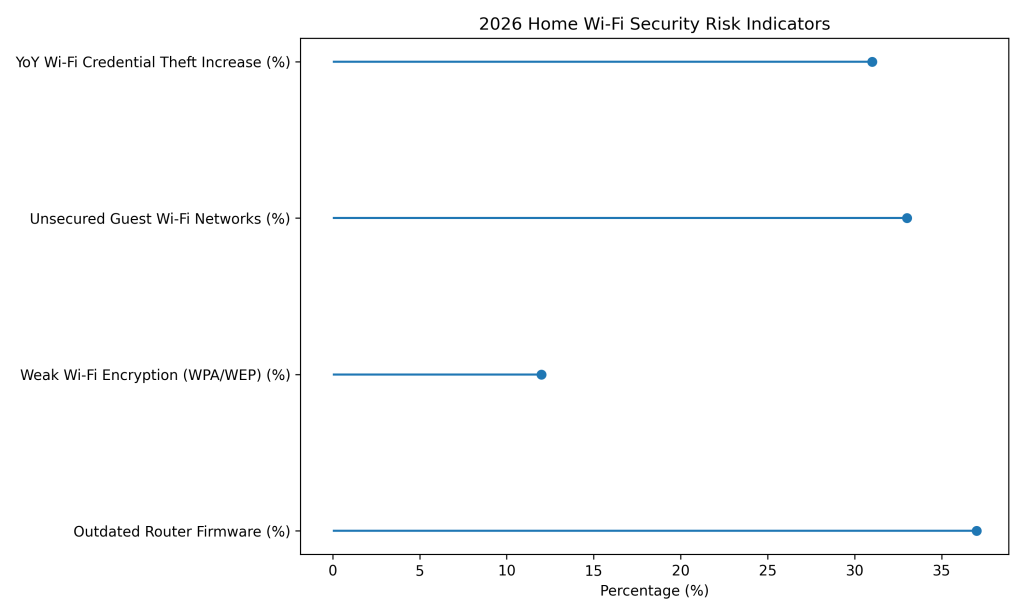
Around 37% of home routers operate on outdated firmware, leaving known vulnerabilities unpatched and exploitable.
-
Approximately 12% of home routers still use weak Wi-Fi encryption such as WPA or WEP, increasing intrusion risk.
-
About 33% of households maintain unsecured guest Wi-Fi networks that attackers can easily abuse for access.
-
Wi-Fi credential theft incidents have increased by roughly 31% year over year, driven by phishing and malware
Compromising the router gives attackers full visibility into the home network.
Zigbee Vulnerabilities (2026 Update)
Zigbee is widely used in:
-
smart bulbs
-
plugs
-
switches
-
locks
-
thermostats
2026 Zigbee Attack Stats
-
About 22% of Zigbee-based smart home devices remain vulnerable during the pairing process, exposing networks at setup.
-
Nearly 28% of Zigbee devices continue to run outdated firmware, increasing exposure to known security flaws.
-
Replay attacks targeting Zigbee smart home networks increased by approximately 34% year over year.
Zigbee mesh networks allow attackers to pivot quickly between devices.
Z-Wave Attack Trends
Z-Wave is used in many security-focused devices:
-
alarms
-
motion sensors
-
smart locks
2026 Z-Wave Stats
-
Devices vulnerable to downgrade attacks: ≈ 14%
-
Z-Wave S0 encryption weaknesses exploited: +27%
-
Devices with insecure pairing keys: ≈ 11%
Downgrade attacks allow the attacker to force weaker encryption.
Bluetooth Low Energy (BLE) Risks
BLE is used in:
-
wearables
-
health devices
-
proximity sensors
-
locks
-
speakers
2026 BLE Stats
-
BLE sniffing attacks increased: +36% YoY
-
Devices vulnerable to unauthorized pairing: ≈ 19%
-
BLE replay attacks: +29%
Attackers exploit BLE to unlock doors, hijack audio, or manipulate health-device data.
Smart Home App & API Security in 2026
Most smart home devices rely on companion mobile apps and cloud-based APIs. This dramatically enlarges the attack surface.
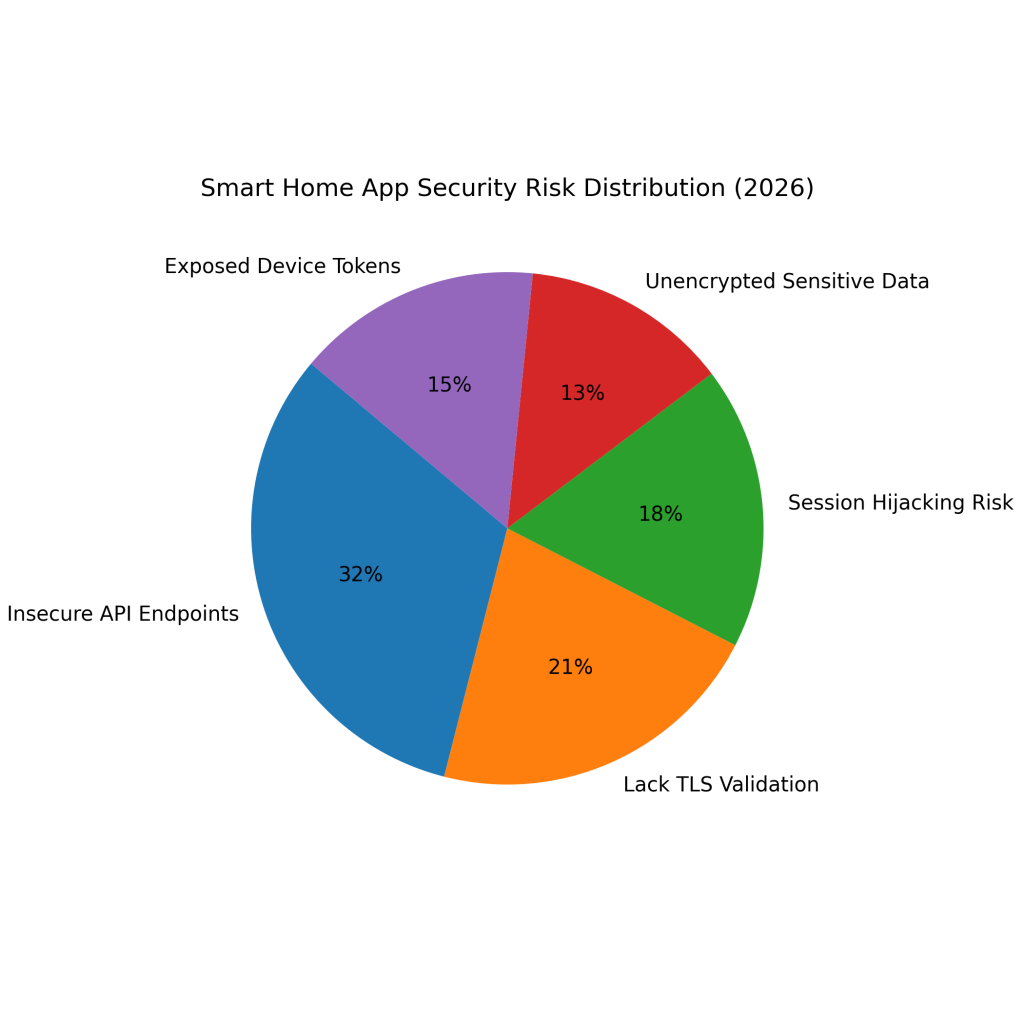
Smart Home App Security Statistics (2026)
-
18% of smart home apps lack proper TLS certificate validation, increasing the risk of man-in-the-middle attacks.
-
Around 11% of smart home apps transmit sensitive user data without encryption, exposing privacy-critical information.
-
Approximately 27% of smart home apps use insecure API endpoints that attackers can exploit to access devices remotely.
-
About 15% of smart home apps are vulnerable to session hijacking, allowing unauthorized account access.
-
Roughly 13% of smart home apps expose device tokens, making it easier for attackers to control connected devices.
Apps are often the weakest link in otherwise secure device ecosystems.
API Vulnerabilities in Smart Home Ecosystems
APIs control:
-
device pairing
-
user authentication
-
cloud synchronization
-
camera feeds
-
automation routines
-
remote-control functions
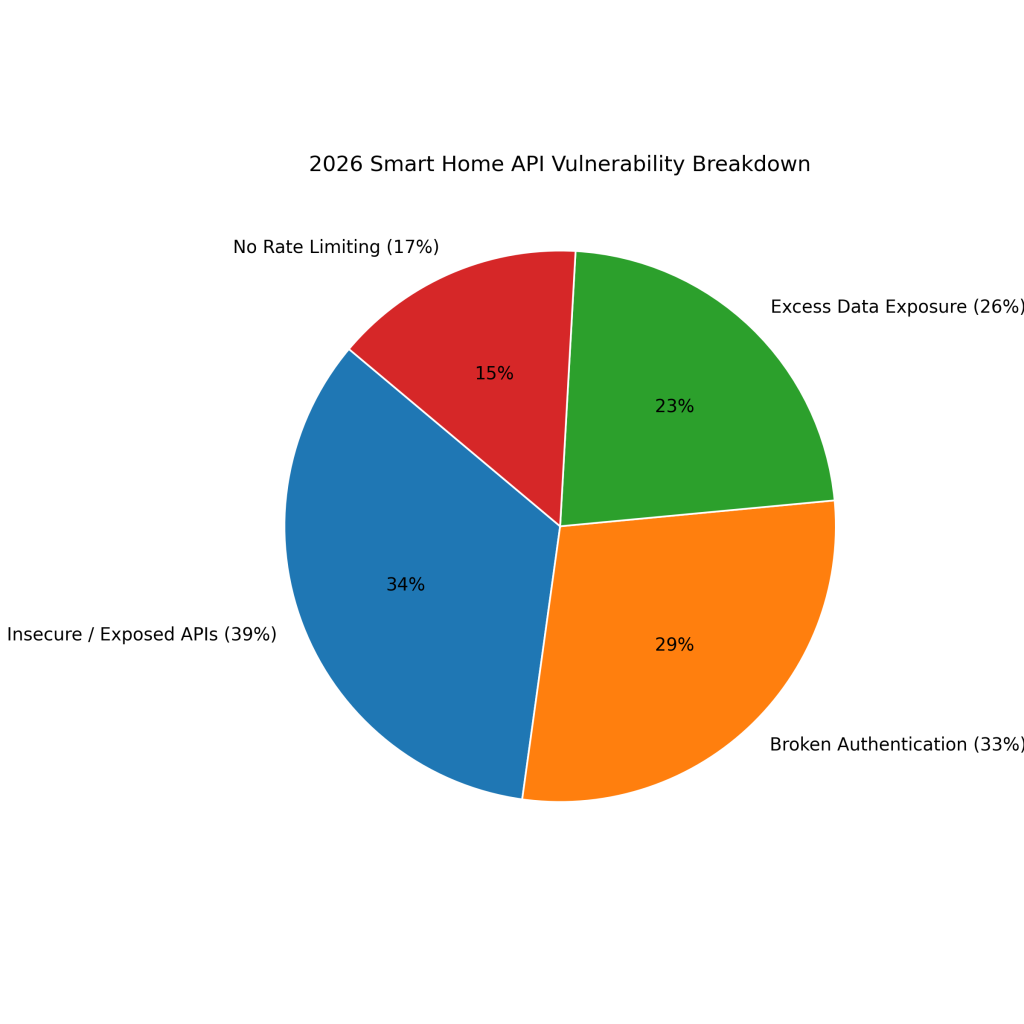
2026 API Vulnerability Stats
-
About 39% of smart home security issues stem from insecure or improperly protected APIs exposed to attackers.
-
Approximately 33% of smart home vulnerabilities involve broken authentication, enabling unauthorized device or account access.
-
Nearly 26% of smart home platforms expose excess user or device data beyond what is functionally required.
-
Around 17% of smart home systems lack proper rate limiting, increasing exposure to brute-force and abuse attacks.
API flaws are exploited to:
-
take over devices
-
alter automation schedules
-
unlock smart locks
-
disable cameras
-
steal user data
Cloud Dependencies & Supply Chain Security (2026 Update)
Smart home devices rely heavily on cloud servers to function. This creates systemic risks.
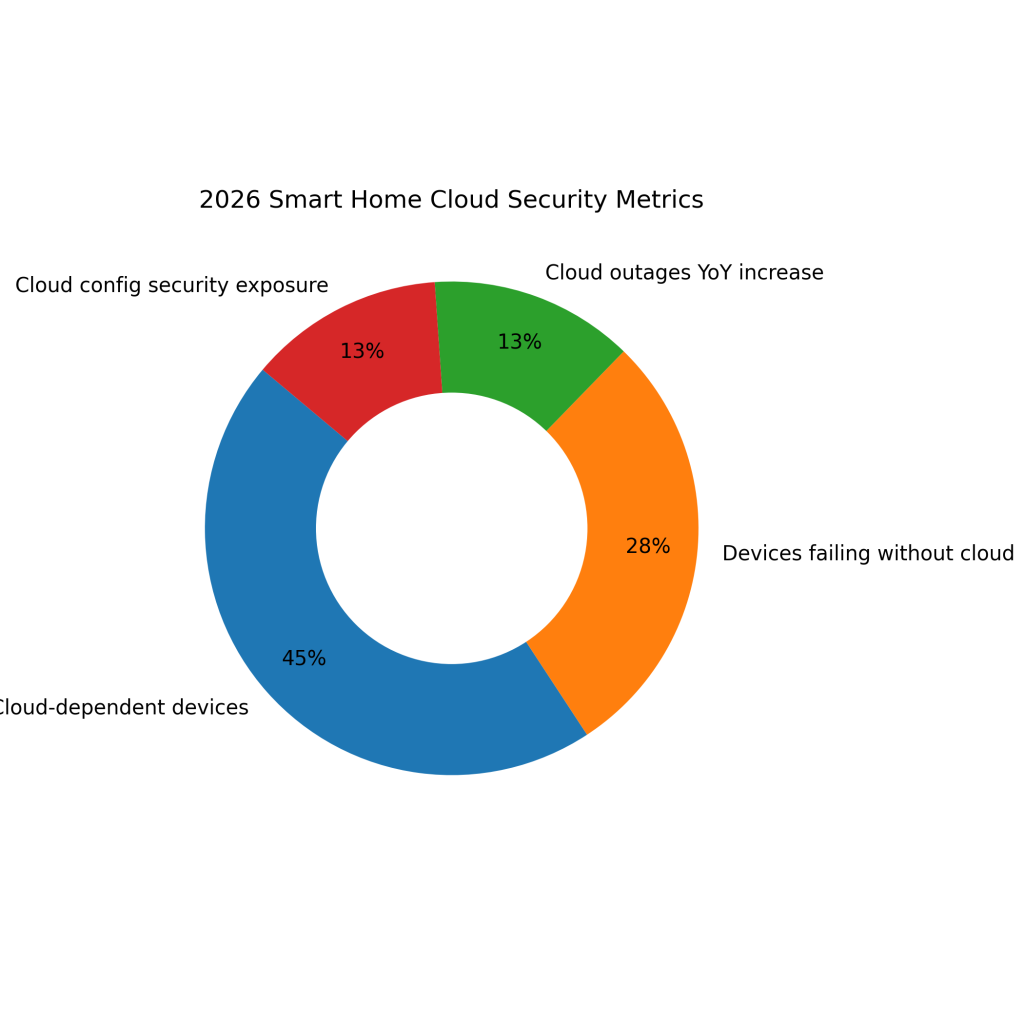
2026 Cloud Security Metrics
-
Around 78% of smart home devices depend on cloud services for core functionality and remote access.
-
Nearly 49% of smart home devices partially or fully stop functioning when cloud connectivity is unavailable.
-
Smart home cloud service outages increased by approximately 23% year over year, impacting device reliability.
-
About 22% of smart home devices are exposed to security risks due to cloud configuration weaknesses.
Supply Chain Risks
-
Unpatched vulnerabilities in cloud SDKs
-
Data leaks through misconfigured servers
-
API keys exposed in app code
-
Hardcoded passwords in firmware
Smart home security is only as strong as the weakest component in the supply chain.
Smart Home Payment & Subscription Fraud
The subscription economy for smart home services (cloud storage, AI features, video history, automation) has created new financial risks.
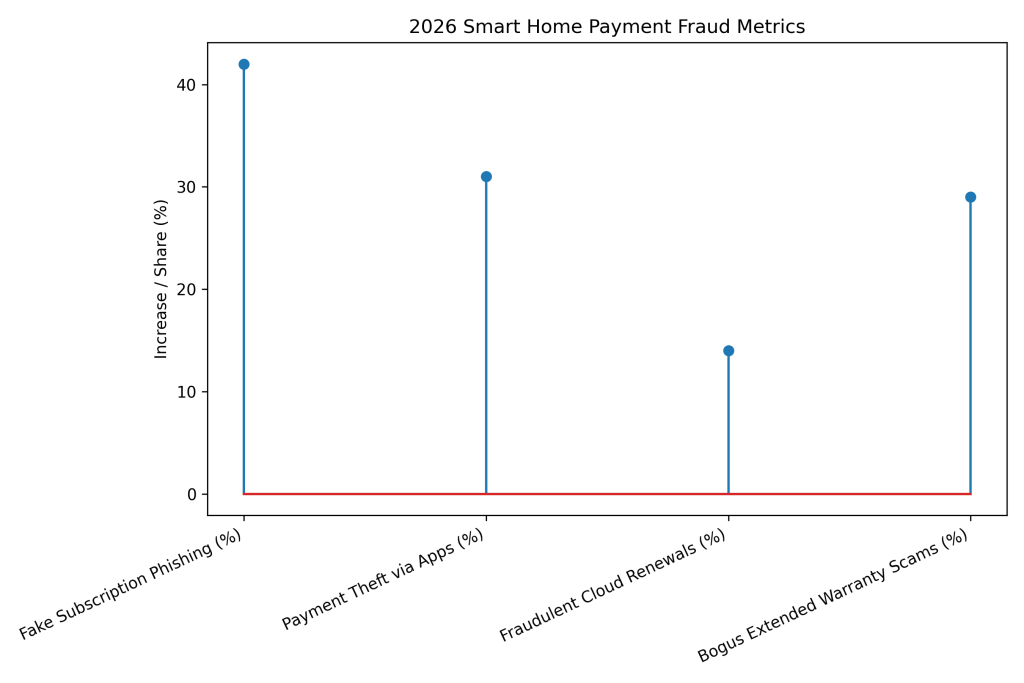
2026 Smart Home Payment Fraud Metrics
-
Fake subscription pages linked to phishing scams rose by 42%, targeting smart home users with renewal traps.
-
Payment method theft via compromised smart home apps increased 31%, exposing stored card details.
-
Fraudulent cloud storage renewal pages now account for roughly 14% of smart home–related phishing cases.
-
Scams involving bogus “extended warranty” services grew 29%, exploiting smart device ownership fears.
Attackers now focus on stealing:
-
payment card details
-
recurring billing credentials
-
autopay tokens
-
subscription login details
Impact of AI on Smart Home Threats (2026)
AI accelerates smart home cybercrime dramatically.
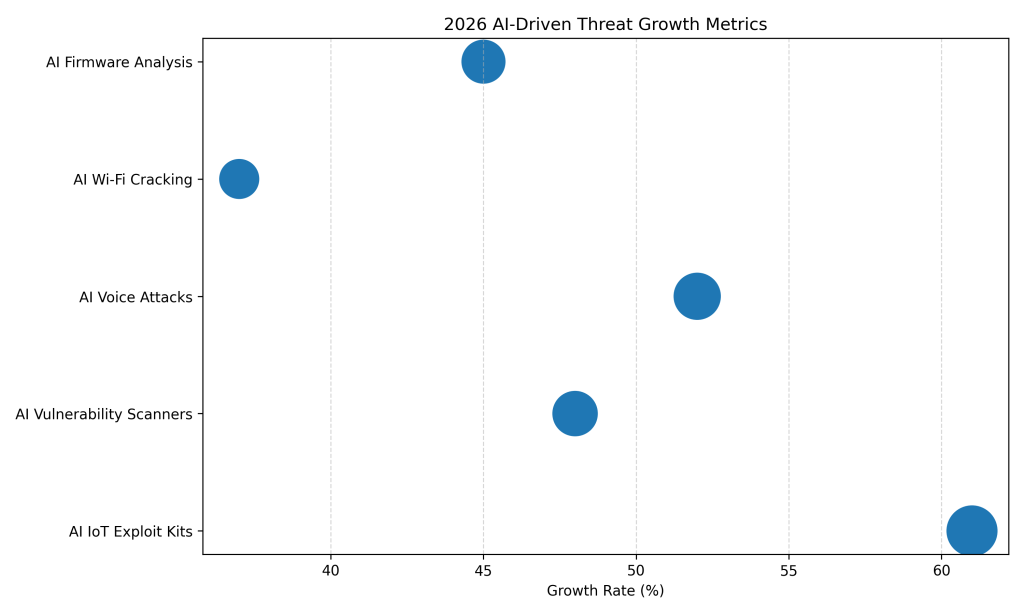
2026 AI Threat Growth Metrics
-
AI-driven IoT exploit kits increased by 61%, enabling faster and more scalable attacks against smart home devices.
-
AI-powered vulnerability scanners targeting IoT environments grew by 48%, accelerating device discovery and exploitation.
-
AI-based voice manipulation attacks on smart speakers rose 52%, enabling unauthorized commands and account takeovers.
-
AI automation used for Wi-Fi cracking attempts increased by 37%, reducing the effort needed to breach home networks.
-
AI-based firmware analysis tools grew by 45%, allowing attackers to identify flaws in embedded smart device code faster.
How Attackers Use AI in Smart Home Environments
1. Voice Assistant Manipulation
AI-generated voice prompts can trigger:
-
purchases
-
automation commands
-
unlocking devices
-
disabling alarms
2. Automated Vulnerability Discovery
AI scans smart devices and firmware to find:
-
open ports
-
weak encryption
-
outdated libraries
-
buffer overflow points
3. Smart Camera Hijacking
AI tools analyze video streams to:
-
detect absence
-
monitor patterns
-
extract sensitive visuals
4. Device Spoofing & Identity Cloning
Attackers spoof devices to intercept commands or impersonate legitimate IoT hardware.
5. Large-Scale Botnet Scaling
AI controls massive IoT botnets with minimal human action.
Security Risks by Smart Home Device Category (2026 Deep Dive)
Different smart home devices introduce different levels of risk. In 2026, the most compromised categories expose sensitive data such as video streams, physical access, and daily behavioral patterns.
Smart Cameras & Baby Monitors
Smart cameras remain the #1 most attacked smart home device category in 2026.
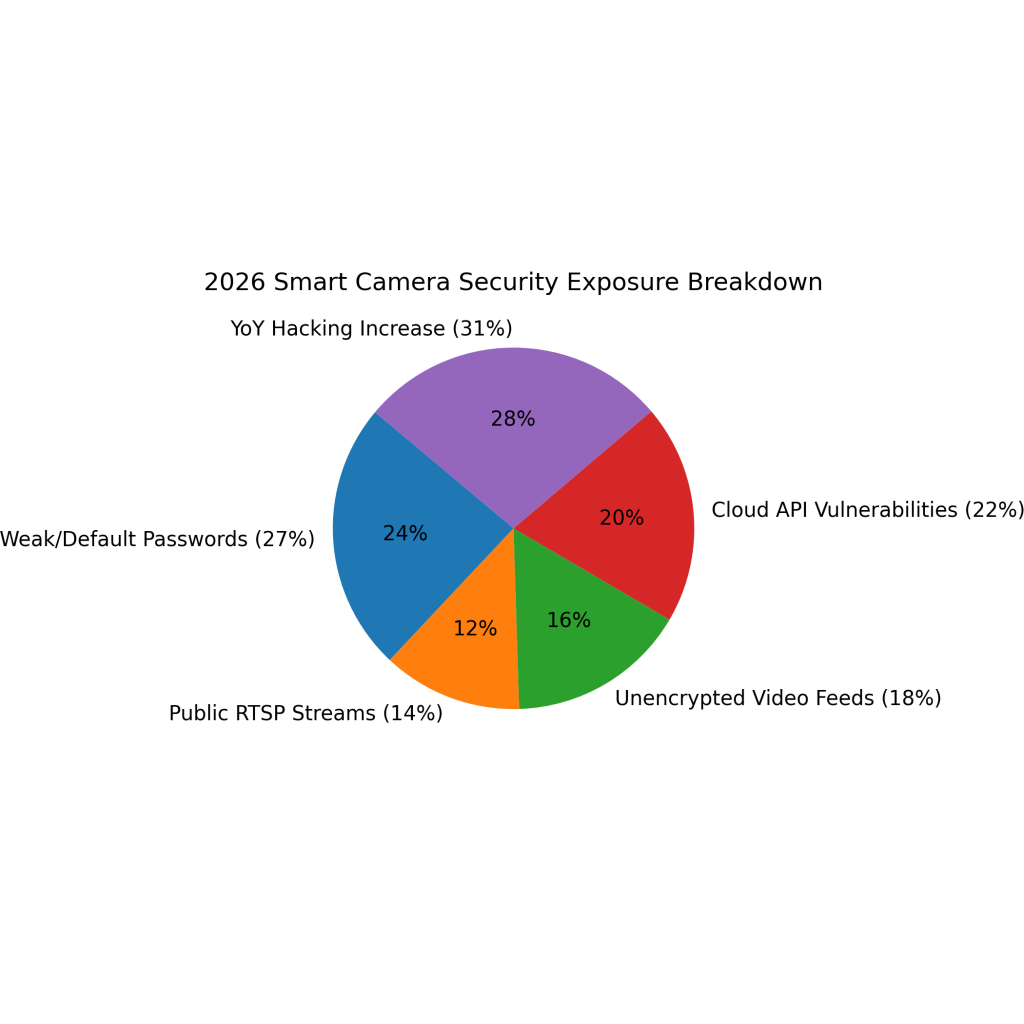
2026 Camera Security Metrics
-
Smart camera hacking incidents increased by approximately 31% year over year, driven by poor device security.
-
About 14% of smart cameras expose RTSP video streams publicly, enabling unauthorized remote viewing.
-
Roughly 27% of smart cameras still use weak or default passwords, making account takeovers easier.
-
Nearly 18% of smart cameras transmit video feeds without full encryption, increasing privacy risks.
-
Around 22% of smart cameras are vulnerable to cloud API flaws that can allow remote exploitation.
Common Camera Attack Outcomes
-
Live feed hijacking
-
Video archival theft
-
Motion detection disabling
-
Stalkerware installation
-
Home occupancy tracking
Baby monitor attacks increased by 29%, with criminals targeting audio/video streams and sometimes using two-way audio to harass or intimidate households.
Smart Locks & Doorbells
Smart locks introduce direct physical security risks if compromised.
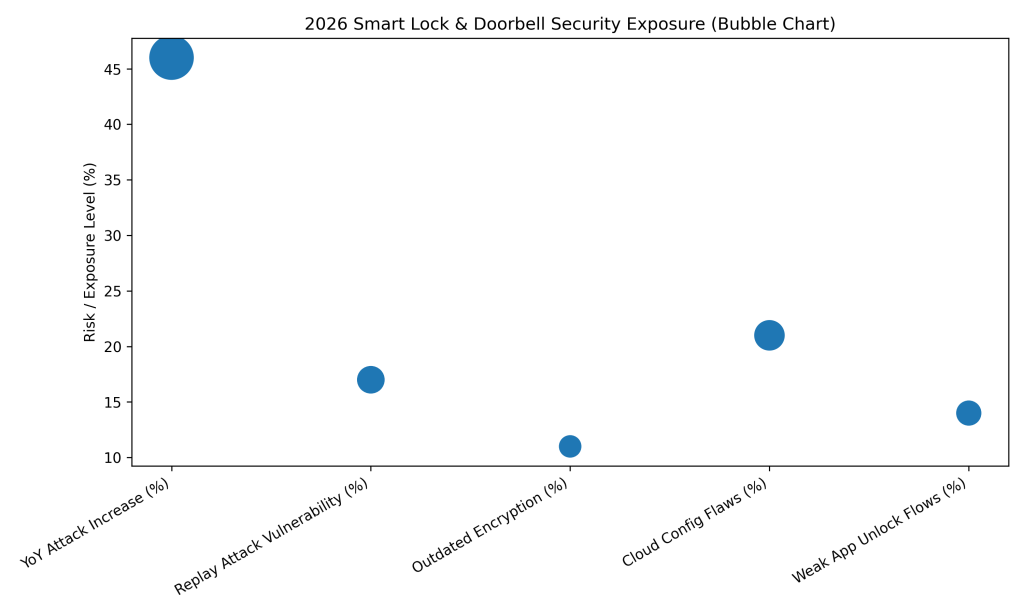
2026 Smart Lock Security Stats
-
Attempts to compromise smart locks increased by 46% year over year, highlighting rising physical access risks.
-
Approximately 17% of smart locks remain vulnerable to replay attacks that can bypass basic authentication.
-
About 11% of smart locks still rely on outdated encryption algorithms that no longer meet modern standards.
-
Roughly 21% of smart doorbells show cloud configuration flaws that expose footage and user data.
-
Nearly 14% of smart locks use weak app-based unlocking flows, increasing the risk of unauthorized access.
Common Smart Lock Exploits
-
BLE spoofing
-
Zigbee/Z-Wave downgrade attacks
-
Password brute-force against mobile apps
-
Cloud API hijacking
-
PIN code extraction from poor logging practices
A compromised smart lock gives attackers precise entry opportunities based on household routines.
Smart Speakers & Voice Assistants
Voice assistants have become universal in modern households, but they introduce several privacy and command-injection vulnerabilities.
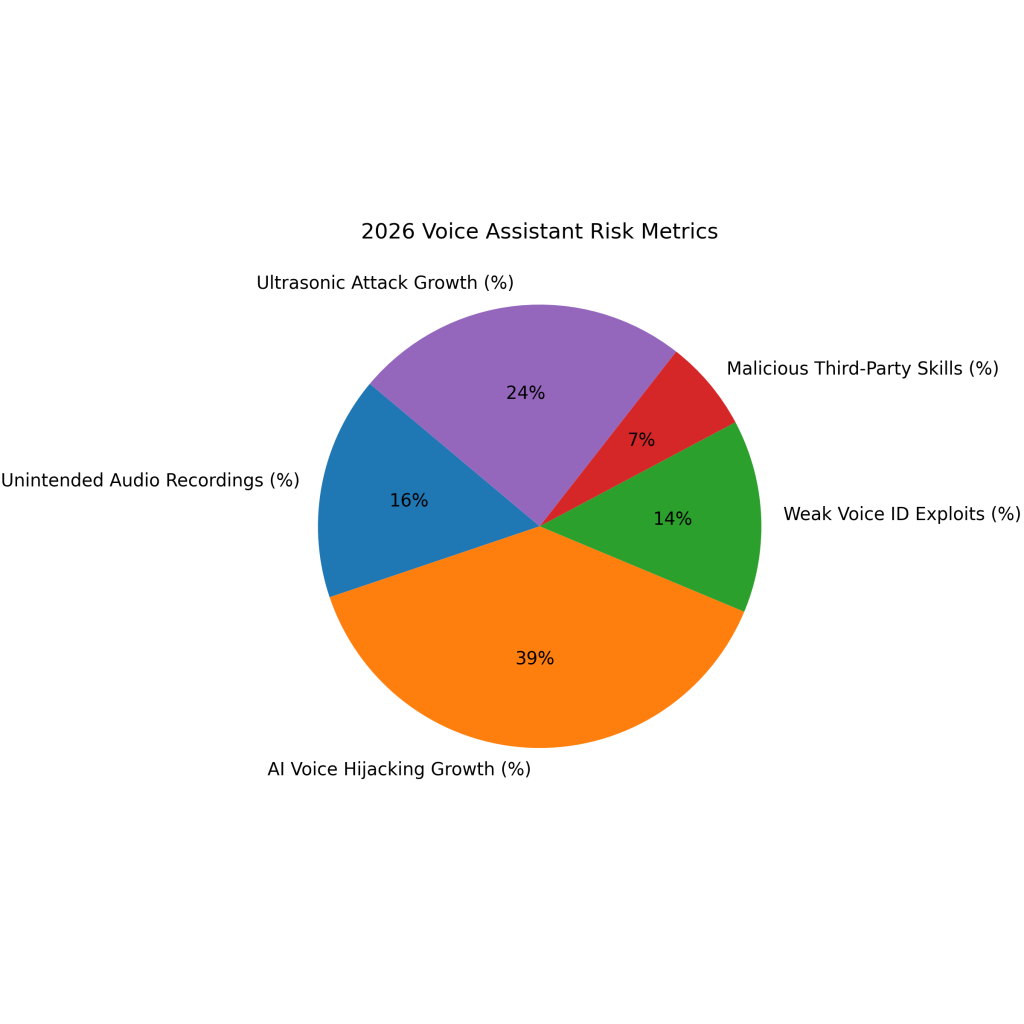
2026 Voice Assistant Risk Metrics
-
About 22% of smart home users report unintended audio recordings caused by accidental or false voice triggers.
-
Voice hijacking attacks using AI-mimicked voices increased by approximately 52%, raising identity spoofing risks.
-
Nearly 19% of voice assistant breaches exploit weak or poorly implemented voice ID authentication controls.
-
Roughly 9% of third-party voice assistant skills or apps exhibit malicious or privacy-invasive behavior.
-
Ultrasonic voice attacks that silently trigger assistants increased by about 33% year over year.
Attacks include:
-
Unauthorized purchases
-
Command spoofing
-
Personal data extraction
-
Unlocking connected smart devices
-
Manipulating home automation routines
AI voice cloning has dramatically increased unauthorized activation incidents.
Smart TVs & Media Hubs
Smart TVs are increasingly targeted due to:
-
Built-in browsers
-
Microphones
-
Cameras
-
Advertising SDKs
-
App stores
-
Weak update cycles
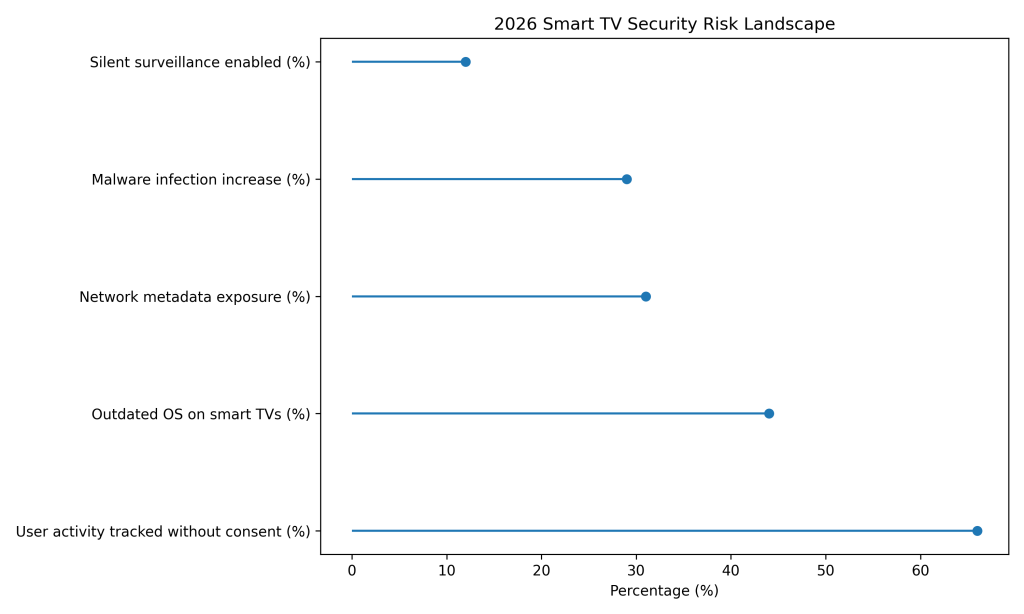
2026 Smart TV Security Metrics
-
Smart TV malware infections increased by 29%, highlighting growing abuse of under-secured home entertainment systems.
-
Approximately 44% of smart TVs run outdated operating systems, leaving known vulnerabilities unpatched.
-
Around 31% of smart TVs expose internal network metadata, increasing the risk of lateral home network attacks.
-
An estimated 66% of smart TVs collect or track user activity without clear or informed user consent.
-
About 12% of compromised smart TVs enable silent surveillance features, including unauthorized screen or audio monitoring.
Smart TVs often become a stepping stone into internal home networks.
Smart Appliances (Refrigerators, Ovens, Washers, Etc.)
Though less critical than cameras or locks, these devices still introduce cyber and physical safety concerns.
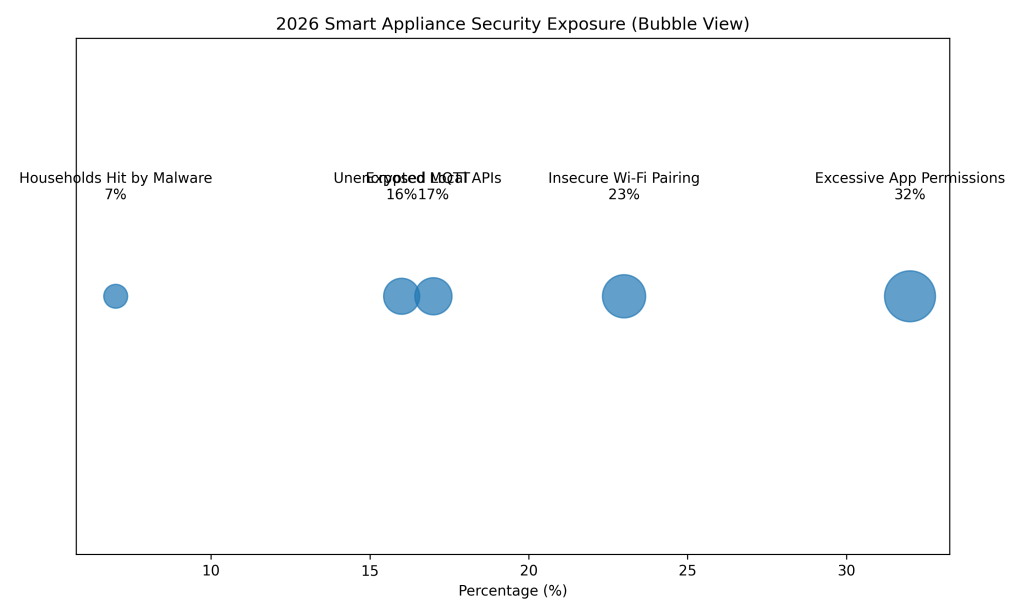
2026 Smart Appliance Stats
-
About 23% of smart home devices use insecure Wi-Fi pairing methods, increasing the risk of unauthorized network access.
-
Nearly 17% of smart appliances expose local APIs, allowing attackers to interact with devices on the same network.
-
Roughly 16% of smart home devices transmit data using unencrypted MQTT protocols, enabling traffic interception.
-
Approximately 32% of smart home apps request excessive permissions, expanding the potential impact of a compromise.
-
Around 7% of households report smart appliance misbehavior caused by malware or unauthorized device manipulation.
Appliances are increasingly network-connected but rarely security-hardened.
Home Routers & Mesh Systems (Critical Attack Surface)
Home routers are the gateway to the entire smart home.
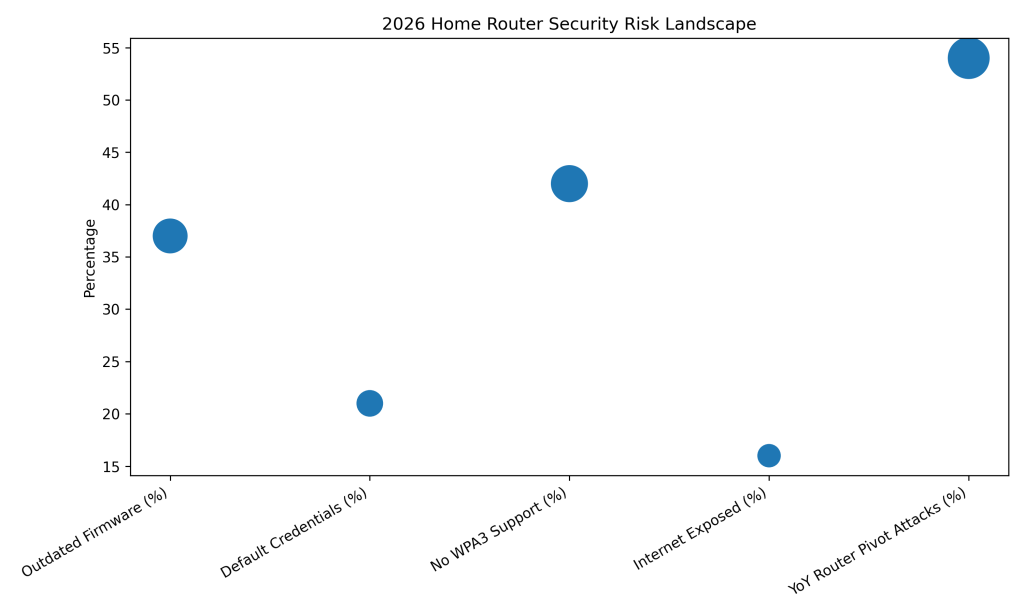
2026 Router Security Metrics
-
About 37% of home routers run outdated firmware, leaving known vulnerabilities open to remote exploitation.
-
Roughly 21% of home routers still use default login credentials, making unauthorized access trivial for attackers.
-
Nearly 42% of consumer routers lack WPA3 support, weakening wireless security against modern attack techniques.
-
Around 16% of home routers remain exposed to the internet due to UPnP misconfigurations and open ports.
-
Router-based attacks used to pivot into smart home IoT networks increased by approximately 54% year over year.
Compromising the router makes all connected devices vulnerable.
Consumer Behavior, Misconfigurations & Awareness Gaps (2026)
The human factor remains one of the weakest links in smart home security.
Password Hygiene & Authentication Behavior
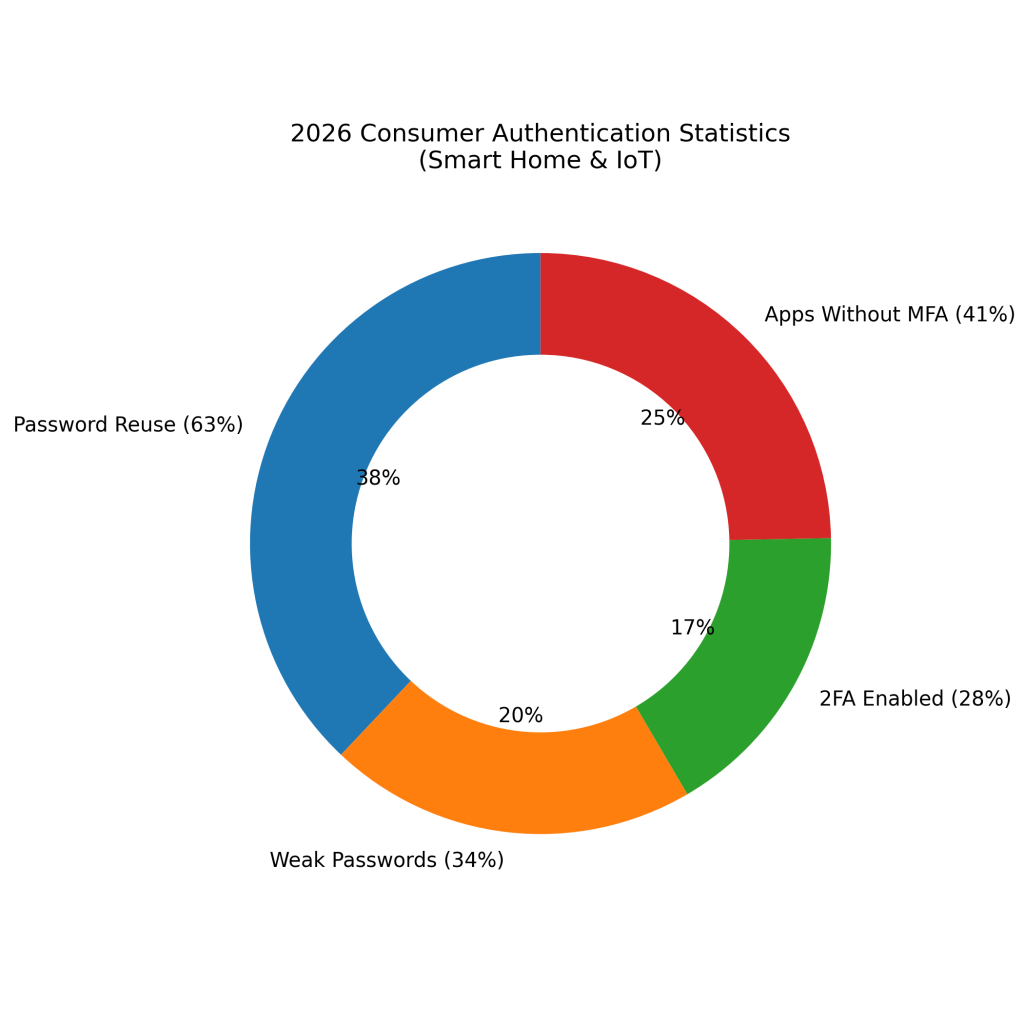
2026 Consumer Authentication Statistics
-
Around 63% of users reuse passwords across smart home apps, increasing the risk of account takeover attacks.
-
Approximately 34% of smart home users still rely on weak passwords that are easily guessed or brute-forced.
-
Only about 28% of households enable two-factor authentication for smart home or IoT accounts.
-
Roughly 41% of smart home applications still do not support multi-factor authentication for user logins.
Reused credentials from unrelated breaches commonly enable IoT hijacking.
Firmware and Software Update Behavior
Smart homes accumulate devices that owners forget to maintain.
2026 Update Adoption Metrics
-
Users who never update their smart device firmware: ≈ 39%
-
Devices left unpatched for over 12 months: ≈ 34%
-
Users unaware updates exist: ≈ 47%
Why updates fail:
-
Manual update processes
-
Complex app paths
-
Unclear manufacturer communication
-
Devices abandoned by manufacturers
Awareness of IoT App Permissions & Data Access
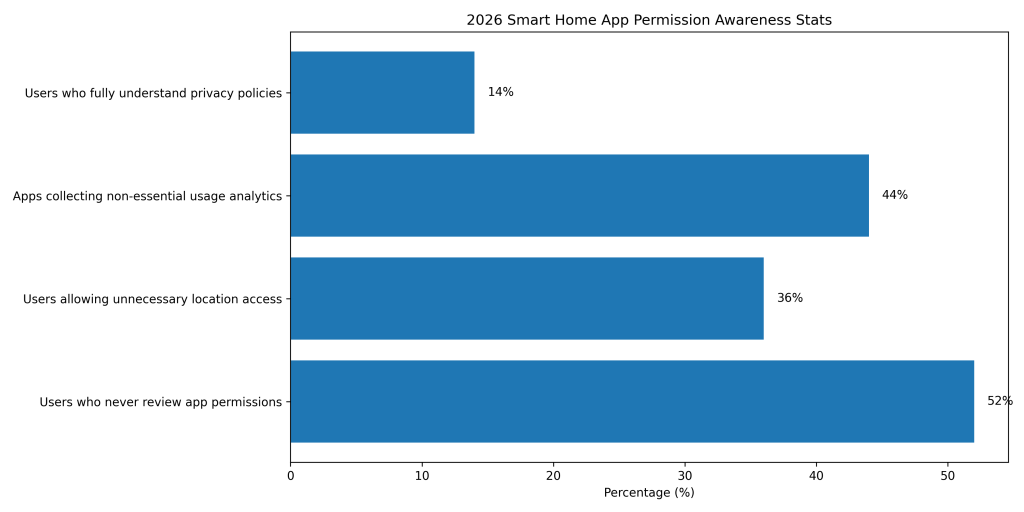
2026 App Permission Awareness Stats
-
Around 52% of smart home users never review app permissions, unknowingly granting excessive access.
-
Approximately 36% of users allow location access for smart devices that do not require it.
-
Nearly 44% of smart home apps collect unnecessary usage analytics beyond core functionality.
-
Only about 14% of users fully understand smart home privacy policies before accepting them.
Smart Home Network Misconfigurations
Improperly configured networks create major vulnerabilities.
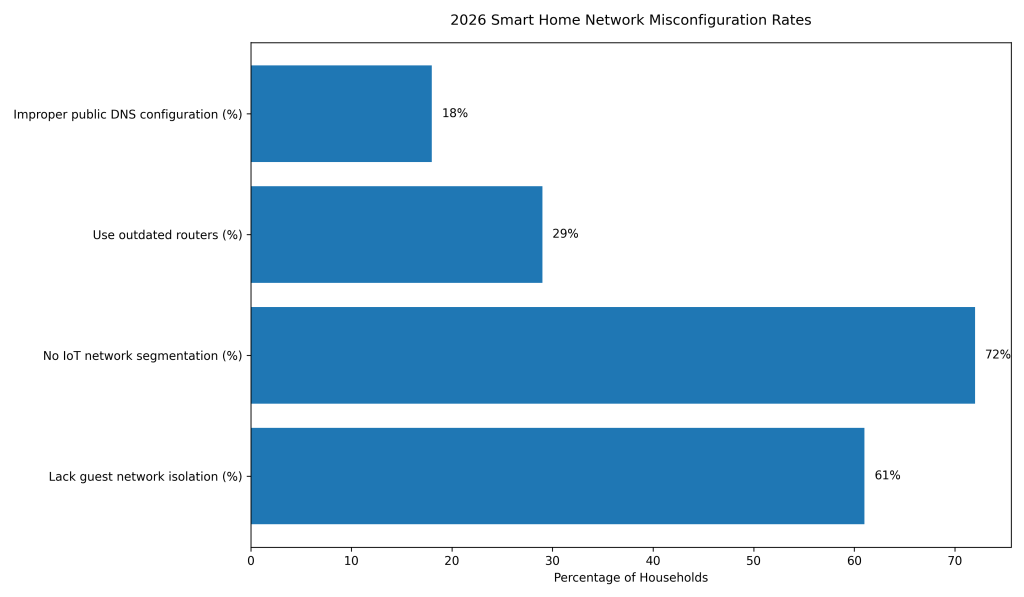
2026 Network Misconfiguration Rates
-
Approximately 61% of smart homes lack guest network isolation, increasing exposure from visitor and third-party devices.
-
About 72% of homes do not use IoT network segmentation, allowing compromised devices to access the main network.
-
Nearly 29% of households continue using outdated routers, often missing critical security patches and protections.
-
Roughly 18% of homes use public DNS resolvers with improper configuration, weakening network-level security controls.
Network segmentation remains one of the most powerful — yet underutilized — defenses.
Insurance, Compliance & Regulatory Pressures (2026 Update)
Governments and insurers are responding to smart home risks with stricter policies.
Smart Home Insurance Trends (2026)
Insurance Risk Metrics
-
Claims involving smart home device compromise: ≈ 11% of cyber-related home claims
-
Insurance premium increases for IoT-heavy homes: +14–22%
-
Discounts for homes with certified smart security: 8–12%
Insurers now evaluate:
-
device types
-
security posture
-
firmware update history
-
network configuration
-
encryption support
Regulatory Evolution
2026 Smart Home Regulation Trends
-
Mandatory security labeling in multiple regions
-
Required disclosure of data-collection practices
-
Minimum security standards for IoT devices
-
Penalties for selling devices with known vulnerabilities
By late 2026, many jurisdictions adopt:
-
secure-by-design requirements
-
forced password change compliance
-
built-in firmware update capabilities
Manufacturers who fail risk legal consequences and bans from major markets.
Smart Home Breach Costs & Consequences (2026)
The financial impact of smart home breaches is growing due to:
-
Privacy lawsuits
-
Property theft
-
Identity theft
-
Device replacement
-
Home insurance claims
-
Lost productivity
-
Emotional distress
2026 Breach Cost Statistics
-
Average cost per smart home breach: $1,100–$4,900
-
Households facing repeated IoT breaches: ≈ 13%
-
Average time to detect a smart home compromise: ≈ 14 days
-
Costliest attack types:
-
Smart lock compromise
-
Camera hijacking
-
Home network takeover
-
Identity theft via IoT apps
-
Physical, digital, and financial damage overlap heavily in smart home breaches.
Future Trends: Smart Home Security Predictions for 2027 and Beyond
Smart homes in 2027 will be even more interconnected, AI-driven, and cloud-dependent than in 2026. With that growth comes rising risk, more sophisticated hacking methods, and increased government involvement in product security.
Below are the most realistic, high-confidence predictions for smart home security in 2027.
Smart Home Device Adoption Will Surpass 80% Globally
With falling device costs and integration with home insurance, energy savings, and automation ecosystems, smart home penetration is expected to exceed:
-
82% of global households by 2027
-
Market size reaching ~$260–$290 billion
-
Average device count per home rising to 22–28 devices
This creates an exponentially larger attack surface for cybercriminals.
Mandatory Security Standards for IoT Devices Will Expand
More countries will adopt:
-
Security rating labels
-
Minimum encryption standards
-
Required support-timeframes for firmware updates
-
Mandatory password changes
-
Disclosure of data-sharing behavior
-
Penalties for insecure-by-design devices
By 2027, regulators may require:
-
TLS 1.2+ mandatory for all cloud communication
-
Prohibition of default passwords
-
Required documentation of API security
Manufacturers who do not comply risk losing access to major markets.
AI-Based Smart Home Attacks Will Double
AI adoption by attackers will grow even faster:
-
Voice cloning to manipulate voice assistants
-
AI bots scanning local home networks
-
Automated vulnerability exploitation
-
Smart device impersonation
-
Behavioral pattern analysis (AI predicting homeowner routines)
By 2027, smart homes must implement AI-assisted defenses to keep up.
Universal Smart Home Identity Will Become a Requirement
Smart homes will adopt a universal “device identity” standard allowing:
-
Device attestation
-
Device trust scoring
-
Secure onboarding
-
Standardized update paths
Home routers and hubs will act as “identity authorities” for IoT devices.
Smart Homes Will Be Targeted for Corporate Espionage
As remote work rises:
-
IoT device compromise enables audio/video surveillance
-
Attackers can infiltrate corporate networks through home devices
-
Compromised routers become footholds for lateral movement
Executives and high-value employees will see targeted attacks.
Smart Home Botnets Will Grow in Size & Complexity
Future IoT botnets will use:
-
AI traffic masking
-
Peer-to-peer communication
-
Smart-home-to-smart-home propagation
-
Cross-device infection (lights → speakers → router → camera)
Botnet takedowns will be more difficult as devices self-replicate malware and bypass resets.
Smart Home Security Recommendations for 2026–27
To protect households and manufacturers against rising IoT threats, proactive steps must be taken.
Below are detailed action plans for consumers, manufacturers, and security teams.
Recommendations for Consumers
1. Change default passwords immediately
Use strong, unique passwords for every device.
2. Enable 2FA for smart home apps
SMS is acceptable, but app-based MFA is better.
3. Update firmware regularly
Set reminders or enable auto-updates where possible.
4. Create a separate Wi-Fi network for IoT devices
Network segmentation reduces cross-device infection.
5. Disable unnecessary features
Turn off remote access or voice commands if unused.
6. Review app permissions
Do not allow camera, microphone, or location access unnecessarily.
7. Replace unsupported devices
Devices without updates for 12+ months become major risks.
8. Avoid installing random IoT control apps
Only use official apps from recognized vendors.
Recommendations for Manufacturers
1. Enforce Secure-by-Design principles
-
Mandatory password change
-
Strong cryptography
-
Secure onboarding
-
Tamper-resistant firmware
-
Update transparency
2. Provide at least 5 years of security updates
Longer lifecycle support reduces ecosystem risk.
3. Implement encrypted cloud communication
TLS 1.2+ must be mandatory.
4. Secure mobile app + API integrations
Authentication, rate limiting, and encrypted tokens are essential.
5. Provide consumer education
Clear setup guidance reduces misconfiguration risks.
6. Harden supply chain
Eliminate vulnerable SDKs and insecure third-party components.
7. Device identity enforcement
Hardware-based attestation will become a market standard by 2027.
Recommendations for Cybersecurity Teams
1. Include smart home risks in enterprise security policies
Especially for remote employees.
2. Monitor for dark web listings of IoT credentials
Compromised IoT account listings often precede home attacks.
3. Train employees on IoT-specific phishing
Attackers increasingly target smart home apps and cloud accounts.
4. Enforce Zero Trust
No device should be inherently trusted — not even in home environments.
5. Perform IoT penetration testing
Focus on routers, cameras, hubs, and cloud APIs.
6. Mandate secure home Wi-Fi configurations
For executives, force the use of secured networks as part of access policy.
Conclusion: Smart Homes in 2026 Are Convenient — and Critically Vulnerable
Smart home ecosystems continue to grow at an extraordinary pace. With each new device comes increased convenience — but also a wider attack surface. In 2026, smart home breaches expanded sharply due to insecure default configurations, outdated firmware, weak encryption, flawed APIs, malicious apps, and AI-driven exploitation tools.
Security must evolve alongside adoption.
By 2027, smart homes will be:
-
more autonomous
-
more AI-driven
-
more cloud-dependent
-
more interconnected
-
more exposed
But with strong authentication, regular updates, secure configurations, Zero Trust principles, and proactive consumer awareness, smart homes can remain safe and resilient against evolving threats.
The time to secure smart homes is now, before attackers grow even more advanced.
FAQ
1. What percentage of homes use smart devices in 2026?
Approximately 72% of global households use at least one smart home device.
2. What are the most hacked smart home devices?
Cameras, baby monitors, smart locks, voice assistants, TVs, and routers are the most frequently targeted.
3. How common are smart home cyberattacks?
Around 23% of smart homes experienced at least one IoT-related security incident in 2026.
4. What is the biggest vulnerability in smart homes?
Weak passwords, outdated firmware, insecure Wi-Fi, and poorly secured mobile apps.
5. How often are smart home devices updated?
Around 39% of users never update their firmware, leaving devices vulnerable.
6. Can AI hack smart home devices?
Yes. AI-driven tools can mimic voices, exploit weak protocols, scan for vulnerabilities, and automate attacks.
7. Are smart locks safe?
They are safe when configured correctly, but 17% are vulnerable to replay attacks or outdated encryption.
8. What protects smart homes the most?
Proper passwords, MFA, firmware updates, network segmentation, and secure cloud communication.
References
-
Global IoT Adoption & Market Growth Reports (2024–2025)
-
Smart Home Device Vulnerability Assessments (Industry Labs)
-
IoT Malware & Botnet Annual Reviews
-
Global Home Network Security Surveys
-
Mobile App Security & TLS Misconfiguration Reports
-
AI & Cybercrime Trend Forecasts
-
Consumer Behavior Studies (Smart Device Usage)
-
Smart Home Vendor Security Disclosures
-
Regional IoT Regulatory Framework Publications
-
Cybersecurity Industry Annual Threat Landscape Reports
Disclaimer:
The content published on CompareCheapSSL is intended for general informational and educational purposes only. While we strive to keep the information accurate and up to date, we do not guarantee its completeness or reliability. Readers are advised to independently verify details before making any business, financial, or technical decisions.


